F5 BigIP vulnerability exploitation followed by a backdoor implant attempt
While monitoring SANS Storm Center's honeypots today, I came across the second F5 BIGIP CVE-2020-5902 vulnerability exploitation followed by a backdoor deployment attempt. The first one was seen by Johannes yesterday [1].
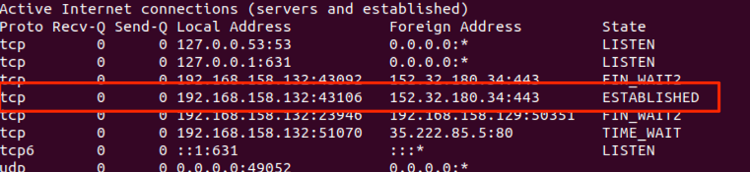
Running the backdoor binary (ELF) on a separate system, it was possible to verify that it establishes an SSL connection to the address web[.]vpnkerio.com (152[.]32.180.34:443).
Looking for the web[.]vpnkerio.com at VirusTotal while writing this diary, I could find no AV detecting the network addresses or the binary hash as malicious.
For persistence, it writes a line on "/etc/init.d/rc.local" file on an attempt to start on system boot.
Examining the binary statically, it is possible to see the string' python -c 'import pty;pty.spawn("/bin/sh")’. It will require more analysis, but it may be used for the attacker to have an interactive terminal on the target system. A proper terminal is usually required for the attacker to run commands like 'su'.
IOCs:
Exploitation attempt source
96[.]45.187.52
Backdoor URL:
http://104[.]238.140.239:8080/123
C2 communication
web[.]vpnkerio.com
152[.]32.180.34:443
The backdoor binary
90ce1320bd999c17abdf8975c92b08f7 (MD5)
a8acda5ddfc25e09e77bb6da87bfa157f204d38cf403e890d9608535c29870a0 (SHA256)
References
[1] https://isc.sans.edu/forums/diary/Summary+of+CVE20205902+F5+BIGIP+RCE+Vulnerability+Exploits/26316/
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter

Comments
Anonymous
Jul 7th 2020
3 years ago
The correct IP is 152[.]32.180.34.
Just fixed in the diary.
Thanks!
Anonymous
Jul 7th 2020
3 years ago