Extracting Digital Signatures from Signed Malware
Sometimes attackers digitally sign their malicious software. Examining properties of the signature helps malware analysts understand the context of the incident. Moreover, analysts could use the signature as an indicator of compromise. Here are some tips and tools for determining whether a suspicious Windows executable has been signed and for extracting the embedded signature in a Linux environment. We'll look at Pyew, Disitool and get a bit of help from OpenSSL.
Microsoft's Windows Authenticode Portable Executable Signature Format document explains that the signatures can be embedded "in a Windows PE file, in a location specified by the Certificate Table entry in Optional Header Data Directories." The location of the signature is stored within the PE header's OptionalHeader structure's Security field.
One way to determine whether the file contains an embedded signature is to use Pyew, which is a command-line hex editor/disassembler for malware analysis. After loading the sample into Pyew, you can look at the size of the IMAGE_DIRECTORY_ENTRY_SECURITY field. A non-zero value indicates that the file probably includes an embedded signature.To do this, load the PE file into Pyew and enter the command "pyew.pe.OPTIONAL_HEADER.DATA_DIRECTORY". Then look at the size of IMAGE_DIRECTORY_ENTRY_SECURITY as shown below:
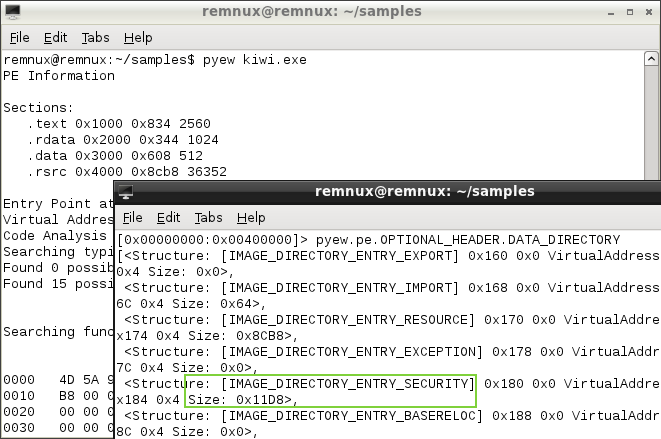
In the Pyew output above, we see that the size of IMAGE_DIRECTORY_ENTRY_SECURITY is non-zero. This indicates that kiwi.exe probably includes an embedded signature.
Disitool provides another way of determining whether a PE file includes a signature. This tool, created by Didier Stevens, can delete, copy, extract and add signatures. If you attempt to extract a signature from a non-signed file, Disitool will tell you "source file not signed."
In the example below, we see that the file has been signed. The author of this malicious file seems to have used a stolen certificate to sign the specimen. Disitool's "extract" command pulled out the signature, so we can examine it.
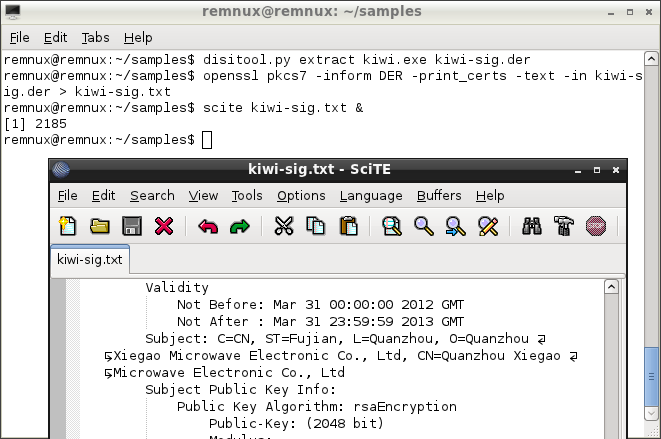
Disitool saves the extracted certificate in the binary DER format. You can look at the strings embedded in the DER file to examine its contents. Even better, you can use the following OpenSSL command to convert the DER file into a more informative text file:
openssl pkcs7 -inform DER -print_certs -text -in INPUT_FILE > OUT_FILE
Knowing how to spot signed files and extract signature details can be helpful for malware and forensic analysts. On Windows, you can gather some of these details by right-clicking on the PE file and looking at its properties, as well as with the help of Microsoft's Sign Tool and Sigcheck tools. On Linux, you can accomplish this with the help of Pyew, Disitool and OpenSSL, which are installed on REMnux for your convenience.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.


Comments