Tracking Privileged Accounts in Windows Environments
While speaking with a customer, he complained about the huge number of privileged users having domain admin rights in his network. It seems to be a recurrent problem for him: The security team reviews all the users at a time t and it reduces the number of privileged accounts to the strict minimum. But quickly, the number of administrators is growing again and, at time t+x, they have to restart the cleaning process. Amongst the SANS 20 Critical Security Controls, the point #12 focuses on controlling administrative privileges. The following controls are already in place by the customer:
- Auditing privileged accounts usage
- Auditing privileged accounts changes (creation, removal)
- Strong password policy
Unfortunately, the control #7 (CSC 12-7) remains a pain: the utilization of privileged accounts for non-administration tasks like reading e-mails or surfing the web. As most of the controls remains technical, a suggestion was to add a extra layer of awareness for administrators to remind them that using privileged accounts can be dangerous. Instead of simply displaying a warning message, the idea was to force the administrator to describe (log) in a few words why he started an administrator session. The information is logged and can be used later to generate activity reports from their SIEM like this example:
| Timestamp | Host | User | Reasons of the session |
|---|---|---|---|
| 2015-09-12 17:23:00 | ServerA | a-user1 | Installed patch MS-15-xxx |
| 2015-09-14 09:43:12 | DC1 | administrator | Installed agent from xxxx |
| 2015-09-15 12:16:34 | SQL-2 | a-user2 | Emergency reboot |
Not valid, funny or empty reasons can we investigated case by case improving the control of privileged users.
There are commercial solutions which implement this like Cyber-Ark or Digital Guardian. I wrote a PowerShell script which can be deployed as a logon script. Details are available on my blog.
Xavier Mertens
ISC Handler - Freelance Security Consultant
rootshell.be
truesec.be
Using testssl.sh
Testssl project has announced the release of testssl 2.6. testssl.sh is a free command line tool which checks a server's service on any port for the support of TLS/SSL ciphers, protocols as well as recent cryptographic flaws.
Here is some examples of how to use testssl.sh:
First you have to download the script from:
Running the script without any option will run all the tests:
testssl.sh google.com
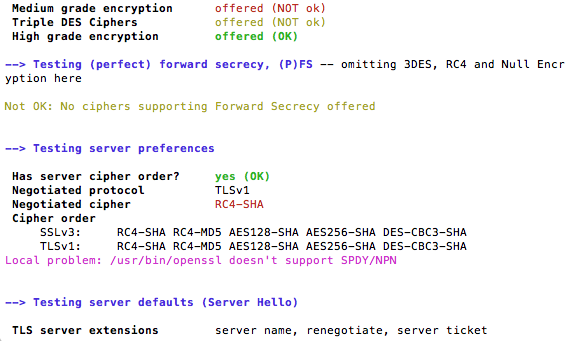
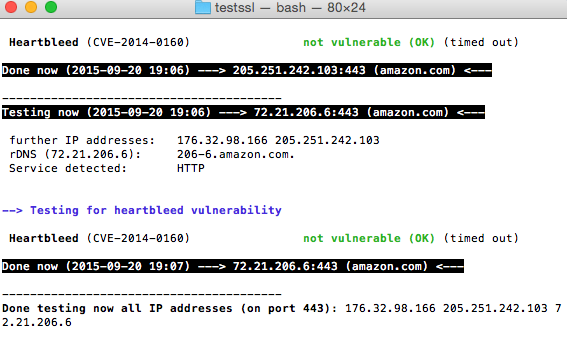
If you like to check for a specific vulnerability such as heartbleed you can run the following option
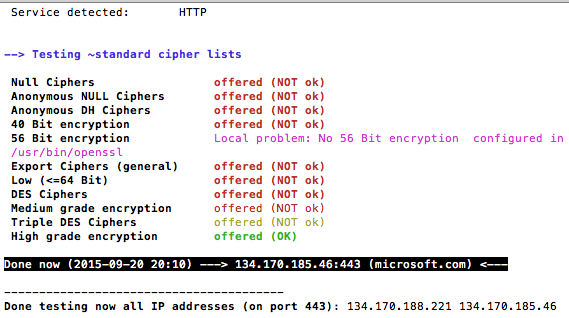
To check the supported ciphers suites you can use the –f option:
./testssl.sh –f Microsoft.com
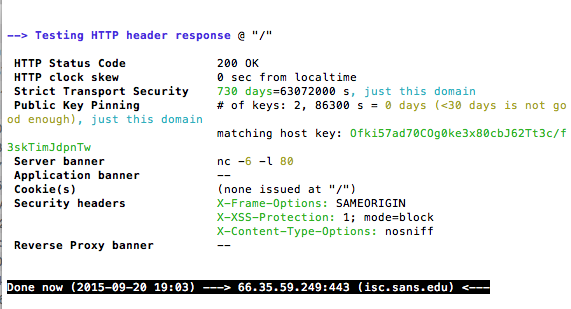
Another neat option is –H which will give you some information about the http header and it will mark the security features
./testssl.sh –H isc.sans.edu


Comments