Mirai - now with DGA
Shortly after Mirai was attributed to massive DDOS on OVH and Brian Krebs the source code for Mirai was released on Github. This was a double edged sword. It gave security researchers insight into the code, but it also made it more available to those who may want to use it for nefarious purposes. Within days Mirai variants were detected. Now chinese researchers Network Security Research Labs are reporting that recent samples of Mirai have a domain generation algorithm (DGA) feature. The DGA is somewhat limited in that it will only generate one domain per day, so a total of 365 total domains are possible and they are all in the .tech or .support TLDs. Further investigation reveals that some of these possible domains have already been registered, presumably by the Mirai variant author.
A few of the domains were in the past, but a number are coming up in the next couple of weeks.
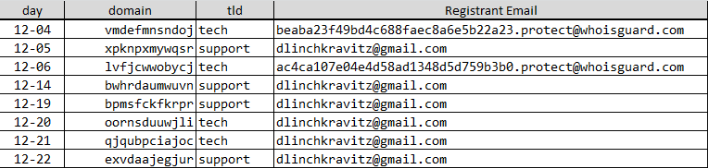
Definitely something to have your Intrusion Detection and DNS sensors watch for.
The detailed analysis of the malware sample is a fun read...if you are into such things.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments