Infocon

The intent of the 'Infocon' is to reflect changes in malicious traffic and the possibility of disrupted connectivity. In particular important is the concept of "Change". Every host connected to the Internet is subject to some amount of traffic caused by worms and viruses. However, once a worm has been identified and the number of infected machines is no longer increasing, this traffic is not likely to cause any disruptions.
The Infocon is intended to apply to the condition of the Internet infrastructure. We do not monitor particular nations or companies.
Link To Current Infocon Status
You may use the following html code to link to the current Infocon status:
In addition to the graphic, we offer two text feeds. The text feed can take up to 15 minutes to update.
- infocon.txt: The Infocon color. Just one word in plain text
- daily_alert.html: The daily alert. Infocon and handlers diary headline as minmal HTML feed for inclusion in web sites
For fans of RSS newsfeeds, check our RSS feed at rssfeed.xml
If we change the Infocon, we try to remain at the same level for at least 24 hrs.
Applications and Widgets
- Neil Fryer wrote an Apple OS X SANS Internet Storm Center Widget (by Neil Fryer)
- Jörn Ahrens wrote an Infocon monitor for KDE ("infokon"). See http://www.jokele.de/infokon/.
- Anthony Parkes created a nagios script to report the ISC Threat Level.
- John Lowry wrote a nagios plugin to report the ISC Threat Level.
Infocon Definition
Infocon images below use a white background. Transparent images are available by adding "_transparent" such as status_blue_transparent.gif.
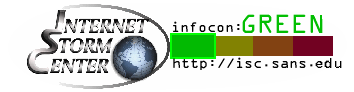 |
Everything is normal. No significant new threat known. |
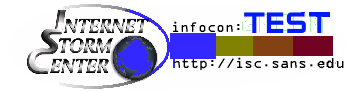 |
This status is used for testing only. Everything is normal. No significant new threat known. |
 |
We are currently tracking a significant new threat. The impact is either unknown or expected to be minor to the infrastructure. However, local impact could be significant. Users are advised to take immediate specific action to contain the impact. Example: 'MSBlaster' worm outbreak. |
 |
A major disruption in connectivity is imminent or in progress. Examples: Code Red on its return, and SQL Slammer worm during its first half day |
 |
Loss of connectivity across a large part of the internet. |
Infocon Rubric
A score of 6 or greater moves Infocon up to Yellow, and 10 or greater moves us to Orange.
How we score the Infocon status:
- +2 Slammer-like impact on Internet wide operations
- +2 Remote arbitrary code execution
- +2 No vendor patch or effective mitigation is available
- +2 Active exploitation of vulnerability
- +1 Affects current version of up to date software
- +1 Affects widely deployed software
- +1 Relatively easy to exploit
- +1 Proof of concept code is available
- +1 Affects current version of up to date software
- +1 Affects a Microsoft OS or Adobe application
- +1 Wormable
- -1 Affects obscure or obsolete OS or application
- -1 Requires user intervention to run
- -1 IDS/IPS rules or other detective controls are available
- -1 Major anti-virus vendors can detect and clean malware
- -1 Mainstream media and everyone else has already covered issue
- -1 Vendor has released an advisory/bulletin/announcement (and decent workaround)
(Partial) Infocon History
This table summarizes past infocon changes. Not every single event is covered. (Eg. Code Red was our first event that caused us to go to 'Yellow' and later briefly to 'Orange')
| Date | Status | Reason |
|---|---|---|
| May 12th 2017 | Yellow | WannaCry Ransomware Worm |
| December 21st 2016 | Yellow | Juniper ScreenOS VPN Backdoor |
| April 16th 2015 | Yellow | MS15-034 IIS HTTP.sys DoS Vulnerability |
| Jan 23 2015 | Yellow | Adobe Flash Vulnerabilities |
| Sep 26 2014 | Yellow | Bash Shellshock |
| Apr 08 2014 | Yellow | OpenSSL Heartbleed |
| Mar 16 2012 | Yellow | MS12020 Windows RDP Vulnerability |
| Sep 28 2010 | Yellow | MS10070 |
| Jul 19 2010 | Yellow | LNK Vulnerability in Windows |
| Jul 13 2009 | Yellow | MS Office Web Components ActiveX |
| Oct 23 2008 | Yellow | Microsoft RPC Patch MS08067 |
| May 15 2008 | Yellow | Debian SSL Keys |
| Mar 31 2007 | Yellow | ANI Exploit |
| Mar 23-24 2006 | Yellow | createTextRange exploit |
| Dec 31st 2005-Jan 5th 2006 | Yellow | WMF flaw |
| Dec 27th 2005 | Yellow | WMF flaw |
| Nov 21-22 2005 | Yellow | Window() MSIE 0-day |
| Oct 19-20 2005 | Yellow | Snort Exploit |
| Aug 12-18 2005 | Yellow | PnP Bot/Worm (Zotob) |
| May 1-4 2004 | Yellow | Sasser Worm |
| Mar 20-22 2004 | Yellow | Witty Worm |
| Sep 10-12 2003 | Yellow | RPC exploit |
| Aug 11-15 2003 | Yellow | MSFT Blaster |
| Mar 17-20 2003 | Yellow | IIS WebDav Exploit |
| Jan 25-28 2003 | Yellow | SQL Slammer |
| Sep 19 2002 | Yellow | Slapper Worm |

