Defining Clouds - " A Cloud by any Other Name Would be a Lot Less Confusing"
So What is Cloud Computing Anyway? Do you find yourself saying "am I the only one that is confused about this?"
The short answer is No, you're not the only one confused about this. Most of the people who put the word "Cloud" in their headline are confused as well (except us of course). Over the last couple of years, the amount of press about "Cloud Computing" has been steadily increasing, as interest in virtualization grows. However, it seems like everyone who writes a "Cloud" article means something different when they use the word, and in many cases it's easy to see some real mis-understanding of key details around some of the virtualization and service
So, let's dive right in - when someone says "Cloud", they generally mean one of several things:
Colocation Services
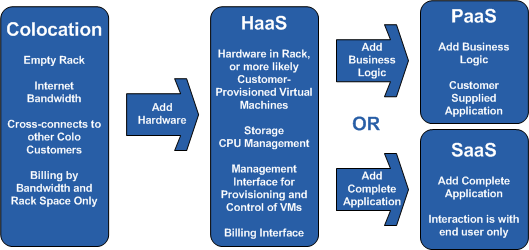
Colocation Services (often shortened to "Colo") is the oldest service of the bunch, and essentially offers an empty rack with very fast communications, reliable power and air conditioning. Colos are often serviced by several ISP's (Internet Service Providers). Providing server hardware, firewalls and load balancers are the responsibility of the customer. Colo services generally aren't included when people reference "clouds", but they're included here to provide a more complete picture
Host as a Service (HaaS) / Infrastructure as a Service (IaaS)
Most commonly called IaaS, this offering uses virtualization to provide computing cycles, memory and storage. IaaS vendors provide the communications, power and environmental controls of a Colo, but also provide the hardware in the form of a "home" for virtual machines (VMs). In the past, HaaS has been just that, renting physical server platforms along with Colo facilities. What has changed this industry so much in the past few years has been virtualization - one server can now be shared by 20 customer virtual machines - either 20 from 1 customer, or from 20 different customers.
The VMs are provided by the customer, which are uploaded, deployed to the IaaS storage pool and started using a management interface. Because virtualization is used, IaaS clouds can offer enhanced services based on what their virtualization platform has available. For instance, when one VM ramps up it's CPU requirements, other VMs that might be on that same server can automatically migrate to a less busy hardware platform, maintaining a consistent profile of available CPU resources for all customers. Similarly, if maintenance is required on a host or storage platform, VMs can be manually migrated away, ensuring constant uptime, even during hardware maintenance.
Some IaaS vendors have extended their service to include additional services such as database, queueing, backup and remote storage. This reduces the software license costs for the customers, but of course also increases the monthly costs of the IaaS service.
IaaS services typically charge their clients based on Compute Usage, Data transfered in and out, Database requests, Storage used, and Storage requests and transfers. IaaS vendors include Amazon EC2 services ( based on XEN), Rackspace and Terremark (both based on VMware's vSphere products).
Computer as a Service (CaaS) or Desktop as a Service (DaaS) are special cases of an IaaS service. These generally referes to VDI (Virtual Device Infrastructure) solutions such as VMware View. These solutions are a special case of an Iaas, but delivering a desktop operating system such as Windows XP, Windows 7 or a desktop Linux OS. These are often used to deliver applications that for one reason or another don't belong on the actual physical desktops in the environment. They might be easier to maintain on the server, there might be bandwidth issues, where the VDI traffic overhead might be substantially less the "fat" application, or regulatory requirements, where the data and application can't live on the remote desktop computer, in case of theft or compromise.
Platform as a Service (Paas)
Platform as a Service takes the environment offered by IaaS, and adds the operating system, patching, and a back-end interface for applications. The customer uploads their application in a standard format, written to use the PaaS interfaces, and the rest is up to the PaaS vendors.For instance, Microsoft's Azure services platform offers .Net Framework and PHP as back-end interfaces, Google App engine has backend interfaces based on Java and Python, and Salesforce.com has proprietary interfaces for business logic and user interface design.
Software as a Service (SaaS)
Software as a Service delivers a fully functional application to the end user, generally with per-user billing.
Google Apps is the latest entry into this field, and seems to have the most press lately - they offer a full office suite including the pre-existing mail (gmail) service. However, lots of other vendors offer SaaS products - Microsoft offers online versions of Exchange, Sharepoint and Dynamics CRM. Salesforce.com has their Salesforce CRM product, and IBM offers LotusLive, which is a hosted Domino environment.
Private Clouds
The thing about all of these "Cloud" architectures we've just described is that none of them are really new. They've all existing in the datacenters of many corporations, running as VMware, XEN, Hyper-V or Citrix servers, and have been there in some cases for 10 years or more. What the new IaaS, PaaS and SaaS services offer is a mechanism to outsource these private infrastructures, generally over the internet. The new functions that these Public Cloud infrastructures bring to the table is new management interfaces and most importantly a billing interface, because nobody would be doing this if there wasn't a good way to charge for it and make a profit.
An interesting thing that we're seeing more and more of lately is internal billing for private cloud services, where production departments within a company are billed by their IT group for use of services in the Datacenter. This has been a slow-moving trend over the last 10 years or so, but with the new API's offered by virtualization platforms, the interfaces required for billing purposes are much more easy to write code for. The goal of these efforts is often a "zero cost datacenter", where production departments actually budget for IT services, rather than IT. While this may be a goal to shoot for, it's not one that is commonly realized today.
=============== Rob VandenBrink Metafore ===============
Cisco Security Agent Security Updates: cisco-sa-20100217-csa
From the advisory, specific CSA versions and components are vulnerable to SQL injection and directory traversal (allowing unauthorized config changes for instance), as well as a DOS (Denial of Service) condition.
Cisco Security Agent releases 5.1, 5.2 and 6.0 are affected by the SQL injection vulnerability. Only Cisco Security Agent release 6.0 is affected by the directory traversal vulnerability. Only Cisco Security Agent release 5.2 is affected by the DoS vulnerability.
Note: Only the Management Center for Cisco Security Agents is affected by the directory traversal and SQL injection vulnerabilities. The agents installed on user end-points are not affected.
Only Cisco Security Agent release 5.2 for Windows and Linux, either managed or standalone, are affected by the DoS vulnerability.
Standalone agents are installed in the following products:
* Cisco Unified Communications Manager (CallManager)
* Cisco Conference Connection (CCC)
* Emergency Responder
* IPCC Express
* IPCC Enterprise
* IPCC Hosted
* IP Interactive Voice Response (IP IVR)
* IP Queue Manager
* Intelligent Contact Management (ICM)
* Cisco Voice Portal (CVP)
* Cisco Unified Meeting Place
* Cisco Personal Assistant (PA)
* Cisco Unity
* Cisco Unity Connection
* Cisco Unity Bridge
* Cisco Secure ACS Solution Engine
* Cisco Internet Service Node (ISN)
* Cisco Security Manager (CSM)
Note: The Sun Solaris version of the Cisco Security Agent is not affected by these vulnerabilities.
The full advisory, including a matrix of vulnerable and fixed versions, can be found here ==> http://www.cisco.com/warp/public/707/cisco-sa-20100217-csa.shtml
=============== Rob VandenBrink Metafore ===============
Cisco ASA5500 Security Updates - cisco-sa-20100217-asa
Tim reports that Cisco has released a security advisory for Cisco ASA5500 products, outlining some security vulnerabilities and resolutions
The issues are:
- TCP Connection Exhaustion Denial of Service Vulnerability
- Session Initiation Protocol (SIP) Inspection Denial of Service Vulnerabilities
- Skinny Client Control Protocol (SCCP) Inspection Denial of Service Vulnerability
- WebVPN Datagram Transport Layer Security (DTLS) Denial of Service Vulnerability
- Crafted TCP Segment Denial of Service Vulnerability
- Crafted Internet Key Exchange (IKE) Message Denial of Service Vulnerability
- NT LAN Manager version 1 (NTLMv1) Authentication Bypass Vulnerability
All issues are resolved by upgrading to an appropriate OS version, outlined in a table in the advisory. If that is not possible, workarounds for many of these issues are also provided.
Most of these are DOS (Denial of Service) conditions, however the authentication bypass issue is much more serious. If your ASA configuration requires NTLMv1 authentication, then read this advisory closely and upgrade to the appropriate OS version as soon as possible ! A workaround that's not referenced in the Cisco doc is changing to RADIUS authentication in place of NTLMv1. If an OS update is not easy to schedule in the near future, this might be a better approach short term (or even long term) than using NTLMv1.
Find the advisory here ==> http://www.cisco.com/en/US/products/products_security_advisory09186a0080b1910c.shtml
=============== Rob VandenBrink Metafore ===============
Multiple Security Updates for ESX 3.x and ESXi 3.x
A number of ESX 3.x security updates are out today. These are released along with updates affecting several operational (non-security) issues.
ESX3.5 update for python packages, that resolves issues with VM Shutdown ESX350-201002402-SG ==> http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1017663
ESX 3.5 update, involving remote execution via XML, updates to libxml packages, ESX350-201002407-SG ==> http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1017679
Updates for BIND on ESX 3.5, ESX350-201002404-SG ==> http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1017679
Updates to resolve a buffer overflow in NTP in ESXi 3.5 (among other things), ESXe350-201002401-I-SG ==> http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1017685
Updates for SNMP that affect ESX 3.0.3 - 3.5, ESX350-201002401 ==> http://lists.vmware.com/pipermail/security-announce/2010/000080.html and ==> http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1017660
Full details on all of these, along with the operational patches, can be found at ==> https://www.vmware.com/mysupport/portlets/patchupdate/allpatches.html
*** none of these updates affect the current version vSphere 4.x ***
=============== Rob VandenBrink Metafore ===============


Comments