Use of CSS stuffing as an obfuscation technique?
From time to time, it can be instructive to look at generic phishing messages that are delivered to one’s inbox or that are caught by basic spam filters. Although one usually doesn’t find much of interest, sometimes these little excursions into what should be a run-of-the-mill collection of basic, commonly used phishing techniques can lead one to find something new and unusual. This was the case with one of the messages delivered to our handler inbox yesterday…
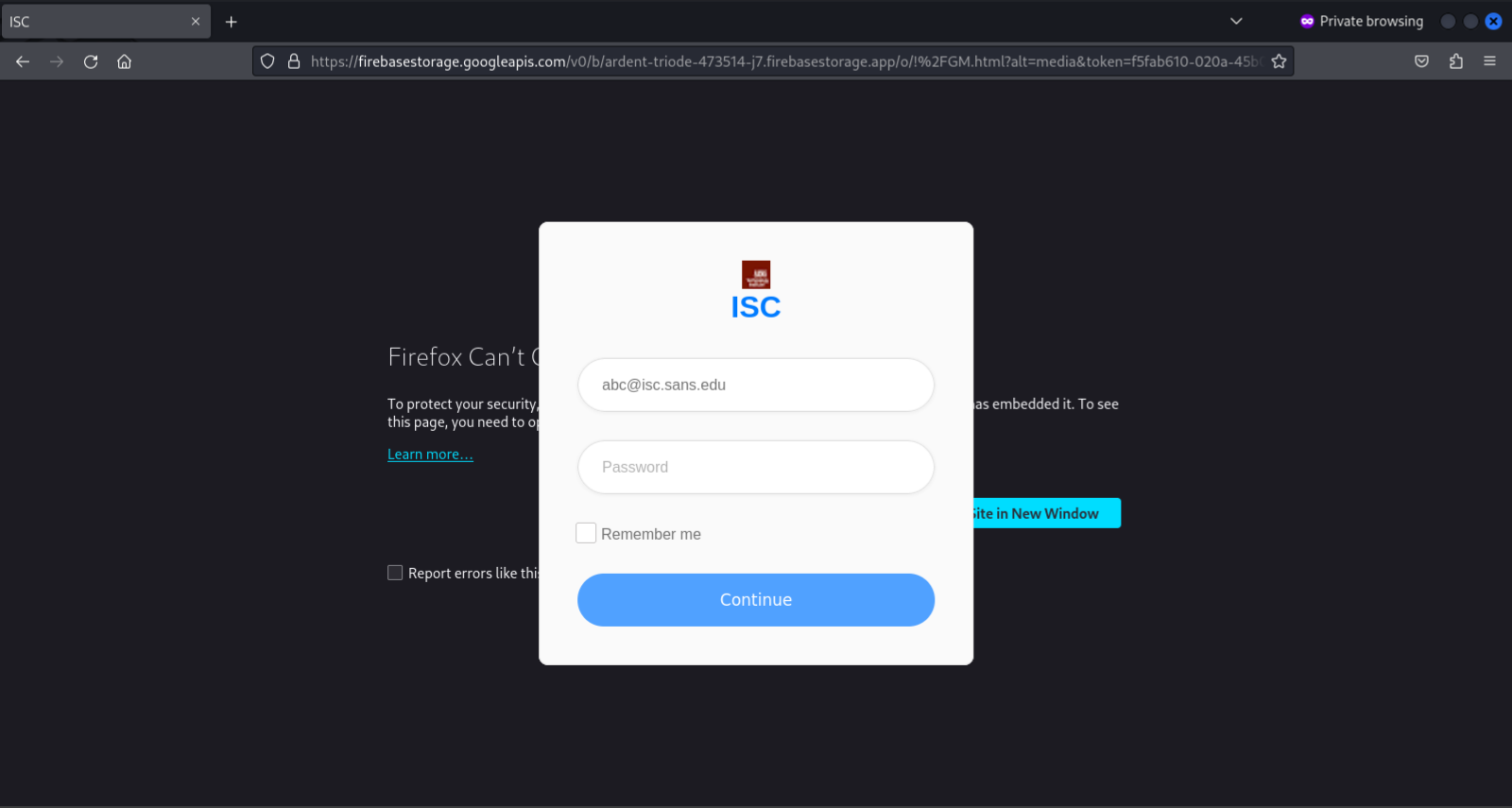
The message in question looked quite unremarkable at first glance, as the link it contained pointed to an HTML page located in a Google Firebase Storage, which has been commonly misused by threat actors to save malicious content for many years now[1].
The interesting part still wasn’t apparent when I first opened the page, since, as you can see, it appeared to be a fairly typical credential harvesting page that tried to overlay a fake login prompt over a legitimate page loaded (unsuccessfully, in the case of isc.sans.edu, due to our Content Security Policy and X-Frame-Options settings) from a domain extracted from a personalized link sent to the recipient of the original phishing message…
What turned out to be unusual was the source code of this page. Although it was 449 KB in size, it contained only about 10 KB (or roughly 250 lines of code) that was actually used when the page was rendered. The remaining hundreds of kilobytes were made up of unused style data – most of it was renamed and/or slightly modified copy-pasted CSS code that was actually used in the page, and about a third of it consisted of a copy of bootstrap.min.css.
Since the copy-pasting of CSS code was certainly intentional, this “CSS stuffing” approach (along with the use of <html lang="zxx"> in the page header[2]) seems to me to have been a fairly unusual attempt at bypassing some of the less effective security filtering mechanisms.
While the size of the file on its own would most likely not be enough to bypass any security scanner used to analyze HTTP traffic altogether, given that most of these tend to have scan limits for file sizes at least in the tens of megabytes range, the amount of benign-looking CSS code might perhaps be enough to change the statistical profile of the HTML page sufficiently to enable the file to pass through some heuristic or machine-learning based systems unnoticed.
Admittedly, this is just speculation, but it is certainly the best explanation for this strange use of CSS code I can think of…
[1] https://blog.knowbe4.com/phishing-campaigns-using-google-firebase-storage
[2] https://www.w3.org/International/questions/qa-no-language
-----------
Jan Kopriva
LinkedIn
Nettles Consulting


Comments