Acquiring Memory Images with Dumpit
Memory has plenty of useful information for incident handlers such as open files, network connections and encryption keys. With pulling the plug forensics methodology you are losing all this information and you’re putting your skills into question if the case go to the court.
While analyzing memory require a set of skills, acquiring memory isn’t that difficult with the new tools available. On a previous diary[i] Mark Baggett wrote about using winpmem to acquire memory.
This diary will be about using similar tools which is Dumpit. Dumpit is a free tool written by Matthieu Suiche from MoonSols . Dumpit support both 64-bit and 32-bit Windows operating systems .
Dumpit can be downloaded from MoonSols website[ii] . After downloading and extracting the zip file it wil be a single executable file ‘dumpit.exe’.
One of the major benefits of Dumpit that it is very easy to use and any user with an admin privileges can use it. I would suggest that you provide your helpdesk team with some USB sticks with a copy of Dumpit, there are some issues that have to be considered: first the size of USB stick should be higher than the RAM size and if you have memory larger than 2 GB the USB sticks should be NTFS formatted.
When you have a suspicious event in a remote office or on a time that no body from the incident response team is available, a ready USB stick with Dumpit might be the ‘smoking gun’ for this incident.
The memory accusation can be performed with these three simple steps:
1. Insert the USB stick.
2. Double click on Dumpit icon (Figure 1)
3. Type “y” (figure 2)
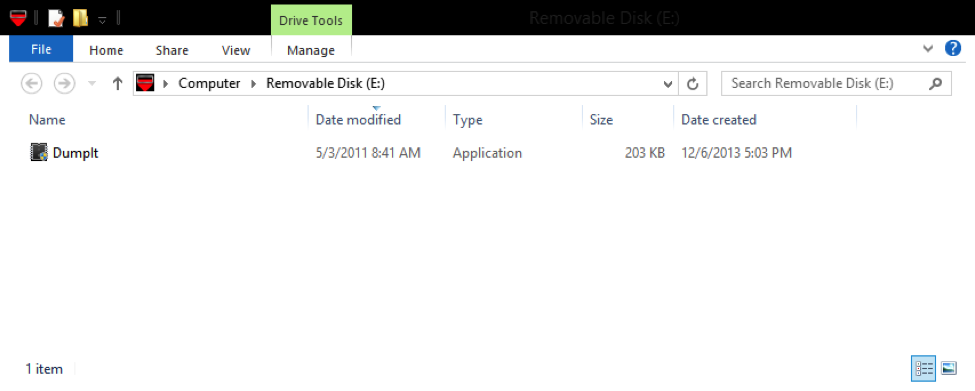
Figure 1 (Dumpit executable)
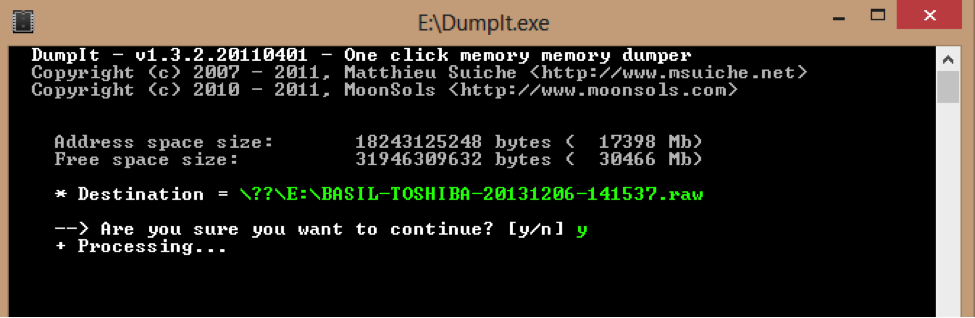
Figure 2 (Dumpit)
After few minutes the image will be ready on the USB stick as the computer name-date-time.raw (figure 3)
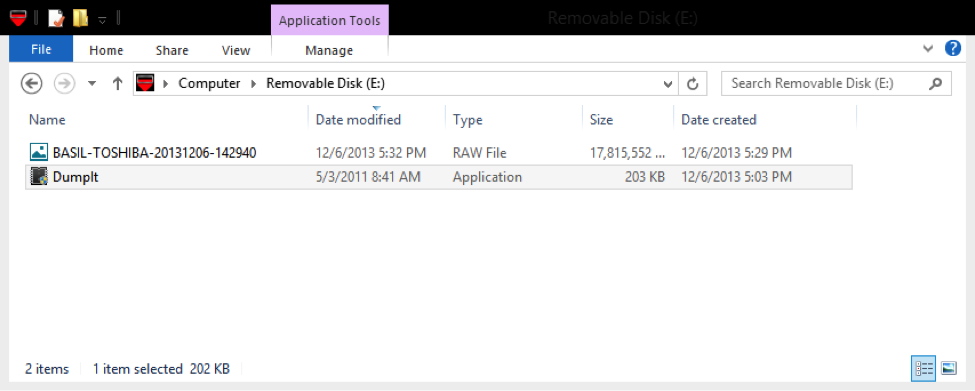
Since Dumpit is a simple tool, it doesn’t have any analysis capabilities .Tools such as Mandiant Redline can be used for the analysis purpose.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter


Comments