More on Protocol 47 denys
Following up on yesterday's diary on an increase in Protocol 47 traffic. Thanks to everyone who sent the ISC PCAPs and more information.
Current speculation is the Protocol 47 uptick is backscatter from a DDOS containing GRE traffic and using random source IPs.
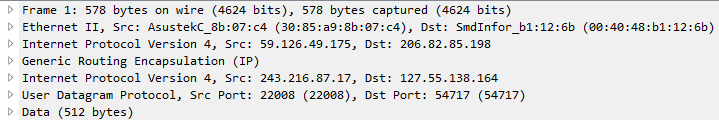
While all of the packets appear to be IPv4 packets encapsulated in GRE, there are two flavors of packets involved. The smaller packets are consistently 66 bytes long and contain no data.
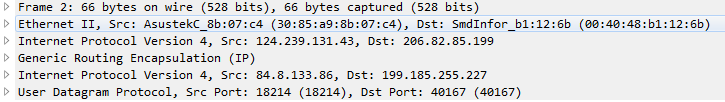
The larger packets vary in size, but are typically in the high 500's of bytes and contain 512 bytes of data. The data appears to be random.
While the sources show IPs from over 50 countries, about 55% of the source IPs in my data were from Taiwan, presumably these IPs are the primary attack targets.
Top 10 Sources by Country
| Country | % |
| Taiwan | 55.10% |
| United States | 9.17% |
| Brazil | 4.85% |
| Israel | 3.22% |
| Romania | 2.66% |
| Mexico | 2.57% |
| Bulgaria | 2.33% |
| Spain | 2.19% |
| Uruguay | 2.01% |
| China | 1.89% |
The majority of those were from IPs associated with Chungwa Telecom (HINET-NET), the largest ISP/Carrier in Taiwan.
Top 20 Sources by IP
| source_address | Country | |
| 61.216.174.203 | Taiwan | HINET-NET |
| 220.128.119.155 | Taiwan | HINET-NET |
| 118.150.129.110 | Taiwan | CHIEF-AS-AP |
| 108.34.140.241 | USA | VIS-BLOCK |
| 122.116.118.57 | Taiwan | HINET-NET |
| 77.238.70.76 | Bulgaria | FIBER1BG |
| 59.125.241.196 | Taiwan | HINET-NET |
| 79.121.32.210 | Hungary | VIDANET-AS |
| 59.126.160.210 | Taiwan | HINET-NET |
| 114.34.6.239 | Taiwan | HINET-NET |
| 143.208.145.62 | Brazil | Duarte & Dias Eletroeletronicos Ltda ME |
| 1.34.143.67 | Taiwan | HINET-NET |
| 125.227.61.121 | Taiwan | HINET-NET |
| 191.243.115.113 | Brazil | Nettel Telecomunicações Ltda |
| 182.155.224.35 | Taiwan | VEETIME-TW-AP |
| 91.213.187.157 | Ukraine | BIOSCOMP-AS |
| 175.182.238.168 | Taiwan | SEEDNET |
| 61.63.178.186 | Taiwan | SAVECOM-TW |
| 95.42.116.59 | Bulgaria | BTC-AS BULGARIA |
| 24.249.56.149 | USA | ASN-CXA-ALL-CCI-22773-RDC |
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
Increase in Protocol 47 denys
ISC reader Scott has indicated that starting on December 27th he has seen a significant increase in Protocol 47 traffic being denied by his firewalls. He has seen this traffic increasing from a baseline of near zero to 20,000 to 50,000 denies per day. Protocol 47 traffic is not normally tracked by the ISC, so none of our sensors had detected this uptick. However a little investigation reveals that firewalls I have access to are also seeing this increase.

Protocol 47 is “GRE” (Generic Route Encapsulation) . It is commonly used as a Virtual Private Network (VPN). Essentially, GRE can be used to encapsulate any other protocol over IPv4. Sometimes it is used for IPv6 tunneling (instead of the more common IPv6 over IPv4, Protocol 41), and some anti-DDoS mitigation systems use it to route “cleaned” traffic.
I am showing this traffic originating from more than 100 unique sources. I would like to dig deeper into this, but unfortunately I don't have access to packet captures to take a closer look at the traffic. If you could let us know whether you are seeing the same thing, or better yet, have access to captures of this traffic, and could share it with us, it would be appreciated.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments