SSH Fingerprints Are Important
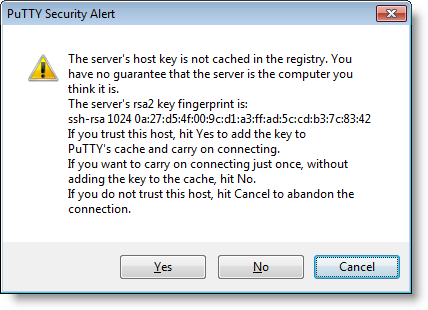
Some years ago, I was preparing Cisco certification exams. I connected via SSH to a new Cisco router, and was presented with this familiar dialog:
This made me think: before proceeding, I wanted to obtain the fingerprint out-of-band, via a trusted channel, so that I could verify it. So I took a console cable, logged on via the serial console, and … then I started to wonder what IOS command to type? A couple of hours later spend with Google, I was no closer to a solution. I could not find an IOS command to display the SSH fingerprint.
I found forum posts advising to connect via a crossover cable and write the presented SSH fingerprint down, but that’s not what I wanted. I had to work out my own solution.
There’s an IOS command to dump your public key: show crypto key mypubkey rsa
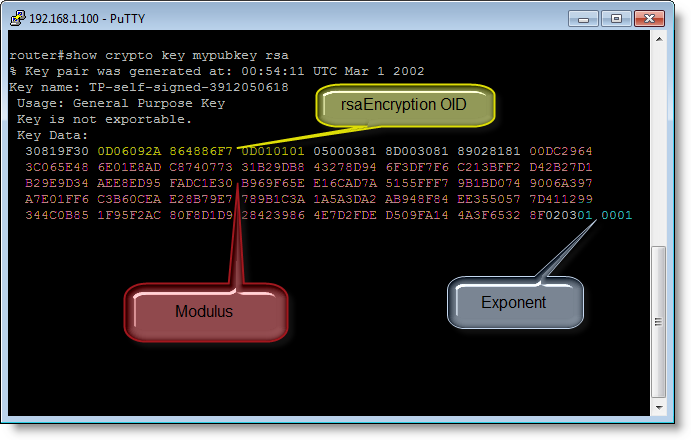
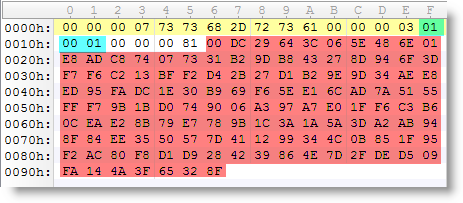
If you take the modulus and exponent of your public key, arrange them in another format (ssh-rsa) and calculate the MD5 hash, then you obtain the fingerprint.
Of course, I could not resist writing a Python program for that :-)
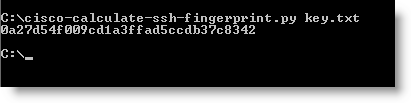
You can find it here.
If you know a Cisco IOS command to obtain the SSH fingerprint key directly, then please post a comment.
Update: on Cisco IOS versions released after I researched this, the "show ip ssh" command now displays the public key in ssh-rsa format (tested on 15.1(4)M3):
SSH Enabled - version 2.0
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 1024 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded):
ssh-rsa AAAAB3NzaC1yc2EAA.....
If you decode the base64 encoded ssh-rsa data, and calculate the MD5, you obtain the fingerprint.


Comments