Windows Autorun-3
In previous diaries I talked about some of the most common startup locations in windows environment.
In this diary I will talk about some of the method to enumerate these values from registry
1-Autoruns
Sysinternals Autoruns is the best tool available to enumerate the startup locations; it can locate almost every startup location in Windows. If you are a big fan of command line or you need something scriptable, Autorunsc is the command line version of Autoruns . Autoruns can detect the startup locations for the current user and any other user using the same system.
In addition one of the most powerful features of Autoruns is the ability of analyzing offline systems ,this will be very useful if you have a binary image of a compromised system.
Here is how to use it with an offline system:
1-Mount the image
2-File->Analyze Offline System..
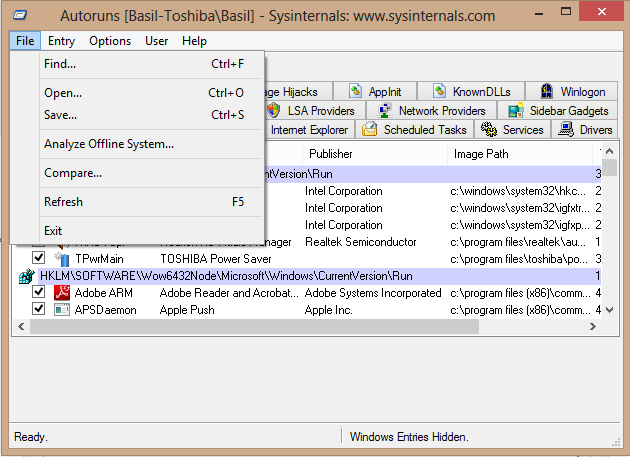
2-Provide System Root and User Profile Path
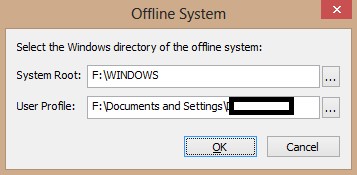
3-Click OK
2-Registry Editors/Viewers
In forensics world we cannot depend on one tool only, in many cases we have to double check the result of one tool using different tool.
In addition to the windows built-in tools (RegEdit, reg command and PowerShell Get-ChildItem/Get-ItemProperty) there are some great tools to analysis registry such as AccessData FTK Registry Viewer, Harlan Carvy RegRipper and TZWorks Yet Another Registry Utility (yaru).
One big advantage of yaru is the ability to recover deleted registry keys which is very useful when someone is trying to hide his track.
3-WMIC
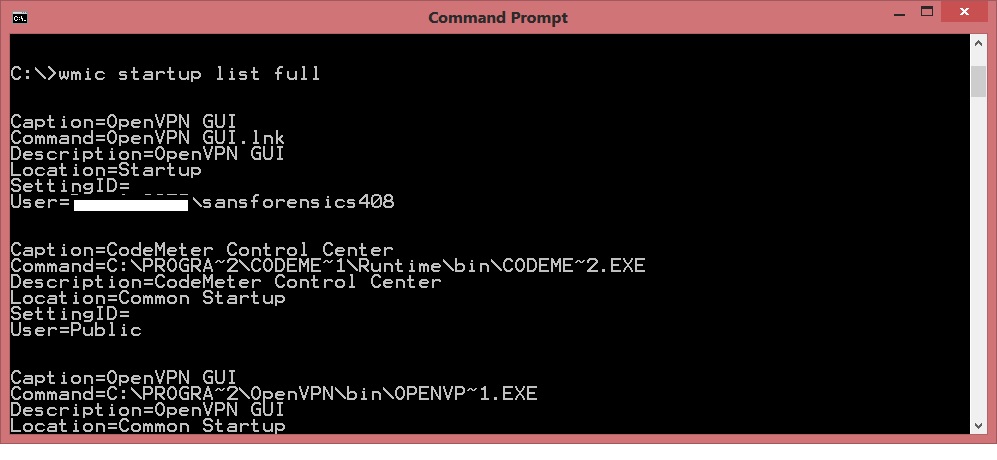
Windows Management Instrument Command-line has its own way to retrieve the startup location.
|
Wmic startup list full |
Cisco Small Business Devices backdoor fix
Cisco has released a new update fix to Cisco WAP4410N Wireless-N Access Point, Cisco WRVS4400N Wireless-N Gigabit Security Router, and the Cisco RVS4000 4-port Gigabit Security Router.
The vulnerability was an attacker can gain root-level access when he/she exploit a service listening on port 32764/tcp .
Here is the details from cisco website:
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140110-sbd


Comments