Proactive Malicious Domain Search
In a previous diary[1], I presented a dashboard that I’m using to keep track of the DNS traffic on my networks. Tracking malicious domains is useful but what if you could, in a certain way, “predict” the upcoming domains that will be used to host phishing pages? Being a step ahead of the attackers is always good, right? Thanks to the CertStream[2] service (provided by Cali Dog Security), you have access to a real-time certificate transparency log update stream. Briefly, Certificate Transparency[3] helps to protect against threats that make use of bad certificates.
By reading the CertStream feed, it is possible to become aware of newly created or renewed certificates. If the feed can be watched in real-time from the website, it is much more convenient to interface it with another monitoring tool. A classic example is Python. You can easily watch the stream with the Python module 'certstream':
$ pip install certstream $ certstream [INFO:root] 2017-11-22 19:14:49,927 - Connection established to CertStream! Listening for events... [2017-11-22T19:14:40.060376] ct.googleapis.com/pilot - 99designsolution.com [2017-11-22T19:14:40.066228] ct.googleapis.com/pilot - sni52607.cloudflaressl.com [2017-11-22T19:14:40.071942] ct.googleapis.com/pilot - 98entrepreneurs.com [2017-11-22T19:14:40.077284] ct.googleapis.com/pilot - sni52607.cloudflaressl.com [2017-11-22T19:14:40.082900] ct.googleapis.com/pilot - 99people.com [2017-11-22T19:14:40.086780] ct.googleapis.com/pilot - www.9980t.com [2017-11-22T19:14:40.090466] ct.googleapis.com/pilot - 98wellstreet-brighton.com [2017-11-22T19:14:40.094337] ct.googleapis.com/pilot - 8bitcyclops.com [2017-11-22T19:14:40.097591] ct.googleapis.com/pilot - 9barrecordings.com ^C
You will immediately see that the raw feed is completely useless due to the huge amount of operations on certificates performed by seconds. How to detect only “useful” domains? I found on GitHub an interesting project based on same feed: phishing_catcher[4]. The purpose is the same as the official 'certstream' command but domain names are checked against different criteria to help in computing a score to estimate if the domain is suspicious or not. Some examples:
| Found String | Weight |
|---|---|
| "account" | +25 |
| "outlook" | +60 |
| ".net-" | +20 |
It also checks for a list of suspicious new TLD’s like .party, .cc, .top, .tech, etc.
Note that a weight of +10 is added if the certificate has been issued by Let’s Encrypt!
The final score is flagged as follow:
| >= 65 | Potential |
| >= 80 | Likely |
| >= 90 | Suspicious |
Let’s have a look at some domains that I tested yesterday:
panel.com-review-client9983.info:

http://appleid.unlocked-cloud.com:
It is also possible to detect upcoming campaigns based on similar domains that have their certificate created or renewed in a short period of time:
appleid.apple.com.appsecure.software www.appleid.apple.com.appsecure.software appleid.apple.com.appdatasecure.report www.appleid.apple.com.appdatasecure.report www.appleid.apple.com.appsecure.site appleid.apple.com.checkdata.report www.appleid.apple.com.checkdata.report appleid.apple.com.checkdata.site www.appleid.apple.com.checkdata.site appleid.apple.com.datacheck.site www.appleid.apple.com.datacheck.site
Ok, how to use it in a simple but effective way? Phishing_catcher can be quickly installed in a Docker container:
FROM ubuntu:latest MAINTAINER Xavier Mertens <[email protected]> RUN apt-get update && \ apt-get install -y git python3-pip python3-selenium chromium-chromedriver python3-pil && \ rm -rf /var/lib/apt/lists/* WORKDIR /opt RUN git clone https://github.com/x0rz/phishing_catcher.git WORKDIR /opt/phishing_catcher RUN pip3 install -r requirements.txt WORKDIR /opt/phishing_catcher ENTRYPOINT ["python3", "./catch_phishing.py”]
If you’re a big organization which is often targeted with phishing kits, I recommend you to modify the 'suspicious.py' file and add your own domains and/or keywords!
The final step is of course to use the list of domains (ex: the last 5000 entries or captured for the last x hours and correlated with your logs:
index=securityonion source="/nsm/bro/spool/manager/dns.log" [|inputlookup phishing_catcher.csv] | stats count by qclass,src_ip | table src_ip,qclass, count | sort 10 -count
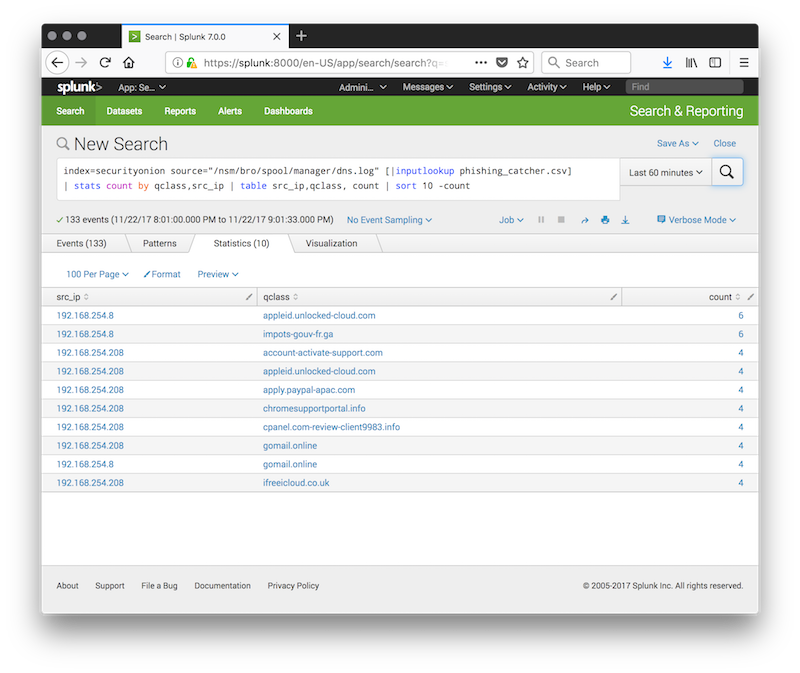
Happy hunting!
[1] https://isc.sans.edu/forums/diary/Suspicious+Domains+Tracking+Dashboard/23046/
[2] https://certstream.calidog.io/
[3] https://www.certificate-transparency.org/what-is-ct
[4] https://github.com/x0rz/phishing_catcher
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments