Clickjacking attacks on Facebook's Like plugin
In last couple of days there has been an outbreak of clickjacking attacks on Facebook's "Like" plugin. For those unfamiliar with Facebook, this plugin allows users to mark certain pages as interesting, and subsequently in their profile a statement will appear that they "like" certain content.
Since we received a lot of e-mails from our readers about these attacks (and certainly some media covered variants of them), I decided to analyze one which is still up and working as I found it pretty interesting.
The main idea of this attack is to get a user to click on a hidden link while the user thinks he is actually clicking on something else – this is the basis for clickjacking attacks. So, let's see how it's done in Facebook's example.
The main malicious web page tries to entice the user to click on it to see the rest of the so called "best passport application rejection in history". The web page just contains a single JPG image and you can see below what it looks like:

Now, what happens behind the scenes is pretty interesting. The HTML source contains two obfuscated JavaScript elements and an iframe that do all the work.
Let's first see what the iframe does:
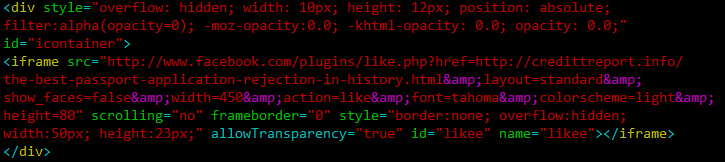
The div tag sets this iframe completely invisible (and the attacker makes sure that this works in every browser by using all the possible opacity combinations). Then the iframe points to the Like plugin at Facebook, and sets the href parameter to the target web site (the credittreport.info site).
This is what shows in the iframe:
![]()
Yes, there are 15,687 people "infected" with this.
Now comes the interesting part – how to make the user click on this, relatively small icon. The second obfuscated JavaScript element tells the rest of the story:
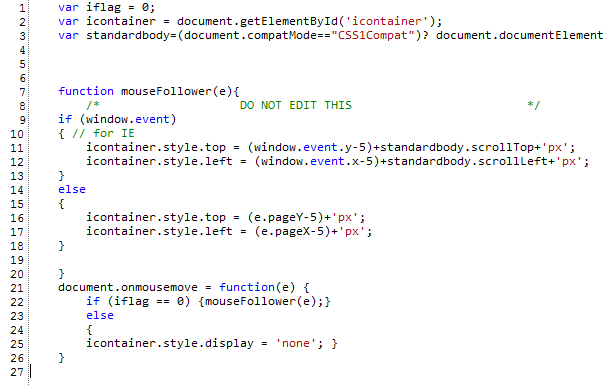
Let's analyze this JavaScript code. In line 2 they get the "icontainer" element – this element holds the iframe, you can see in the iframe code above that the div tag uses the id "icontainer". The standardbody object will contain the document body. Now, let's skip to line 21 – this line defines a handler for mouse movement. So, every time the mouse is moved, this function, starting with line 22 is called. The function checks if the iflag variable is 0 (and it is, until the user clicks on the hidden element). If the variable is 0, the mouse movement handler will call the mouseFollower() function. And this is the main trick – the mouseFollower() function actually moves the iframe to follow the mouse! So the attackers made sure that no matter where you click on the web page, you will land on the hidden Facebook button and "infect" yourself by posting a message on your profile saying that you like this malicious site. When a friend of yours click on that link, he/she will be taken to this web page again and no matter where they click, they will end up doing the same! If you close the window, nothing will happen.
Attacks such as this one have become increasingly popular lately, so be careful what you click on, no matter if it's in Facebook or not. If you are a Facebook user, be especially careful of all links, especially those that require you to click on something else to see the real content.
While this isn't really a vulnerability in Facebook, it does appear that their team will have to step up and implement some controls to prevent clickjacking attacks such as this one.
-- Bojan
INFIGO IS
New Mac malware - OSX/Onionspy
A new strain of MAC Malware is being reported by Intego - OSX/OpinionSpy.
You can find details here:
http://blog.intego.com/2010/06/01/intego-security-alert-osxopinionspy-spyware-installed-by-freely-distributed-mac-applications/
http://webcache.googleusercontent.com/search?q=cache:tWyWhF_d-30J:blog.intego.com/+flv+mp3+intego&cd=1&hl=en&ct=clnk&gl=ca&client=firefox-a
So far, it has been seen on a number of screensavers, and a small java/php app generally named "mac_flv_to_mp3.php" or similar, but be cautious on downloads, it's a simple bolt-on, so be on the lookout for it elsewhere.
The neat thing about this malware is that it passes most static scan tests - the downloaded software itself is clean, the malware is downloaded as part of the installation process. This highlights the requirement for an on-access virus scanner for your OSX computers. I hate to bring "that advertisement" up again, but the "viruses? oh, mac's don't have that problem" statement was both not true and a huge red flag for malware authors.
Thanks to several readers for both pointing us to this article, and shooting us a copy of the actual code !
=============== Rob VandenBrink Metafore
SPAM pretending to be from Habitat for Humanity
I received a disturbing (to me) piece of SPAM this morning:
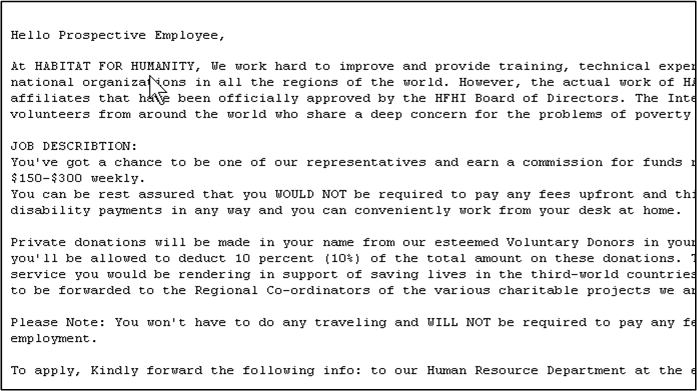
As happens occasionally, this one sailed through our SPAM filter, but it got my attention for a number of reasons
The spelling and grammar are pretty good - this does not look like your typical spam
- It doesn't ask for money
- It does ask for your personal information
- It pretends to come from a charity that has a long history of delivering services via volunteering.
- After a bit of digging, this looks like a new specimen, just cropping up over the last few days (I could be wrong on this, please correct me if so)
- I think it bothers me so much at a personal level because H for H is a favourite charity of mine - where else can you do so much good, and get to use your power tools at the same time?
As you'd expect, the text of the "reply to" looks like a legit-sounding address, but under the text, the actual link goes to a bogus gmail account.
So, I thought - what to do? I haven't been an admin responsible for a corporate mail server in several years - is this kind of spam normal these days? My best answer to this question was "ask the readers at ISC" - any comments that any of you might have on this spam-bit, or any trend that it may represent would be very much appreciated. Please use the comment button, and pass along any info you may have.
As a trend, we see that SPAM tends to follow the news. I'd expect that we're seeing SPAM about the BP oil disaster in the Gulf of Mexico, and also about the Pacaya volcano eruption near Guatemala City. Are you seeing spam taking advantage of these events?
Just to feed the discussion a bit more - what's next? Will we be seeing SPAM from bogus medical labs - "There may be an issue with your recent blood test, please enter your information to verify" or some-such? How far will these low-lifes go to get our info or cash?
I'd like to say I'm disappointed in our fellow online denizens, but really the worse these get, the more I almost seem to expect them.
Please comment, let us know what you're seeing out there spam-wise !
=============== Rob VandenBrink Metafore ===============


Comments