Adobe Acrobat Spam Going Strong - More to Come?
We received several reports of spam email messages that advertise a new version of Adobe Acrobat, attempting to entice the recipient into clicking a link to a suspicious website. (Thanks, Steve and Bill.)
Since Adobe announced a new version of Adobe Reader a few days ago, we expect to see an increase in spam proclaiming security advantages of the new version and encouraging people to upgrade. It's likely that the new messages will even highlight the improved security of the new version (Adobe Reader X) as an element of social engineering.
At the moment, Adobe Acrobat/Reader spam is not yet using the Reader X designation, but talks about "Adobe Acrobat 2010":
Subject: Download Your New Adobe PDF Reader For Windows And Mac
INTRODUCING UPGRADED ADOBE ACROBAT 2010
Dear Customers,
Adobe is pleased to announce new version upgrades for Adobe Acrobat 2010.
hxxp://www.adobe -acrobat-solutions.com
Advanced features include:
...
Variations of these messages have been around for a few months, as Adobe confirmed on September 13. The spam that we've seen have used mostly the same text in the body of the email message, but changed email Subject lines and destination URLs:
September:
Subject: Upgrade New Adobe Acrobat 2010 PDF Reader Alternative, hxxp://www.pdf -adobe-download.com
October:
Subject: Adobe Upgrade Notification, hxxp://www.adobe -upgrades.com
Subject: Action Required : Download Your New Adobe Acrobat Reader, hxxp://www.adobe -acrobat-new-download.com
Subject: New Adobe Acrobat PDF Reader Alternative, hxxp://www.official -adobe-software.com
November:
Subject: Action Required : Active Your New Adobe PDF Reader, hxxp://http://www.adobe -pro-software.com
Subject: Action Required : Upgrade Your New Adobe PDF Reader, hxxp://www.adobe -pro-upgrade.com
Subject: Download Your New Adobe PDF Reader For Windows And Mac, hxxp://www.adobe -acrobat-solutions.com
Note that suspicious domains used as part of this campaign tend to include "adobe" as part of its name, along with incorporating hyphens.
The domains that are still active were registered with Regional Network Information Center, JSC dba RU-CENTER and specified ns3.nic.ru, ns4.nic.ru, and ns8.nic.ru as their DNS servers. Contact details for the domain sometimes specified "PDF Reader Solutions" as the registrant, and were probably fake.
The sites advertised as part of the spam campaign attempt to convince the person to provide his or her credit number to obtain PDF reader/writer software using a form that's hosted on secureonline.ru. We haven't checked whether the software is actually malicious, but we're doubtful of its intentions.
Here's what the landing pages linked from spam messages looked like:

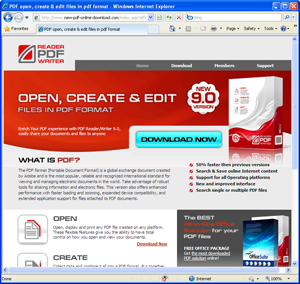
Here's what the subsequent pages, which requested user data, looked like:

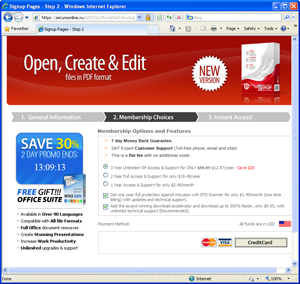
To see full-size images, visit the screen shot gallery at http://www.dropmocks.com/mKDOP.
Consider letting users in your organization know about these Adobe spam activities, so that they don't attempt to download and install software coming from an untrusted source.
Update: Brian Krebs published a story describing that the spamming campaign described in this note is part of criminal efforts that have been targeting "e-mail marketing companies that manage opt-in campaigns for some of the biggest corporate brands in existence."
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.
Brand Impersonations On-Line: Brandjacking and Social Networks
Companies invest heavily in their brands to build the desired association between the brand and the consumers. Most recently, organizations have embraced the practice of social media marketing campaigns to reach customers where they spend much of their time: on social networking sites such as Facebook, Twitter and LinkedIn.
Phishing: A Form of Brand Impersonation
Let's set the baseline by first looking at phishing, which is perhaps the most common form of on-line brand impersonation. Phishing typically involves setting up a website that resembles that of the company whose customers are targeted as part of the phishing attack. The idea is to convince the individuals that the website belongs to the trusted company, such as the person’s bank, so that the victim reveals sensitive information (such as logon credentials).
Phishing scams are often conducted with the help of cybersquatting, which is the act of "registering, trafficking in, or using a domain name with bad faith intent to profit from the goodwill of a trademark belonging to someone else." If the URL of the phishing site includes the impersonated company’s name or its product name, the victims are more likely to consider the site legitimate. (Unfortunately, some companies conduct marketing campaigns in a way that makes legitimate activities resemble phishing.)
Most companies whose customers are often targeted through phishing attacks know how to deal with these incidents by now. The effort involves identifying the appearance of phishing sites using approaches such as:
- Examining referrer logs of web servers for anomalies
- Soliciting phishing reports from customers
- Detecting fraudulent transactions
- Performing web searches for brand references
Once the company identifies a phishing site, it contacts the server's owner, hosting provider or the registrar to request that the site be shut down. There are firms offer phishing site take-down services to assist with this process.
Brandjacking: A Broader Perspective on Brand Impersonation
The term brandjacking refers to the act of assuming the on-line identity of a company or a person. From this perspective, phishing is a form of brandjacking. So is the act if impersonating a brand on a social network.
Brands might be impersonated by attackers on social networking sites to target the brand's customers. A fraudulent marketing campaign on a social networking site might look like it’s conducted by the brand, but it might actually be led by someone else. In the style of phishing, impersonation incidents put the brand’s customers’ data at risk, and may tarnish the brand's reputation.
Here are a few examples of Twitter accounts that were set up to impersonate well-known brands:
- BPGlobalPR: Set up during the gulf oil spill in 2010 to satirize and criticize the situation. It has amassed around 200,000 followers, while the official BP account BP_America has around 20,000 followers.
- ChuckNorris_: Spreads the humorous meme about Chuck Norris’ super powers and has around 21,000 followers.
- GapLogo: Set up in 2010 when Gap attempted to change its logo design. The account was used to satirize and critique the new logo and has around 5,000 followers.
Brand impersonation takes place on other social networks as well, of course. Here are a few examples:
- Screenwriter Alex Grossman impersonated Sarah Palin on Facebook by setting up an account named "Governor Palin."
- TechCrunch co-founder Michael Arrington impersonated Google CEO Eric Schmidt on Facebook.
- Researchers Shawn Moyer and Nathan Hamiel impersonated security expert Marcus Ranum on LinkedIn (with his permission)
Some brands (e.g., Chuck Norris) may benefit from the increased publicity brought about by the impersonator. In most cases, though, companies are rightly concerned that brandjacking will confuse consumers, dilute trademark defensibility and hurt the brand’s reputation. (For more on this, check out my social networking risks and rewards presentation.)
Dealing With Brand Impersonations on Social Networks
Identifying when the brand is being impersonated on social networks includes the activities outlined above in the context of phishing. Furthermore, a company can use search engines that can mine social networking sites to report upon all references to the company’s name, products, executive names or other elements of the brand.
Free social media search tools in this category include: SocialMention, Google Alerts, Twitter Search, Twazzup, CrowdEye, etc. Commercial tools include the various marketing campaign tracking tools, such as PostRank, and specialized products such as Social Sentry.
Once the company identifies the occurrence of brand impersonation, it can contact the corresponding social networking company, requesting that the account be shut down and, perhaps, transferred to the legitimate brand. The brand needs to clearly state why it believes the user of the social network who is impersonating the brand is violating that site’s terms of services or, perhaps, breaking the law. The request needs to include sufficient evidence to establish that the request comes from the legitimate brand and showing proof (e.g., screen shots) that the specified account impersonated the brand.
Read the terms of use and policies of the popular social networking sites in advance, so you don’t need to figure out whom to contact and how during the impersonation incident. A few pointers:
- How to report impersonation to Twitter
- How to report terms of use violations to LinkedIn
- How to report an impostor to MySpace
- How to report abuse to Facebook
If the incident is serious, the company may need to involve law enforcement. In all such cases, it’s wise for the company’s information security, legal and marketing professionals to collaborate on defining and executing the incident response process.
Social networking sites are thinking about ways of verifying the authenticity of high-profile accounts. Twitter calls this "Verified Accounts," and places a check mark badge next to the names of Twitter accounts that it has verified. Unfortunately, there is no way for a brand to be requested that Twitter verify it: this is a closed, limited "beta" process at the moment. I am not aware of similar efforts by other social networking platforms to provide a mechanism of verifying authenticity of account holders. All that users can do at the moment is to look at the accounts recent activities and the number of followers to assess the likelihood that the account is legitimate--a process that can easily be gamed.
Have you recently had to deal with a social network account take-down incident? Please leave a comment or drop us a note.
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.


Comments