Christmas Ecard Malware
For years, Storm was the threat most commonly associated with malicious Christmas cards and other "timely announcements". Their techniques have gradually been adopted by other organized crime groups, and over the last days there has been an increase in malicious Christmas cards distributing the Waledac worm.
The e-mails consist of a hyperlink to a "Christmas card". When the user visits this site, he will see the following. The user will need to click on either button, get a Security Warning and will need to accept the fact that an executable is being run.
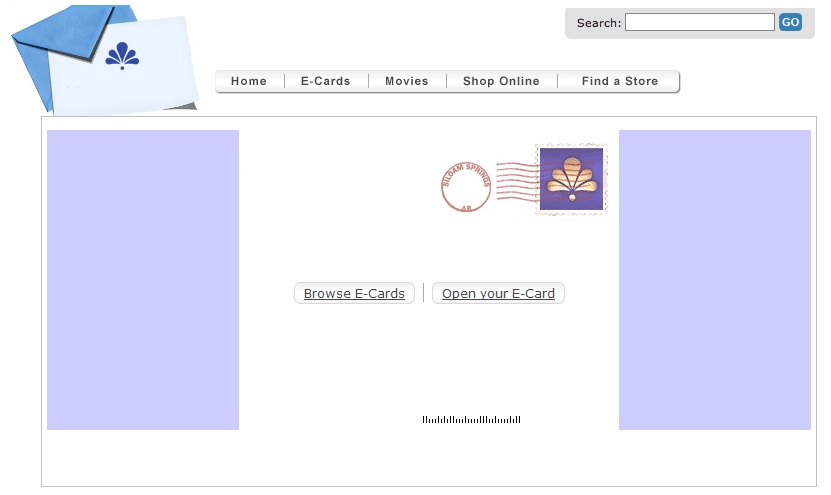
Most likely because of this, and because the cards are coming in fairly late in the holiday cycle, the threat has not been wildly succesful at propagating. Interestingly, even though the first reports of this threat we have are dated December 21st, many of the domains were already registered on December 1st.
Some of the domains that were reported to us by readers (thanks Mike and the Shadowserver foundation) include:
bestchristmascard.com
blackchristmascard.com
cheapdecember.com
christmaslightsnow.com
decemberchristmas.com
directchristmasgift.com
freechristmassite.com
freechristmasworld.com
freedecember.com
funnychristmasguide.com
holidayxmas.com
itsfatherchristmas.com
justchristmasgift.com
livechristmascard.com
livechristmasgift.com
superchristmasday.com
superchristmaslights.com
whitewhitechristmas.com
yourchristmaslights.com
yourdecember.com
Update: Shadowserver published a full list of the domains they've seen for this worm.
For now, we recommend:
- Blocking the download of 'ecard.exe', or the affiliated domains on your corporate proxy;
- Ensure that your anti virus and anti spam solutions are updated frequently as the AV vendors build coverage for this new threat. Given the mass mailing nature, spam protection is likely to be the first to pick up on this.
In the long run, we recommend educating your users on the risk involved with gratuitous "warning" e-mails related to events, or greeting cards that look even the slightest bit suspicious. In addition, consider investigating solutions that control which untrusted code, originating from the internet, can be executed on corporate desktops.
Arbor Networks has an interesting blog entry up on the flux tactics involved with this threat here. For further data on the worm itself, visit Symantec's writeup.
Merry Christmas, and beware of digital hitchhikers!
For those of us who celebrate it, Christmas not only has religious meaning, it is also synonymous to gift giving. Though still a small percentage, every year the number of “connected” gifts increases: photo frames, USB sticks, cameras. Each of these now has a USB interface to connect to your desktop computer. This is a powerful innovation: combining these tools makes them much more powerful than each of them individually.
One disadvantage of such interconnectedness is the risk of malicious code hitching along with them. This is a problem of all ages: floppy disks were for a while a potent means of transmission for boot-sector viruses, downloads, and even CD-ROMs with infected installers all have been or are still important infection vectors. Just in the last few weeks, Samsung reportedly shipped photo frames with an infected CD in the package.
There are many common pathways for malicious code to make its way onto USB hardware, even though it looks like it may come straight “out of the box”. Generally, during assembly a small number of devices will get pulled out of production for quality assurance testing. An infection of equipment in the QA environment would be noticed far less quickly than in the production environment, as the set of affected samples would be drastically less.
In addition, vendors want to offer their customers a bright shopping experience, and this generally includes giving them the ability to return items that would turn out to be a misbuy. In almost all cases, these items will be tested for functionality, but that is never a 100% guarantee that its state is identical to the newly manufactured item. What happened while in possession of a customer after the initial purchase is somewhat unclear, and could include introduction of unexpected code.
The good news, however, is that most Autorun malware spreads relatively rapidly – making it something the anti virus companies stay on top of. If you are running up-to-date anti virus software, it’s unlikely you will be at much risk of any of the major Autorun malware families.
If you’d like to provide some additional protection to your family members for the holidays, you may want to consider running a behavioral based anti malware product in addition to your regular anti virus. These applications apply a techniqua called behavioral profiling. They do not detect viruses based on a signature applied to every binary, but instead look at the behavior of every binary running on the system.
Every “suspicious” action, such as writing to windows\system32, installing a service, or making an internet connection is given a specific rating, and once that rating exceeds a preset threshold for a binary, the solution will flag the process as potentially malicious and will alert the user. While we can't recommend vendors, common solutions include Threatfire, Primary Response SafeConnect and NovaShield. Some common anti virus packages even include this functionality, so talk to your existing vendor as well. Combining this with signature based anti virus provides the best of both worlds on end user platforms, where the owner of the system needs to be able to have full control and ability to install whatever code he wishes. Known malicious code will be stopped before execution and identified, and unknown malicious code will be blocked before it does too much harm.
From all of us here at the SANS Internet Storm Center, have a great holiday season!
Cheers,
Maarten


Comments