Hancitor/Pony/Vawtrak malspam
Introduction
Until recently, I hadn't personally seen much malicious spam (malspam) using Microsoft office documents with Hancitor-based Visual Basic (VB) macros to send Pony and Vawtrak. It still happens, though. Occasionally, I'll find a report like this one from 2016-12-19, where Hancitor/Pony/Vawtrak malspam was disguised as a LogMeIn account notification, but I rarely come across an example on my own. And apparently, there's been a recent lull in Hancitor/Pony/Vawtrak malspam until yesterday.
This diary describes a wave of Hancitor/Pony/Vawtrak malspam from Tuesday 2017-01-10.
The malspam
The example I saw was a fake parking ticket notification.
- Date/Time: Tuesday, 2017-01-10 20:25:41 UTC
- Received from: kennedyslaw.com
- Message-Id: [email protected]
- From: [email protected]
- Subject: RE: RE: parking ticket
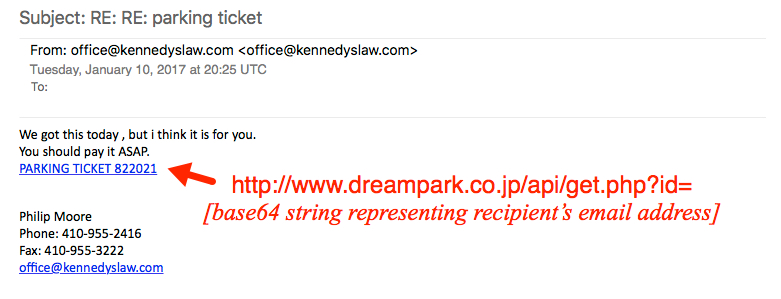
Shown above: The fake parking ticket notification with a link to a Word document.
The link from the malspam downloaded a Microsoft Word document. The document contains a malicious VB macro described has Hancitor, Chanitor or Tordal. I generally call it Hancitor. If you enable macros, the document retrieves a Pony downloader DLL. The Pony downloader then retrieves and installs Vawtrak malware.

Show above: Flow chart of the infection process.
The link from the email contains a base64-encoded string representing the recipient's email address. Based on that string, the downloaded file will have the recipient's name from the email address. I used a base64 string for [email protected] (a made-up name/address) and received a file named parking_bert.doc.
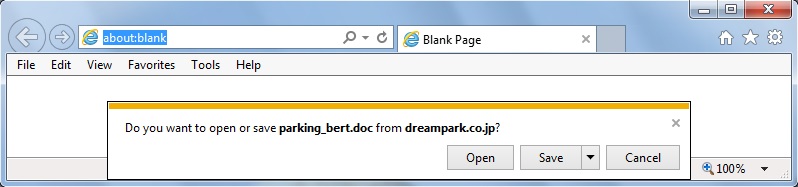
Shown above: Retrieving the Hancitor Word document from the email link.
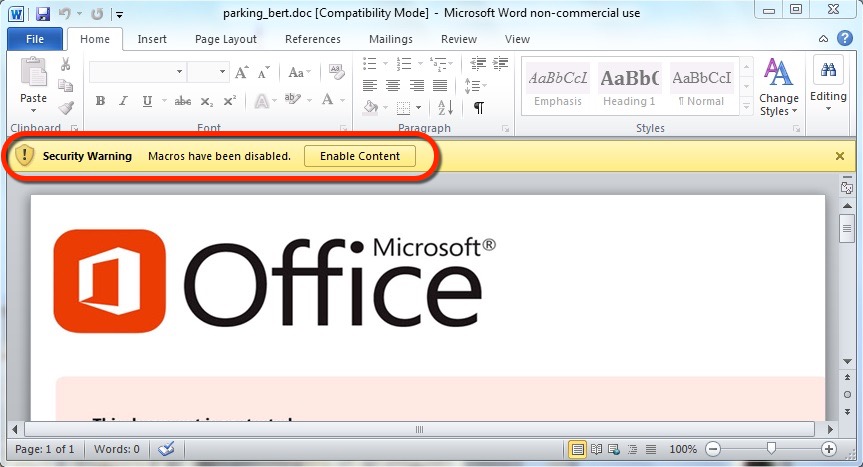
Shown above: Enabling macros will activate Hancitor.
The traffic
Pattern-wise, URLs from this infection are similar to previous cases of Hancitor/Pony/Vawtrak malspam reported during the past two or three months.
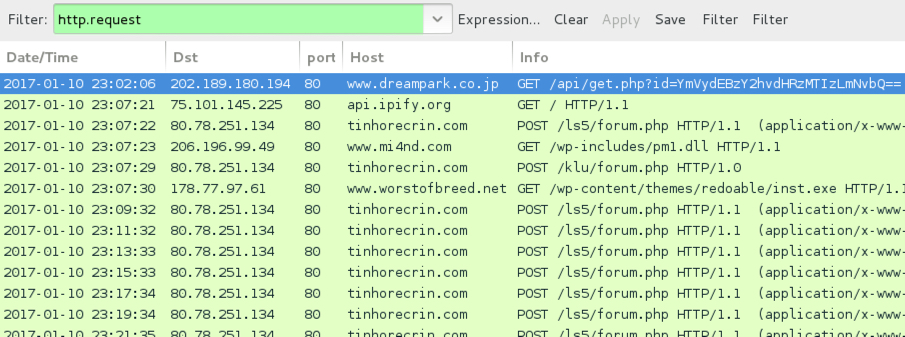
Shown above: Infection traffic after activating macros in the Word document.
You won't see any Vawtrak-specific activity until you start your browser and try to look at a something. Once you do, you'll see Vawtrak callback traffic.
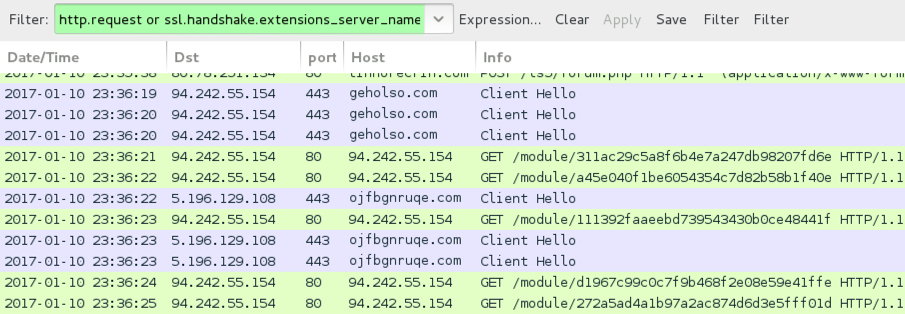
Shown above: Vawtrak callback traffic seen only after trying to browse the web.

Shown above: Alerts on the traffic using Security Onion with Suricata and the ETPRO ruleset.
Indicators of Compromise (IOCs)
Email links noted on Tuesday 2017-01-10 to download the Hancitor Word document:
- 202.189.180.194 port 80 - www.dreampark.co.jp - GET /api/get.php?id=[base64 string]
- 123.30.182.73 port 80 - www.thienyhotel.vn - GET /api/get.php?id=[base64 string]
Traffic after enabling macros on the Word document:
- api.ipify.org - GET / [IP address check]
- 80.78.251.134 port 80 - tinhorecrin.com - POST /ls5/forum.php [Hancitor callback]
- 80.78.251.134 port 80 - tinhorecrin.com - POST /klu/forum.php [Hancitor callback]
- 80.78.251.134 port 80 - tinhorecrin.com - POST /borjomi/gate.php [Hancitor callback]
- 206.196.99.49 port 80 - www.mi4nd.com - GET /wp-includes/pm1.dll [DLL for Pony]
- 206.196.99.49 port 80 - www.mi4nd.com - GET /wp-includes/pm2.dll [DLL for Pony]
- 178.77.97.61 port 80 - www.worstofbreed.net - GET /wp-content/themes/redoable/inst.exe [EXE for Vawtrak]
Vawtrak traffic noted after trying to browse the web:
- 94.242.55.154 port 80 - 94.242.55.154 - HTTP post-infection Vawtrak callback
- 94.242.55.154 port 443 - geholso.com - HTTPS/SSL/TLS post-infection Vawtrak callback
- 5.196.129.108 port 443 - ojfbgnruqe.com - HTTPS/SSL/TLS post-infection Vawtrak callback
Associated file hashes:
- SHA256 hash: ccf2700ac1878b47ff99bbef8074ccdc0a6dd53ebce8b7aadc00f8d31e78ff43
- File size: 200,192 bytes
- Description: Word document from link to dreampark.co.jp
- SHA256 hash: ad89a7ca5869cb6ea153be32740e6fe4c2fae06383c4680560cc3dd861c2a77a
- File size: 188,416 bytes
- Description: Word document from link to thienyhotel.vn
- SHA256 hash: c726abc766688a680a7c4edd519998ccd436149f907cb5bc0df16137b60e73a2
- File size: 71,680 bytes
- Description: Pony downloader (DLL stored in memory)
- SHA256 hash: 71f601df5d547be70e75bc7acd10f437d4438a7fc7d66b111607fe64d1d8ce41
- File size: 389,120 bytes
- Description: Vawtrak malware
Final words
Speaking as a security professional, we often become jaded as yet another wave of malspam does the same thing it's done before. Patterns behind such activity are often well-documented. So why bother with discussion, if there's nothing new? Why bother talking about it, when we have the technical means to prevent these types of infections?
Why indeed! That attitude only encourages the criminal groups behind malspam. For various reasons, many environments don't follow best security practices, and they're still vulnerable. If we discuss on-going waves of malspam in high-visibility forums like this one, more people will be aware of the threat.
I encourage security professionals to routinely check sites like blog.dynamoo.com, myonlinesecurity.co.uk, and techhelplist.com. Many folks also have Twitter channels with even more timely updates.
If you know any blogs or Twitter channels you find helpful, feel free to leave a comment below. Let's keep the discussion going!
Pcap and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments