In Need of a OTP Manager Soon?
Even if everybody agrees to say that passwords are a weak way to protect access to sensitive or private information, they remain still today the default method implemented by many online services. A password, as complex as it may be, is easy to steal or leak. Tools like Mimikatz or memory scrappers[1] are common today. For a while, major players on the Internet started to implement two-factors authentication (2FA) or multi-factors authentication (MFA). Just to remind you, this authentication mechanism is based on a combination of:
- something "you know" (a password, a PIN or pass phrase)
- something "you have" (a token, a smart card)
- something "you are" (your fingerprint, retina, hand palm, …)
From a cost and ease of implementation point of view, the most common combination remains a password and a temporary code or "OTP". They are commercial solutions based on physical tokens but today with the explosion of smartphones, the Google Authenticator[2] and compatible applications became the most used platform. Once the application is installed, every time you activate the OTP feature on a compatible website, you scan a QR code and that’s it!
An alternative way (not available on all sites) is to use the Base32 or HEX key like on the ISC website:
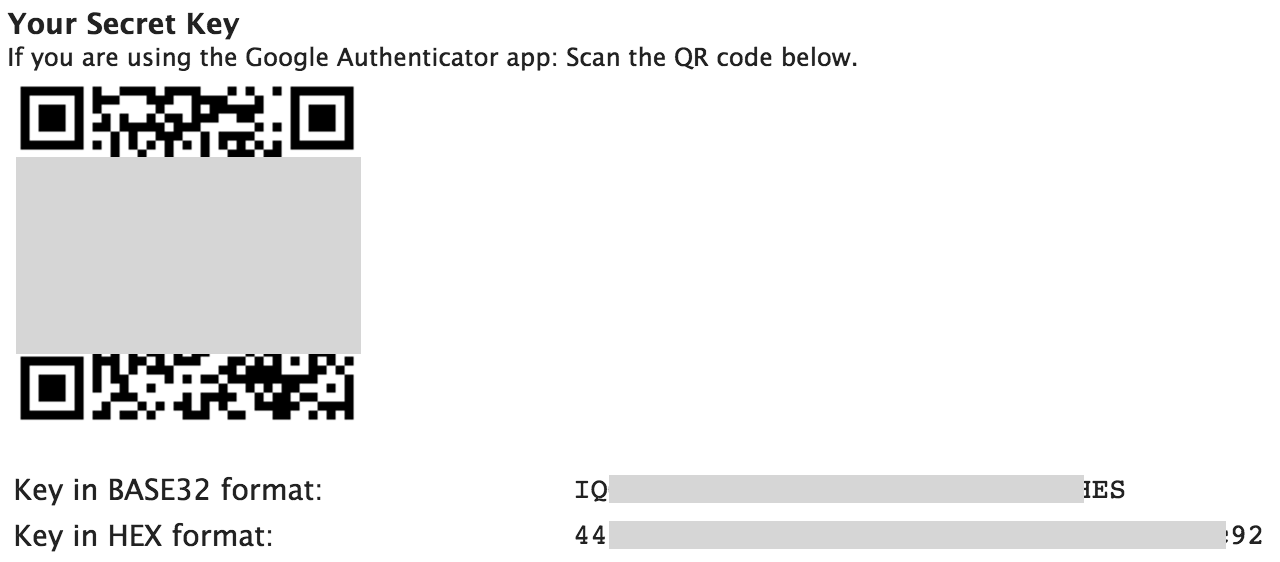
When available, I always enable OTP on my online accounts (Twitter, Github, Apple, Dropbox, … but also on my own resources like my blog or my private ownCloud). On my iPhone, I’m using the 2FA app because it has a simple GUI and it provides an Apple watch version (It is so convenient to have tokens just on your wrist!). But my collection of tokens is constantly growing:
I can’t imagine losing all those tokens! We use password managers for a while (well, I hope you do) but will we need a “OTP Manager” soon? The other question is: How to safely keep track and backup your tokens? They are available in your pocket but a smartphone is easy to loose, to be stolen or broken. Most websites propose a procedure to recover your access if you lost your token but there isn't a unique procedure: Some propose recovery codes (that must also be safely stored somewhere), emails or SMS code (and, guess what, usually the same phone is used to receive the recovery SMS).
Here are some best practices:
- Always read carefully the recovery procedure
- Copy / print backup codes
- Link your account to a mobile phone (to receive SMS)
- Link your account to a valid and rock-solid email address (not the one provided by your employer)
Personally, what I do:
- When the QR code is displayed on the website, I take a screenshot of the code and rename the picture QR_websitename_
.png When the Base32 or HEX key is provided, I write them in a text file KEY_websitename.txt Files are zipped, encrypted with my PGP key and stored offline Link the account to a different SIM / phone number that can be used in any old-fashioned phone
Note that some 2FA apps, like Authy, propose a backup solution (usually in the cloud - it's up to you to trust it or not). To conclude, OTP passwords are a good way to protect your accounts but have a good recovery procedure to avoid losing control of your accounts. And you? What how to you address this issue? Share your input!
[1] https://blog.blechschmidt.saarland/memory-recovery/
[2] https://support.google.com/accounts/answer/1066447
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
Is "2 out of 3" good enough for Anti-Malware?
One of my morning rituals is to take the last few malware samples I received in any of my inboxes and run them in a virtual machine to see if there is anything new. To be honest: There isn't much new that we haven't already written about. The sample is usually a zipped VBScript file that will download and run ransomware. But that isn't the only constant. The other constant is the inability of anti-malware to protect your system from these consistent attacks.
The virtual machine runs a fully patched Windows 10 install, and home-user grade anti-malware. I would consider it a "well configured" average home user system.
This morning, for example, I tried these three samples:
924936fb9f562dc08556bf0677a5d15c813eebde SCAN_20160915_241418570.zip
c29dd0d1fe36b3891d685171683635c442d84c8d SCAN_20160915_3640961765775.zip
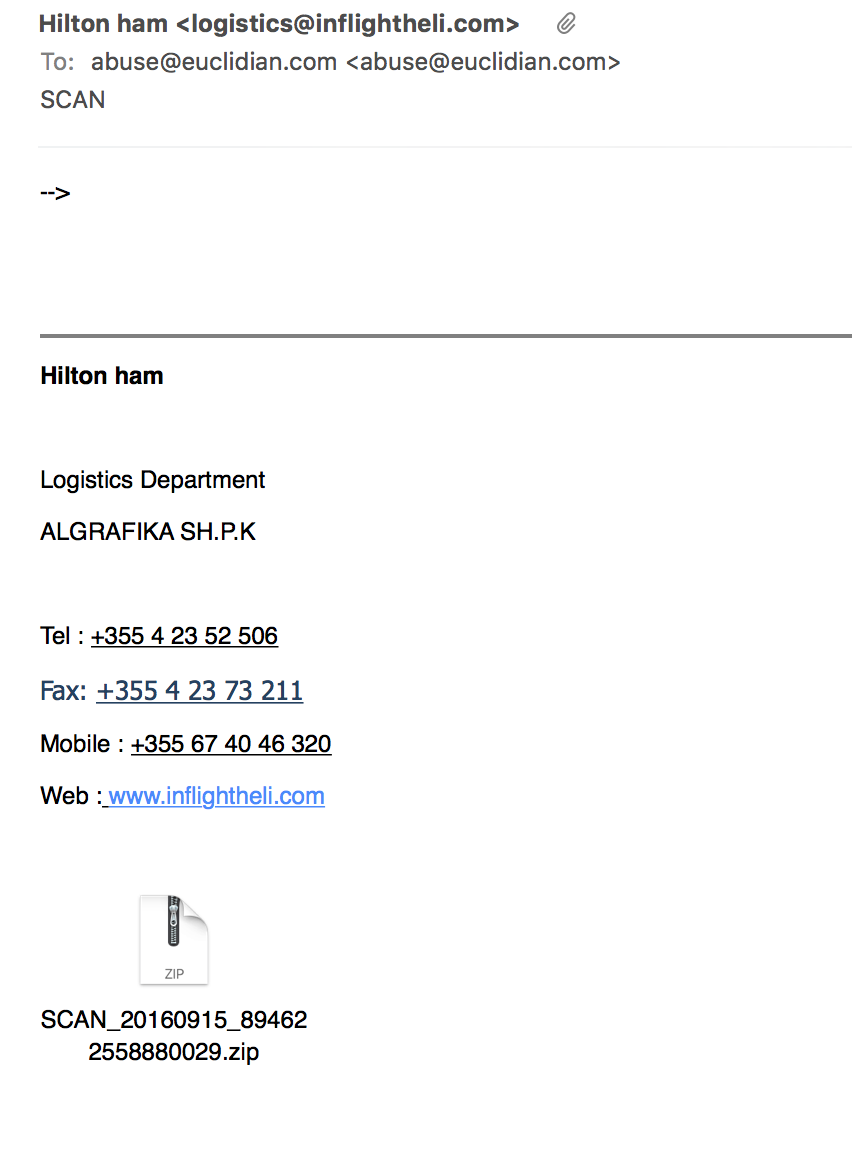
6213e371567b4620064933efa43e5ffdba455c65 SCAN_20160915_894622558880029.zip
They all arrived in similar emails with a subject of "SCAN" .
If you are paying attention of malware, you probably have seen e-mails like this for years with various attachments.
Two of these samples were nicely detected by my anti-malware solution, and I wasn't even able to copy them to my virtual machine. But the third one, which isn't substantially different, made it past whatever signature was used to detect these generic JavaScript downloaders.
Virustotal shows that some name-brand anti-malware solutions do not detect this particular sample:
https://www.virustotal.com/en/file/8acb71453b9759a64eea060949ad87bae3d6f070b04daf2f70ed124b1a905399/analysis/
https://www.virustotal.com/en/file/f732887b200563bfdd89f516fc30139ea21e8adbd3280df3436c289bc154383a/analysis/
https://www.virustotal.com/en/file/a9b4a38e515ee10e1dc8eda13ac9abd8c11c0eece4ac1cb1c746015d17ff5a0c/analysis/
It also shows that all of these samples were rather "fresh" in that Virustotal had received them about 30 minutes ago, so around the time I had received them.
Even if your anti-malware solution doesn't detect the downloader, there is still a chance that it will detect the malware that is downloaded by the JavaScript. This often leads to a false sense of security in that you will see, often multiple times, popups that your anti-malware solution did remove malicious code from your system. But these downloaders can be rather persistent. One sample I looked at yesterday took about 15 minutes, and about a dozen of "malware found" popups, until it finally downloaded a version of Locky that was not detected, and I ended up with another encrypted system.
So what can you do?
- The less malware reaches the user, the better. Filter as much on mail servers and proxies as you can using generic filters ("zipped VBscripts" and the list. We talked about this before).
- Once you notice a possible infection, NEVER trust anti-malware to clean your system. It is probably best to shut down the system as soon as you notice "malware found" popups. This way, you MAY prevent the final successful install, and you may be able to save some of your files from being encrypted.
- Just like you should not rely on anti-malware: Blocklists of bad URLs and the like are just as bad (ours included). They will help you in hindsight to figure out who got infected yesterday (or an hour ago if they are good), but they will not consistently prevent exploitation.
For example, here are the URLs that I think where used in the undetected sample (I didn't do a full analysis):
(spaces added to protect readers.)
bigfishcasting .com/ afdIJGY8766gyu?YJRTHAigKa=sLUfGQkQRhO
delicefilm .com /afdIJGY8766gyu?YJRTHAigKa=sLUfGQkQRhO (this one has some reasonable recognition as a bad URL)
keratin .sk/ afdIJGY8766gyu?YJRTHAigKa=sLUfGQkQRhO
The issue with anti-malware missing the downloader, and then hoping that the downloaded malware will be detected, isn't new, and going back at least to the famous "WMF" incident more than 10 years ago, when anti-virus was suggested as a mitigation for the vulnerability, even though it didn't detect actual exploitation of the vulnerability but instead only the additional malware downloaded via the exploit. 10+ years later... not much changed. We are still making it too easy for the bad guys.


Comments