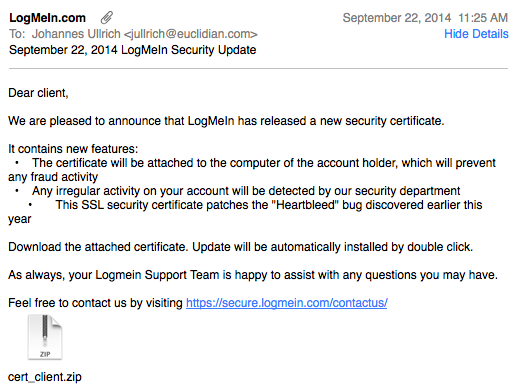
Fake LogMeIn Certificate Update with Bad AV Detection Rate
I just receive a pretty "plausible looking" e-mail claiming to originate from Logmein.com. The e-mail passed the first "gut check".
- The "From" address is [email protected].
- It was sent to an address I have used for Logmein in the past
- The only link inside the e-mail went to a legit Logmein URL.
Of course, the .zip attachment did set off some alarm bells, in particular as it unzipped to a .scr (Screen Saver).
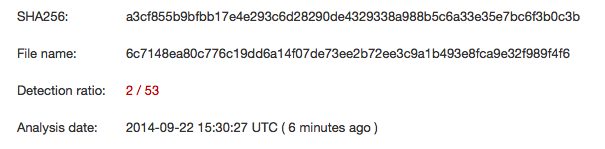
According to VirusTotal, AV detection is almost non-existant at this point:
LogmeIn does publish a SPF record, and the e-mail did not originate from a valid LogmeIn mail sender, so it should be easy to descriminate against these emails using a standard spam filter.
iOS 7.1.x Exploit Released (CVE-2014-4377)
Haven't upgraded to iOS 8 yet? Aside from a lot of new features, Apple also fixed a number of security vulnerabilities in iOS 8. For example CVE-2014-4377, a memory corrupion issue in iOS's core graphics library. An exploit is now available for this vulnerability.
NOTE: I have not verified yet that the exploit is working / genuine. We will not link at this point to the exploit code, but basic Google Fu should allow you to find it.
The author claims that the exploit is "compleatly reliable and portable on iOS 7.1.x". The exploit comes in the form of a malformed PDF, which would usually be delivered as an image inside an HTML page.
Cyber Security Awareness Month: What's your favorite/most scary false positive
As in prior years, we would like to use a theme for our October diaries, in order to participate in Cyber Security Awareness Month. This month, we are looking for "False Positives". One issue we are running into a lot is users who are new to security and start looking at logs, only to be confronted with unparsable, "scary" messages. But even as an experienced security practitioners, you can run into a an indicator that may initially get you to believe that your system is compromised only to learn later that there was nothing to worry about.
To help us out, please send us your favorite scary, but in the end bening, lot message or other error/system message. Please include a few details stating why you initially thought that there was a problem and how you came to believe that the message was nothing to worry about. We hope to cover about 1 message for each work day (5 / week). Please include how you would like to be identified (usually we use submitters first name)


Comments