Ongoing Scans Below the Radar
With the rise of botnets like Mirai[1], we have seen a huge increase of port scans to find new open ports like port 2323 or later port 6789. If the classic port 80 and port 23 remain the most scanned ports, we see new trends almost every week. By the way, thank you to our readers who also report this to the ISC!
This is the traffic detected by my current honeypots:
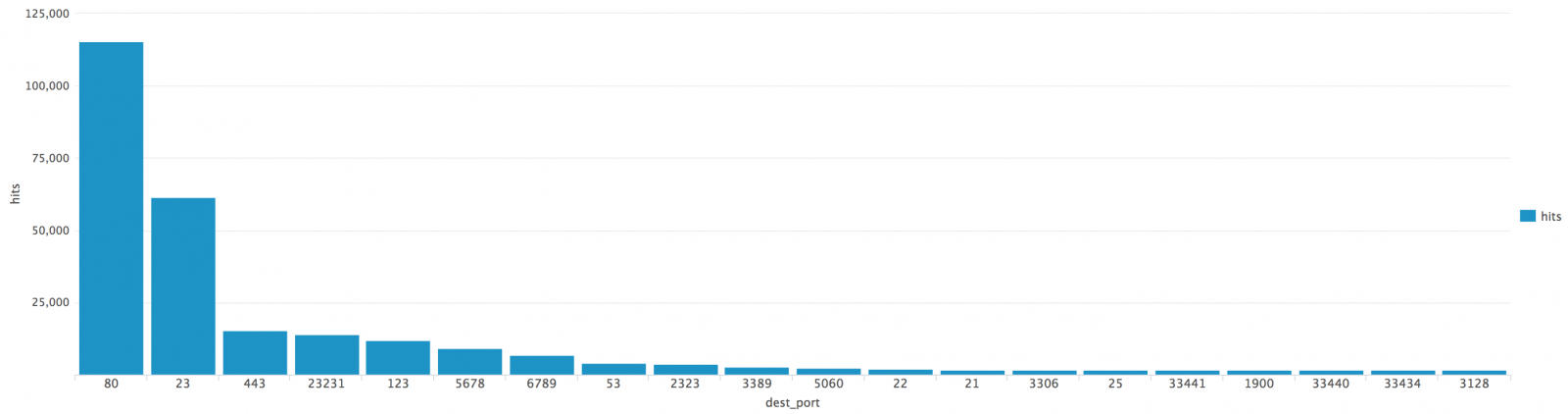
The honeypots accept connections on ports 80 and 443 and just log attempts performed on other ports.
A few days ago, I deployed a new honeypot that listens to many more ports:
- 21 (FTP)
- 22 (SSH)
- 69 (TFTP)
- 80 (HTTP)
- 123 (NTP)
- 161 (SNMP)
- 445 (SMB)
- 1433 (MSSQL)
- 3389 (RDP)
- 5060 (SIP)
- 5900 (VNC)
- 8080 (Proxy)
For each protocol, the honeypot collects interesting information related to the application (user, password, commands, filename, path, ...) It has been deployed on a brand new system that was unknown before. Here are some results after one week online:
| Protocol | Hits |
| 21 | 1 |
| 3389 | 2 |
| 80 | 3 |
| 69 | 9 |
| 161 | 35 |
| 123 | 82 |
| 5060 | 234 |
| 3306 | 3097 |
| 1433 | 4897 |
| 23 | 41857 |
As you can see databases seems to remain a nice target. The MSSQL scans revealed the following users:
| Chred1433 |
| IIS |
| KISAdmin |
| kisadmin |
| sa |
| su |
| vice |
With MySQL, the targeted users were:
| mysql |
| root |
| server |
The NTP scanners issued the "monlist" command to search for NTP servers vulnerable to amplification attacks.
As you can see, there are bots scanning for many protocols. We need to keep an eye on what is happening below the radar. I'm planning to listen to more ports in the coming days. I wish you already a wonderful and safe year 2017!
[1] https://isc.sans.edu/forums/diary/What+is+happening+on+2323TCP/21563
[2] https://www.us-cert.gov/ncas/alerts/TA14-013A
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments