Log Parsing with Mandiant Highlighter (1)
Reading log isn’t the most enjoyable thing in Network/Security Analysis, sometimes it’s impossible to get something useful from log without using a log parser .In this diary I am going to talk about one of my best log analysis tool.
MANDIANT HIGHLIGHTER
“MANDIANT Highlighter is a log file analysis tool. Highlighter provides a graphical component to log analysis that helps the analyst identify patterns. Highlighter also provides a number of features aimed at providing the analyst with mechanisms to weed through irrelevant data and pinpoint relevant data.”[i]
Installation:
1-Download Mandiant Highlighter from https://www.mandiant.com/resources/download/highlighter
2- Launch MandiantHighlighter1.1.3 and click Next
Highlighter Usage
Now let’s have some examples of using Mandiant Highlighter:
Let’s say that you have a snort log file and you would like to check for all MS-SQL related alerts:
- Go to File menu and select Open file.
2-open snortsyslog
3-Type MS-SQL in the keyword field
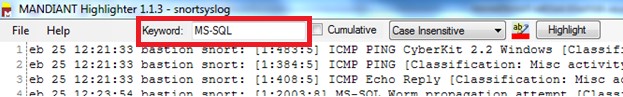
4-Click on Highlight ,Now Highlighter will highlights MS-SQL in the snortsyslog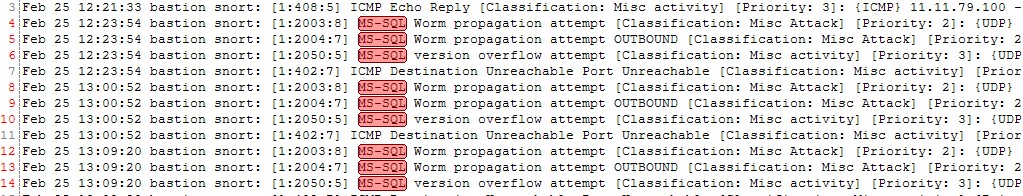
6-If you would like to filter the snortsyslog just to display MS-SQL related alerts:
- Highlight MS-SQL
- Right-click and select “Show Only”
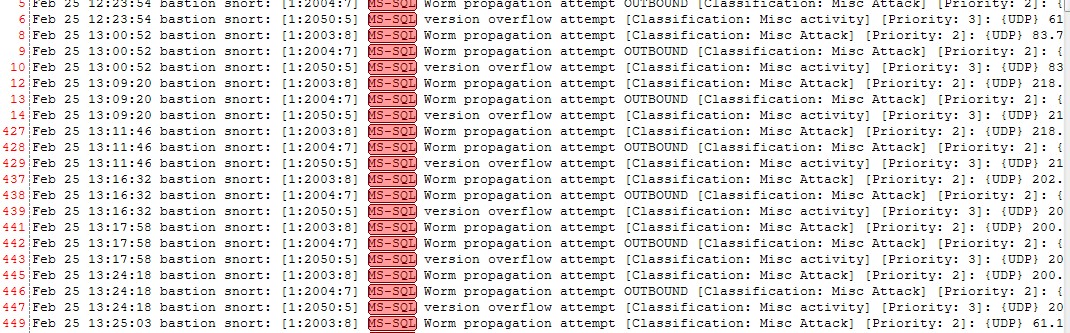
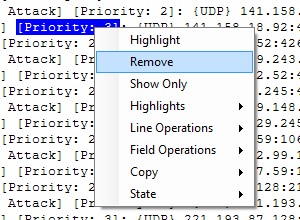
7-Now let say that you are not interested in Priority:3 events
a)right click on Priority: 3
b)Select Remove
In the next diary I will discuss some other advance options in Mandiant Highlighter
[i] Mandiant High-lighter User Guide.


Comments