Botnet-based malicious spam seen this week
Introduction
Botnets continually send out malicious spam (malspam). As mentioned in previous diaries, we see botnet-based malspam delivering Dridex and Dyre malware almost every day [1, 2]. Recently, someone sent us a malicious Word document from what appeared to be Dridex malspam on Tuesday 2015-06-16. (Thanks, Wayne... You know who you are!) Unfortunately, while investigating the malware, I could not generate the full range of infection traffic. Otherwise, the traffic follows the same general patterns we've previously seen with Dridex [1].
Examples of the malspam
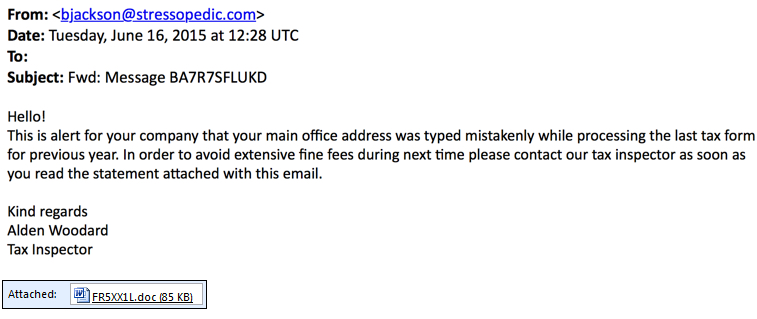
Dridex has been using Microsoft Word documents and Excel spreadsheets designed to infect a computer if macros are enabled, which matches the infection vector used by this malspam. Shown below are two examples of the malspam from Tuesday 2015-06-16. Both examples claim the recipient has made an error in tax forms. This wave of malspam used a Word document for the malicious attachment. As seen before with botnet-based malspam, the emails have different senders, subject lines, attachment names, and message text. Due to these many differences, people usually have a hard time blocking it from their mail servers.
Examples of the Word documents
The image below shows an example of a Word document sent on 2015-06-16. File names consist of random characters. Random characters are also seen in the "Authors" and "Last saved by" fields.
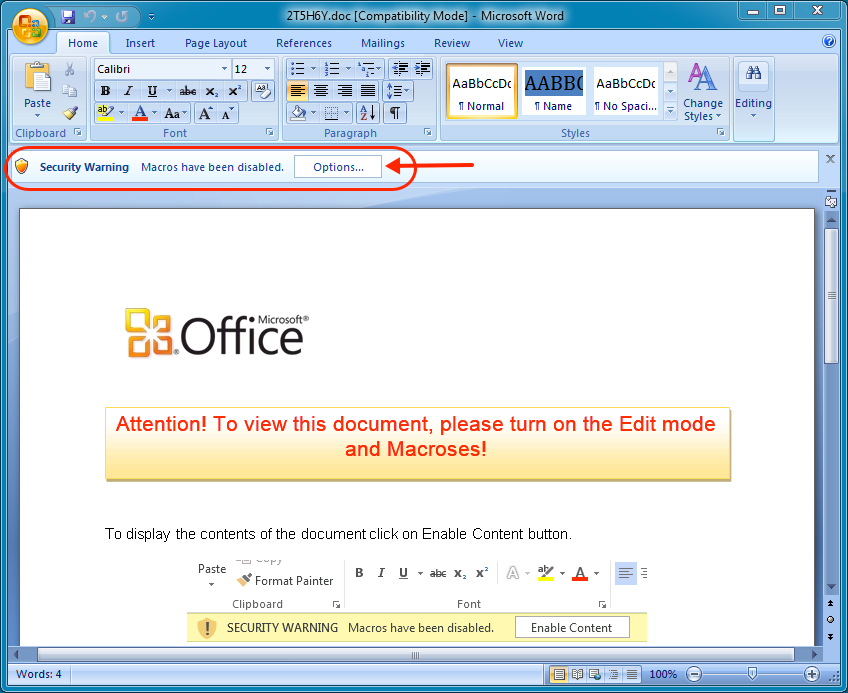
Macros are not enabled in the default installation for Microsoft Office. To infect a computer, most people will have to enable macros after the document is opened, as shown below.
Traffic
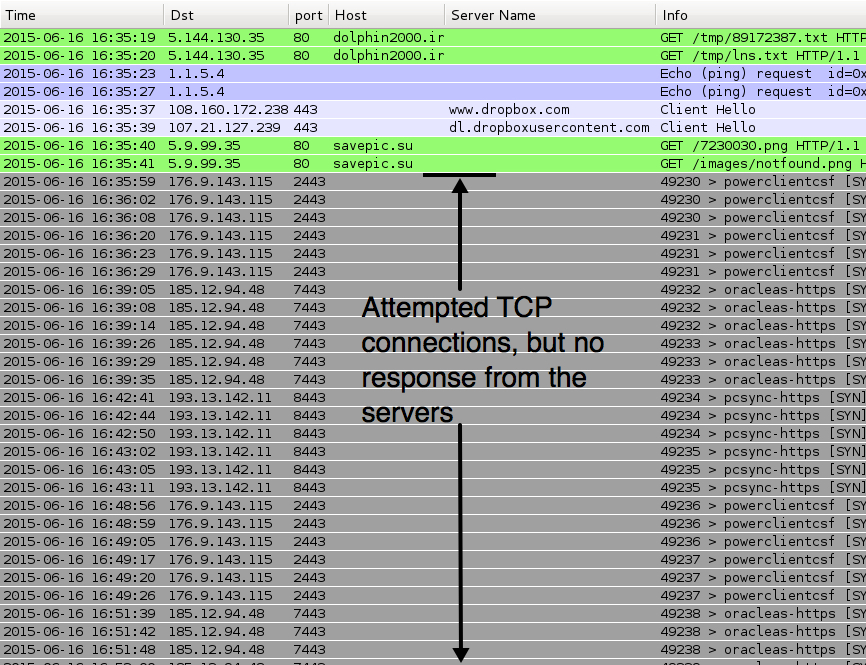
Below is a screenshot of Wireshark displaying traffic seen from an infected host.
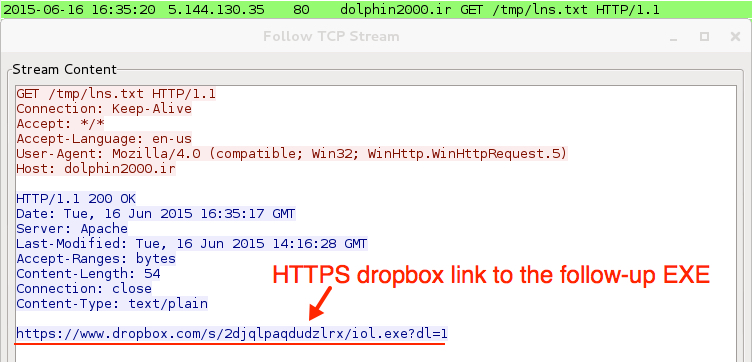
Traffic seems typical of Dridex we've seen the past couple of months. Last month, the follow-up executable was retrieved from a pastebin.com URL over HTTP. This time, the follow-up executable was retrieved from a dropbox.com URL using HTTPS.
The attempted TCP connections shown below would normally result in SSL traffic, but the servers did not respond. That's probably an issue for this particular sample or possibly my environment's connection to the Internet.
- 5.144.130.35 port 80 - dolphin2000.ir - GET /tmp/89172387.txt
- 5.144.130.35 port 80 - dolphin2000.ir - GET /tmp/lns.txt
- 1.1.5.4 - Echo (ping) request
- www.dropbox.com - GET /s/2djqlpaqdudzlrx/iol.exe?dl=1 (https)
- 5.9.99.35 port 80 - savepic.su - GET /7230030.png
- 5.9.99.35 port 80 - savepic.su - GET /images/notfound.png
- 176.9.143.115 port 2443 - attempted TCP connection
- 185.12.94.48 port 7443 - attempted TCP connection
- 193.13.142.11 port 8443 - attempted TCP connection
- 176.9.143.115 port 2443 - attempted TCP connection
- 185.12.94.48 port 7443 - attempted TCP connection
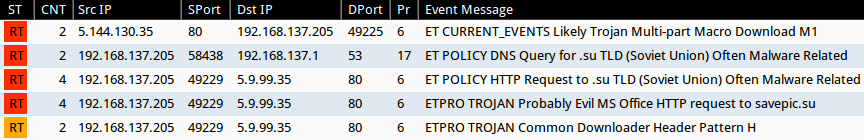
Reviewing the traffic in Security Onion using the Emerging Threats and ET PRO signature sets shows a few Snort events, as shown in the image below. There's nothing Dridex-specific in the events, and I've seen savepic.su used before with malspam using Chanitor to send Vawtrak [3, 4]. At first, I wasn't certain this was Dridex, but the VirusTotal entry for the downloaded EXE indicates this is probably Dridex [5].
Malware
The following artifacts were retrieved from the infected Windows host:
- C:\Users\username\AppData\Local\Temp\21807.bat
- C:\Users\username\AppData\Local\Temp\21807.ps1
- C:\Users\username\AppData\Local\Temp\21807.vbs
- C:\Users\username\AppData\Local\Temp\8.exe
- C:\Users\username\AppData\Local\Temp\444.jpg
The file 8.exe is an executable that deletes itself shortly after it is executed.
Final words
Botnet-based malspam is something we see almost every day. A quick Google search on Dridex returns several articles with good insight into this malware. However, traffic from Dridex and other botnets continually evolve. What's current one week could be out-of-date the next.
If you run across any interesting malspam, feel free to use our contact form and send us a copy. We might not be able to investigate all submissions; however, we're always interested in the samples.
Traffic and the associated malware for this diary can be found at:
- http://malware-traffic-analysis.net/2015/06/16/2015-06-16-possible-Dridex-traffic.pcap
- http://malware-traffic-analysis.net/2015/06/16/2015-06-16-possible-Dridex-malware.zip
The zip file is protected with the standard password. If you don't know it, email [email protected] and ask.
---
Brad Duncan
ISC Handler and Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/diary/Recent+Dridex+activity/19687
[2] https://isc.sans.edu/diary/UpatreDyre+the+daily+grind+of+botnetbased+malspam/19657
[3] http://malware-traffic-analysis.net/2015/03/24/index2.html
[4] http://www.rackspace.com/blog/malicious-email-campaign-spreads-vawtrak-malware/
[5] https://www.virustotal.com/en/file/1ea2548ae6060765f125ed6173eeabf167eb53d70adde6f2c293b179526909ca/analysis/





Comments