Sometimes it's just SPAM
A reader forwarded us a suspicious email. It contained a URL, and I downloaded the content with a method similar to what Lenny explained in this diary entry.
Here is the content of the html page:
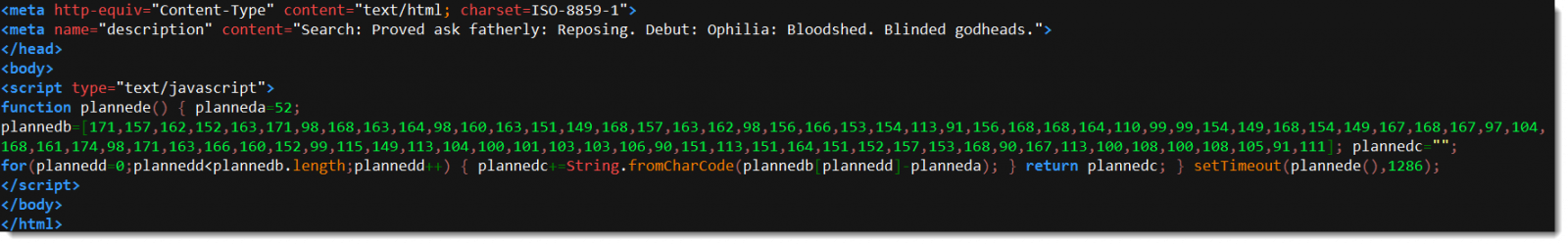
There are several methods to deobfuscate the data in this script. If you take a close look, you will notice that each number in array plannedb is subtracted with 52 (planneda) and then converted to characters.
As I often have to do such decodings, I have a tool for this: numbers-to-string.py
It can easily be used to decode the script:
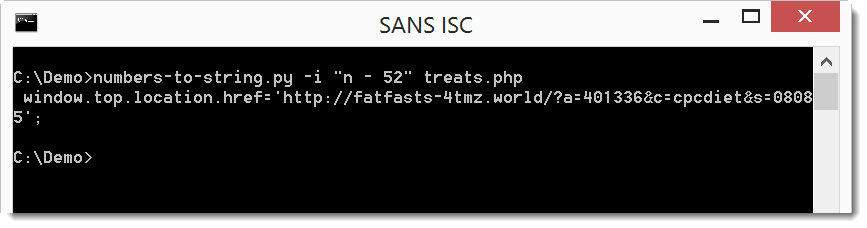
Retrieving this URL reveals that this is actually a SPAM email, there is no malicious code.
I've seen before that spammers and advertisers use code obfuscation techniques similar to malware authors. Even legitimate web developers do it occasionaly to try to protect their code from being copied and reused.
Didier Stevens
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments