Facebook "Like Pages"
I am seeing a trend on Facebook recently, and I am not sure what to make of it. As we all know just too well, Facebook has a "Like" feature. This feature, a little button associated with a post, allows you to show agreement with a post. Lately however, I am seeing more and more posts like the following:
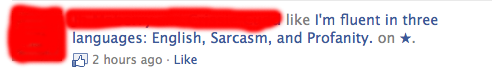
I covered up the parts identifying the friend of mine who posted this. A few things make these posts look "suspect": The post itself links to a domain "x.co". This is not the only domain used for these posts and it isn't obvious if they are all related (but many are). Another domain associated with x.co is for example thelikepage.com.
Once you click on it, you are offered a large number of other "provocative quotes" and offered to "like" them. At this point, I am mostly asking "what is the point"? Is it just an attempt to direct Facebook users to ad-covered pages? Or is there something more sinister at play? I don't see any exploits like click-jacking or cross-site-request-forging used. These pages also do not phish your credentials like some other similar pages.If you got an opinion or any further inside, please let us know.
Update: Just a quick summary of some of the feedback we got so far. Too much to mention every single one (Thanks BTW!)
Nobody has seen anything malicious from these URLs yet, so it appears to be just "Spam", maybe search engine optimization techniques to get these pages linked and ranked higher. A couple readers noted that unlike a regular "like", it is not so easy to remove these notes from your profile. You need to go to your "wall" page and remove them. You can not remove them like normal "Likes" from your "Newsfeed".
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
A Packet a Day
Not traveling this week, I got a bit extra time and decided to put up a couple "packet challenges". If you are following me on twitter, you may have already seen them. If not... here they are:
First one (with solution): http://johannes.homepc.org/packet1.txt
The second one (posted yesterday): http://johannes.homepc.org/packet.txt (I think I only got one decent answer for it so far, so I will keep it up a bit longer...)
A third one will be posted later today. And BTW... got packets? We always like good and interesting packets.
update: just made the new challenge live. again at http://johannes.homepc.org/packet.txt
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
OpenX Ad-Server Vulnerability
A vulnerability in some "random ad server" software wouldn't be terrible big news, but in this case I decided to spent a couple minutes on it. OpenX is somewhat popular, and used by various sites to server ads. Not only that... the vulnerability is actively being exploited. And to make things worse: The OpenX.com site is down, so you can't download a patch or any details "direct from the source".
We have seen compromised ad servers being used in the past to inject malicious content into various "trusted" pages and I am a bit afraid that we will see some of this with these OpenX vulnerabilities.
For more details: http://blog.sucuri.net/2010/09/openx-users-time-to-upgrade.html
(thanks to David of Sucuri for the heads up)
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter


Comments