Windows Autorun Part-2
In previous diary I talked about startup folders and shell folders registry keys. In this diary I will continue talking about how to check if you are suspecting something malware or a compromised system.
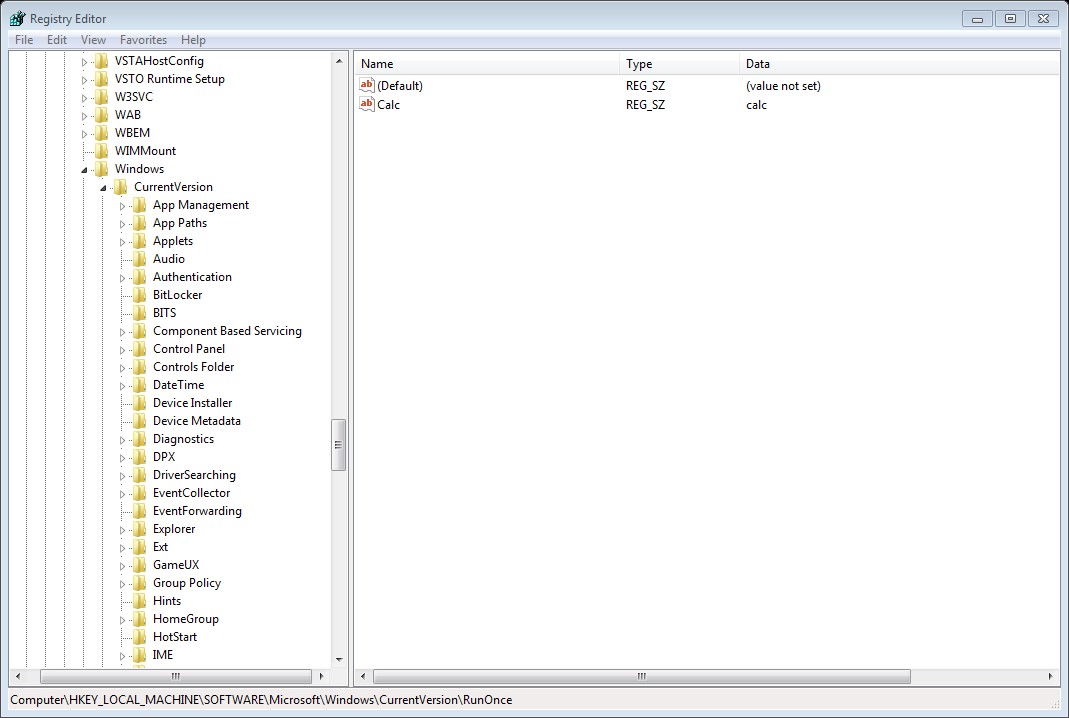
2-Run and RunOnce registry key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce\
Any executable in the above registry keys will start during the system startup, the different between Run and RunOnce is that RunOnce will run the value for one time then it will be deleted ,while Run it will run every time that the system startup.
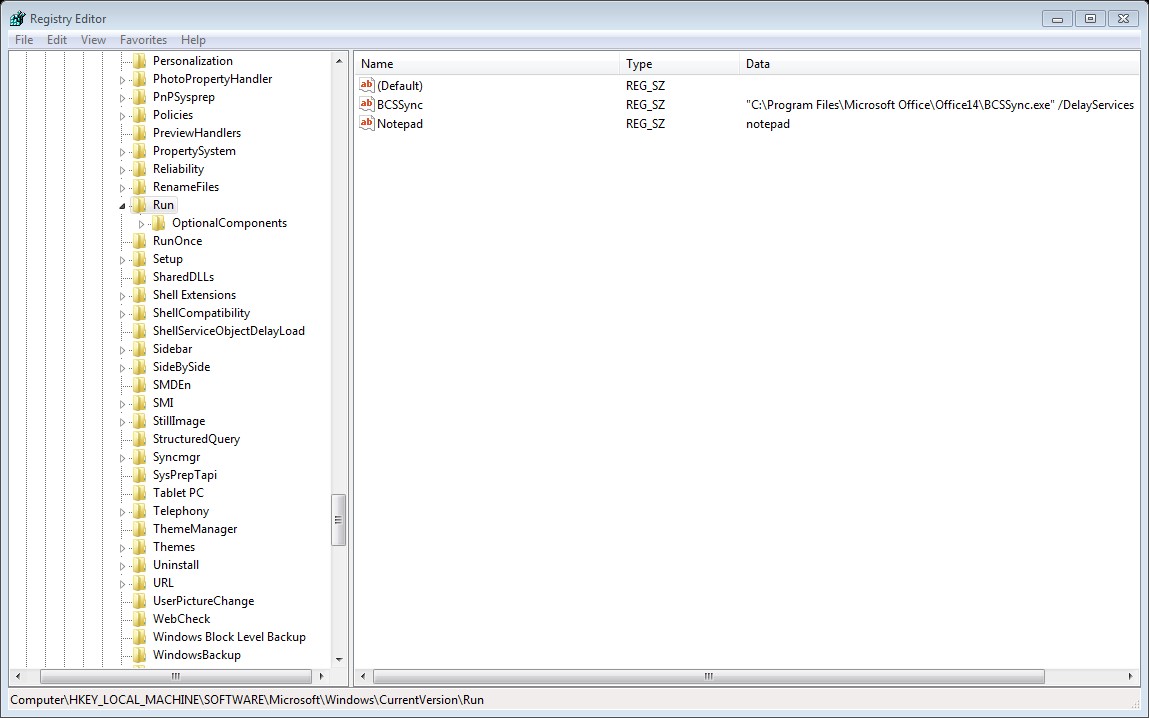
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\
The above keys is related to specific user login, again the different between Run and RunOnce is RunOnce will run one time the the value will be deleted while run will be run every time that the specific user log on.
3- Services
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
Here you can find the list of services that run at system startup, each service has a startup value as the following table:
|
Value |
Startup Type |
|
2 |
Automatic |
|
3 |
Manual |
|
4 |
Disabled |
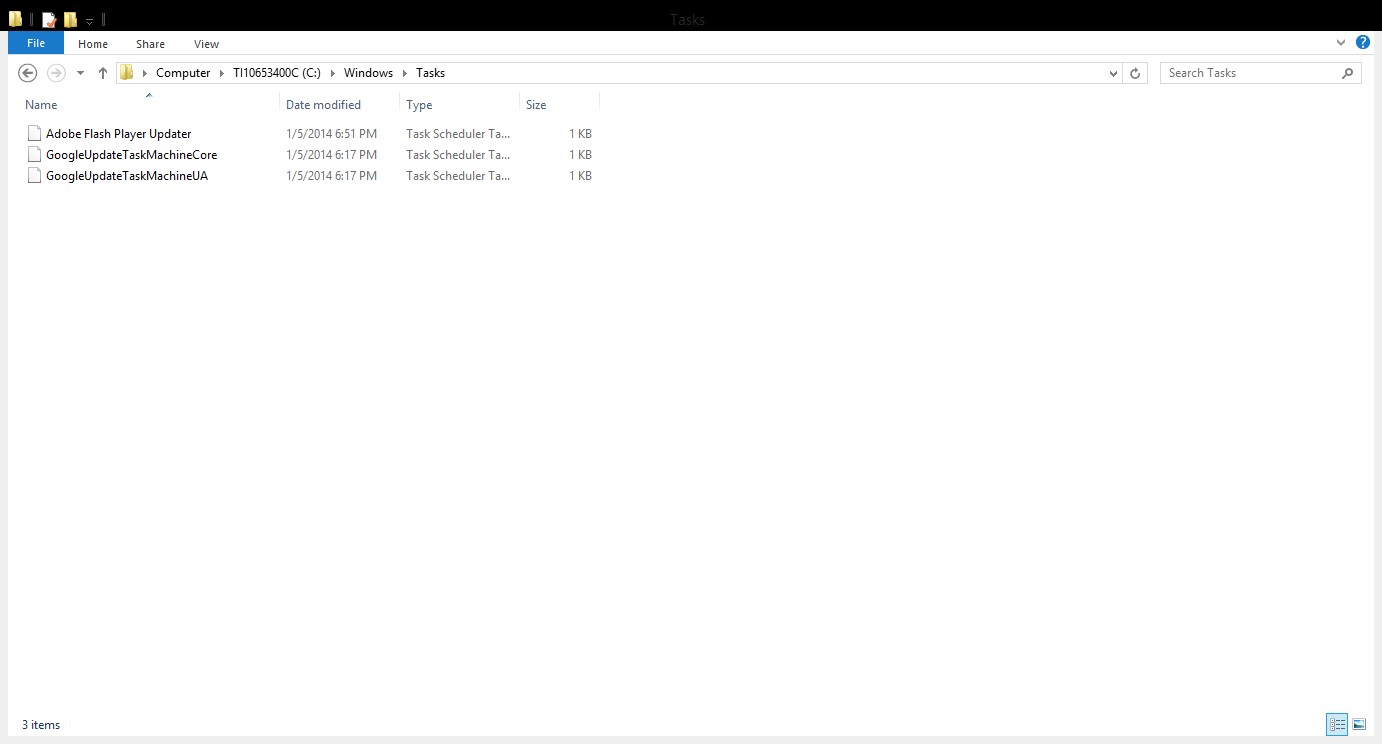
4-Schedule tasks:
Schedule task can be used to run a executable based on a schedule .The task are located in %windir%/tasks folder,of course attacker and malware will not use task name such as ‘I am malicious’ instead it will use some names that sound legitimate such ‘Windows Update’ .


Comments