Scanning for Laravel - a PHP Framework for Web Artisants
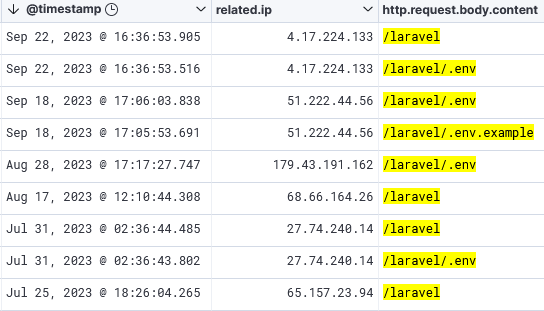
Today while reviewing my honeypot logs, I noticed an HTTP request for a directory this week I had not noticed before that included Laravel:
- /laravel
- /laravel/.env
- /laravel/.env.example
- /vendor/laravel/.env
- /vendor/.env
- /project/env.example
- /staging2.env.example
- /public/.env
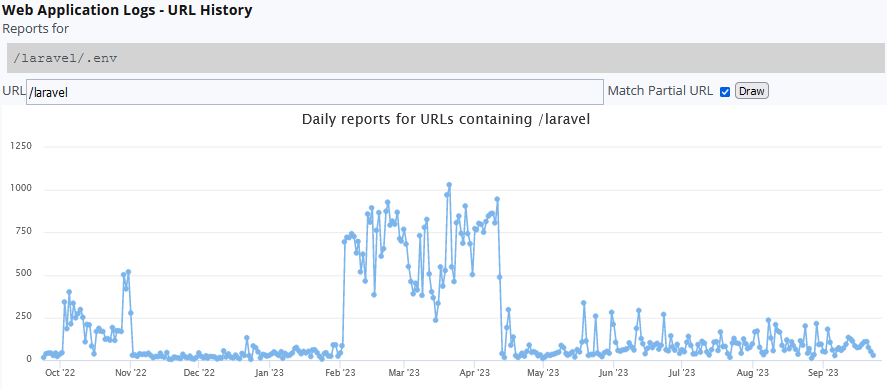
This is only a short list of directories these IPs were probing for. After a search across all the logs I have for the past year, the honeypot captured a few times this activity looking for this application. Checking ISC Web Application logs, scanning for Laravel peaked between February and mid April 2023. The last know exploit for this application was for CVE-2021-3129 for a Remote Code Execution (RCE).
Active scanning likely looking for any misconfigured applications.This is a list of the IPs captured in the past 3 months:
[1] https://laravel.com
[2] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-3129
[3] https://isc.sans.edu/ipinfo.html?ip=4.17.224.133
[4] https://isc.sans.edu/ipinfo.html?ip=51.222.44.56
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

Comments